A few weeks ago I gave a guest lecture at the Windesheim University of Applied Sciences in The Netherlands. Being a Windesheim graduate myself I’ve always kept in touch with my former teachers. One of them told me recently that a lot of students want to learn more about IT security & hacking and invited me to give a guest lecture. Of course! And to keep it a bit juicy, I added a hacking demonstration to my lecture.
When I started the demonstration, I thought it would be fun to ask the students to name a company of which I would subsequently review the security. What I found out next was quite astonishing and I had to change the direction of the demonstration in order to protect the company’s security.
Hacking Unilever?
One of the students mentioned Unilever, a well known company in The Netherlands, so I thought it would be cool to review this particular company. Within the restrictions of the law, of course. I started analyzing the HTTP headers of the Unilever website and eventually I fired up Shodan.
Searching Shodan for Unilever results
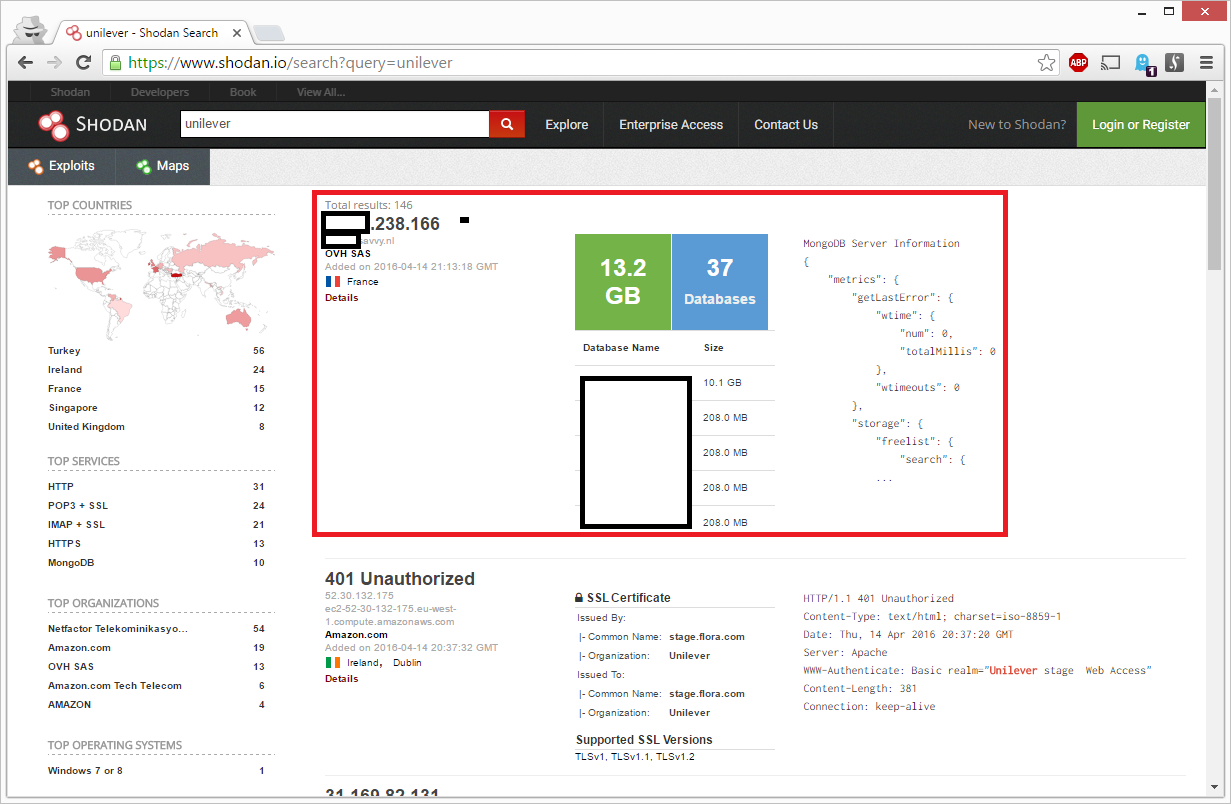
Shodan is a great search engine for hackers. It scans a large part of the internet and creates a digital map of all devices and services connected to it. I typed in ‘unilever’ and got several results. The first search result immediately got my attention:
Apparently there was an unprotected database attached to the internet with quite a lot of data in it (13.2 GB!). And somewhere in all that data the word ‘Unilever’ popped up. Oh my god! This hacking demonstration is really getting somewhere! I never expected to end up with this information! What exact content did Shodan index from that database?
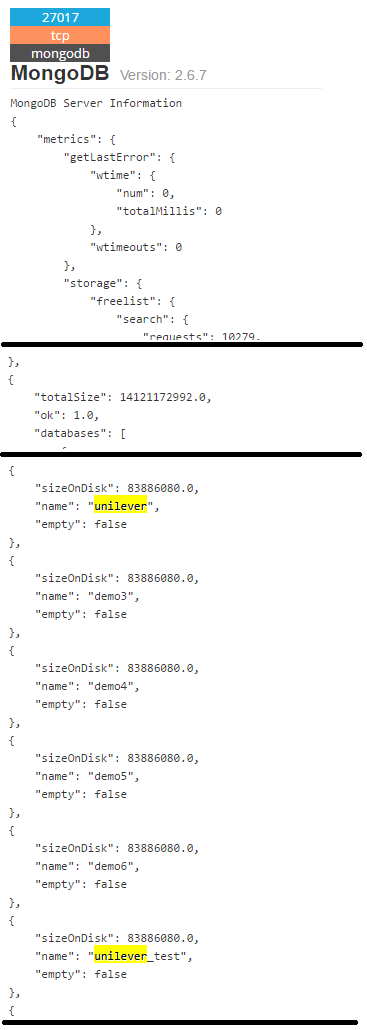
I clicked on the details button and Shodan showed me some more information:
It seemed this MongoDB database server contained at least two databases which were named unilever and unilever_test. I felt this could be really dicey and decided to cut off the Unilever hacking demonstration. Never teach your students too much! 😉
Aftermath: should I report the security hole?
It is two weeks later now and somehow it didn’t feel right to just leave this database unprotected while attached to the internet. Unilever is probably not even aware of the fact that their complete database server has no password configured. I should actually help them to fix this security loophole. So I started digging into it to assess the situation.
Connecting to the database
The database server runs on MongoDB and to validate Shodan’s findings I needed to get software that could connect to a MongoDB server. I hadn’t installed a MongoDB client so I googled on ‘mongodb client‘. The fourth result lead me to a client called MongoVue which I installed and opened. I pressed the connect button:
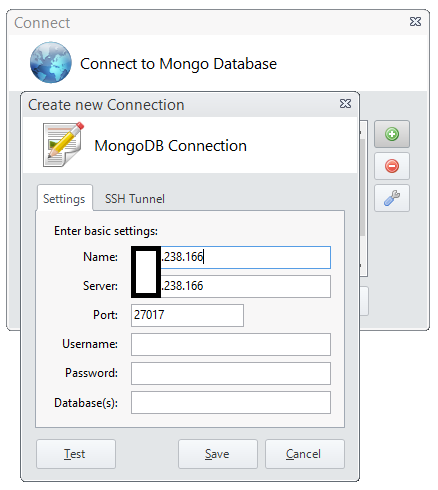
Then I filled in the IP address that Shodan gave to me:
And then I hit the save button. On the next screen I just hit the connect button to see what would happen:
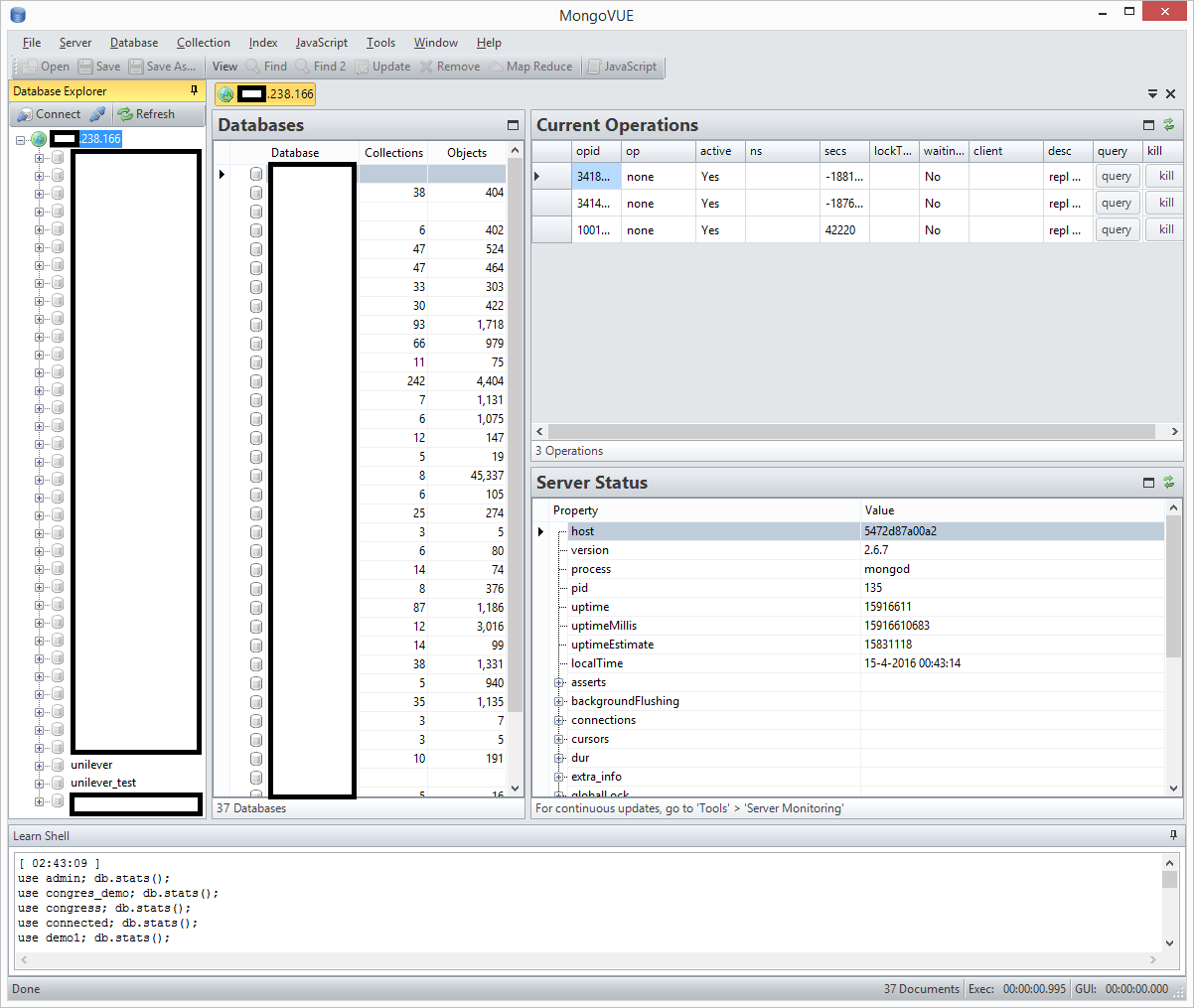
It looked as if I had now unrestricted access to 37 databases within this server!
Holy shit!
It looked as if Unilever wasn’t the only company affected by this security loophole. This was much bigger! I needed to find out who to contact exactly to get this matter solved, so I clicked around in the database tables to find out more. The database had no user name and password configured to protect it so I assumed it was a public database 😉
Within the databases I found personal details like names, e-mail addresses and also private chat logs. I didn’t count how much data was leaking exactly. But this information shouldn’t be unprotected and on the internet at all! It appeared the database server had something to do with multiple conference presentations. Unfortunately at first glance I couldn’t find more clues as to whom this database belonged to.
Side note: in above screenshot you can see that MongoDB version 2.6.7 is installed. This is an outdated version and contains a medium denial-of-service security risk.
Back to Shodan
Unilever isn’t the company to report this issue to since they’re merely a victim. So I got back to Shodan to see if there was more information available about the vulnerable server:
Quick look at the MySQL server
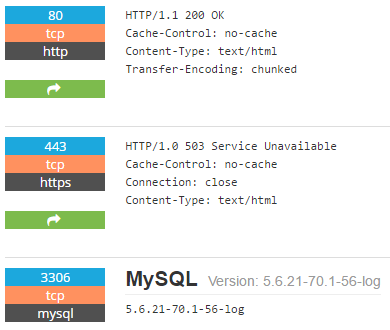
It looked as if another database server (MySQL) was publicly accessible from the internet. It was unclear if it had a password configured. Nonetheless, it’s bad security practice to have a database server directly accessible via the internet.
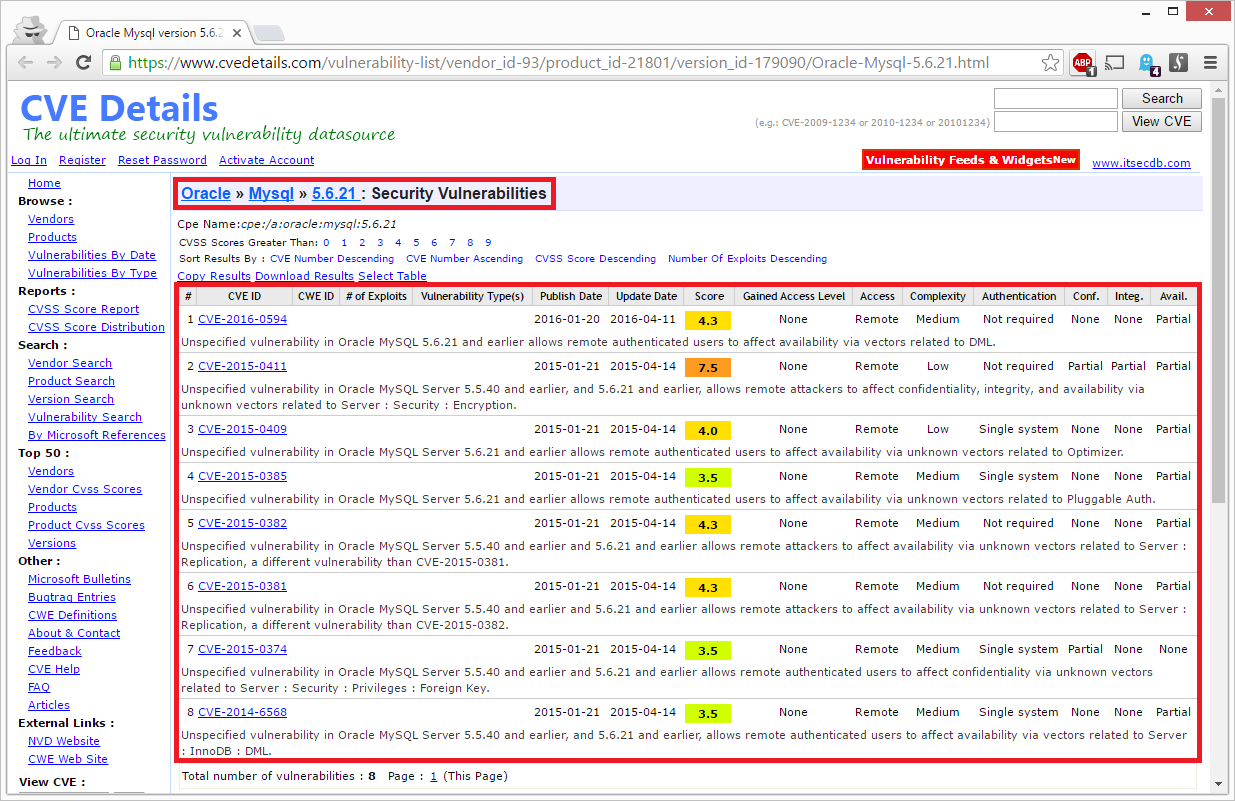
When giving the MySQL version number (5.6.21) a closer look I noted that it contained various security vulnerabilities:
One of the vulnerabilities even got a CVSS rating of 7.5! This means it’s a high security risk that should be patched immediately. I didn’t extend my research into the MySQL server as I was looking for the server owner.
Visiting the accompanying server website
I left that particular database server and visited the attached website (which the server broadcasts on TCP port 80):
Apparently highly technical data about the status of the (proxy) server is publicly available. From a security standpoint this sort of confidential information should never be published.
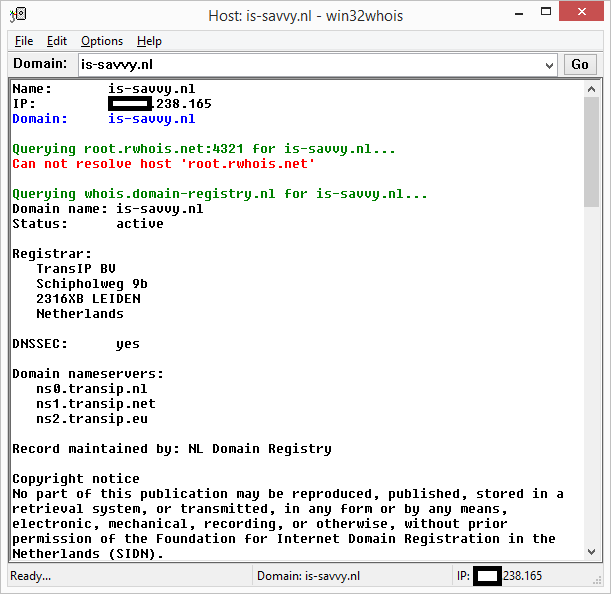
Retrieving domain name ownership information
I saw the domain name [removed].is-savvy.nl in above results and thought this would be a good starting point for finding the owner information for that domain name (via whois):
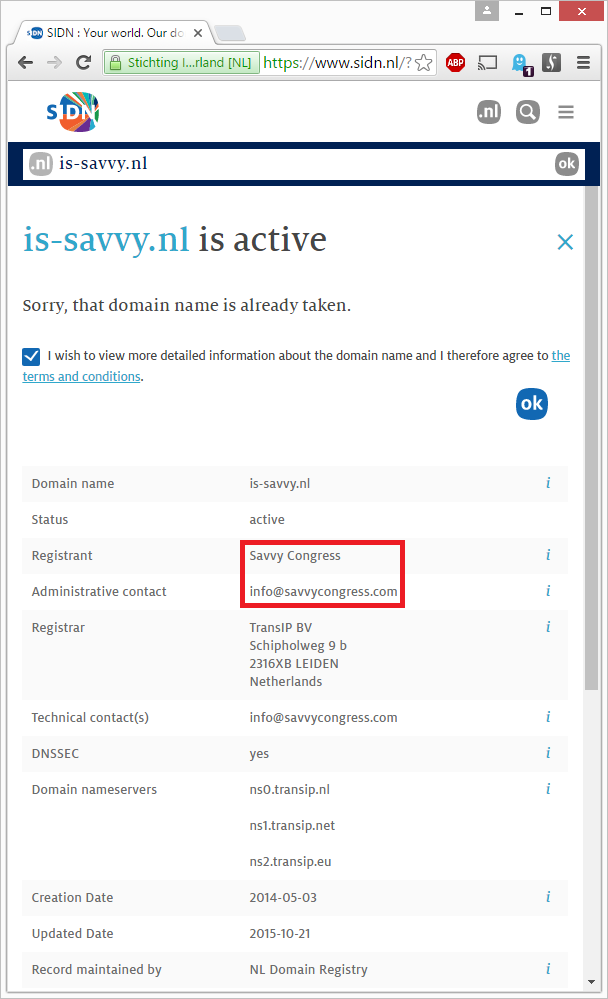
Above information didn’t get me much further. Since for domain names that end with .nl, further detailed information can only be requested by visiting the SIDN website. SIDN maintains the administration of .nl domain names. And this is their record about is-savvy.nl:
Ah, now we’re getting somewhere! The owner is Savvy Congress.
Visiting the Savvy Congress website
I visited their website and immediately noticed they develop software that can be used during a congress. To chat with the audience for example:
That makes sense. I noticed chat logs and pointers to congresses so I was fairly sure their software used MongoDB as a database server.
Searching Shodan for more vulnerable database servers
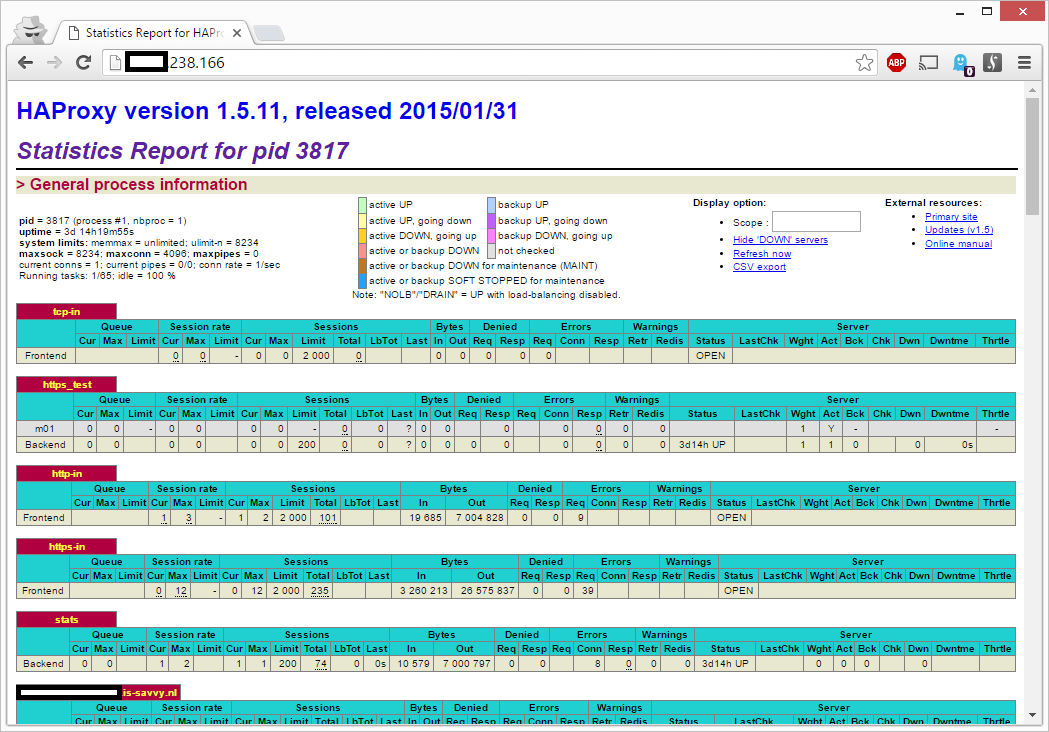
I was curious to see if Savvy Congress had more vulnerable MongoDB servers and searched Shodan for savvy. From the results I extracted the following information:
| IP address | Size | Databases |
| x.x.238.161 | 13.1 GB | 36 |
| x.x.238.162 | 11.1 GB | 33 |
| x.x.238.163 | 23.1 GB | 35 |
| x.x.238.164 | 13.1 GB | 36 |
| x.x.238.165 | 13.2 GB | 37 |
| x.x.238.166 | 13.2 GB | 37 |
| x.x.238.167 | 13.1 GB | 36 |
| x.x.238.168 | 13.1 GB | 36 |
| x.x.238.169 | 13.1 GB | 36 |
| x.x.238.170 | 13.1 GB | 36 |
| x.x.238.171 | 11.1 GB | 33 |
| x.x.148.216 | 9.8 MB | 2 |
| x.x.43.136 | 6.6 GB | 10 |
None of these 13 databases (156.6 GB total) had a password configured and were freely accessible. 11 databases were within the same IP range (x.x.238.*) and had an incremental IP address.
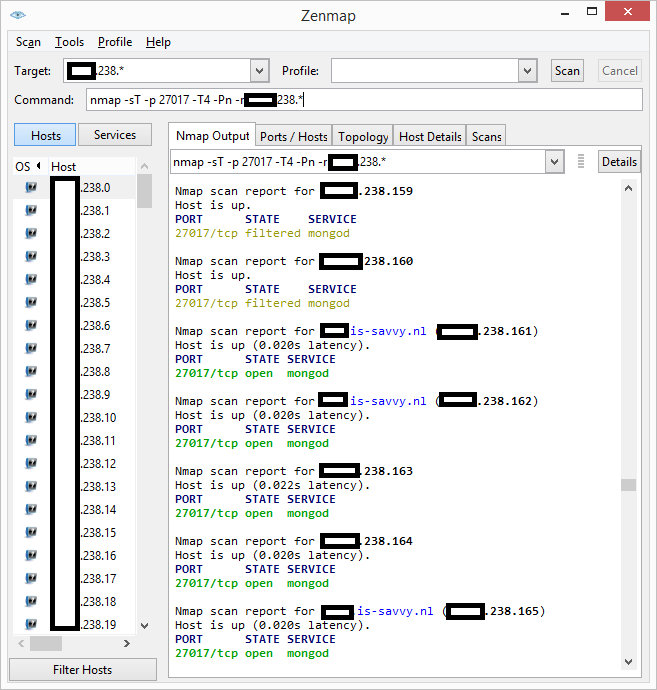
Firing up Nmap
I didn’t know if Shodan was extensive in their effort in indexing services on the internet so I performed a quick port scan via Nmap to see if I could find more MongoDB servers in the IP range that had 11 vulnerable servers:
Luckily I couldn’t find any more servers so Shodan must have done a pretty good job indexing them 🙂
Contacting Savvy Congress
Since I now knew which database servers were unprotected and also what the security impact was – it was time to contact the owner to communicate the gathered intelligence. On April 15th, 2016 I called Savvy Congress twice but unfortunately was ‘firewalled’ by the reception on both occasions. So I mailed them my findings.
The next day I got a friendly reply in which they stated that these servers were indeed open but that they were part of an old development cluster. They also sent me a nice t-shirt to show me their appreciation of the responsible disclosure:
If the vulnerable servers were indeed development machines then the production data I saw was probably copied into development databases. Not a smart move as these environments are almost always less secure than production systems.
Finally, the last two IP addresses (x.x.148.216 and x.x.43.136) which hosted insecure MongoDB databases did not belong to Savvy Congress.
Finding the other owners
I found out that the 6.6 GB database at x.x.43.136 belonged to Droisys. According to LinkedIn they have between 246 and 500 employees and operate in the financial sector. The database is probably used for transactions and prices. Not really sure what it does exactly. I had found several Droisys e-mail addresses in the database and decided to use these to notify them that their database was exposed on the internet. Unfortunately I haven’t received any reply from them yet. Since I didn’t get e-mail bouncers the e-mail addresses I mailed to should still exist. Did Droisys ignore me?
Final words
Companies which don’t scan their internet infrastructure for security vulnerabilities don’t realize how vulnerable they can be. As I unfortunately notice too often in my work.
You can only hope for them to be contacted by a friendly hacker who invests time and effort in their security situation and notifies them of their vulnerabilities before a cyber criminal comes by.
Also, if you use MongoDB databases, please use a strong password and put it behind a firewall 😉 Thanks!
Timeline of notable events
| March 30, 2016 | Gave college lecture at Windesheim |
| April 15, 2016 | Disclosed security vulnerabilities to Savvy Congress. |
| April 16, 2016 | Savvy Congress acknowledges my findings. |
| April 25, 2016 | Validated that Savvy Congress secured their MongoDB servers and notified Droisys of their vulnerable database. |
| May 13, 2016 | This article is published. |
Sites linking to this article:
- NOS.nl
- Softpedia.com
- Sisteminformasi.biz
- Hacker News
- Silicon.fr
- Reddit.com
- OpenQuery.com.au
- Secaholic.com
This article has been manually translated into Japanese by IT news site POSTD.cc.



Unilever is a pretty evil company, judging alone by their activities in Southeast Asia. Why are you all, “omg, they should be protected!” Perhaps as an Ethical Hacker, you could stand to pause and consider longer the ethical implications of being a knee-jerk handmaiden to Unilever. I don’t mean to dismiss the rest of what’s at stake in your writeup, and I would commend you for finding and reporting the vulnerability, but the whole “must… protect… Unilever” thing is one kernel of bother I had with this. Ethical Hacker ≠one who operates completely within the bounds of law, if the law itself is not bound up in a rigorous ethics.
tldr: you are cool; I have a mild problem with your logic; Unilever can suck it.
You’re right that there are plenty of open databases online. That’s shocking, right? This needs more awareness! I think it’s unacceptable that we as a society can’t protect our information well enough. We can only fix the problem by telling stories about it and raise awareness.
Ethical Hacker means EXACTLY that you operate within the bounds of the law. You’re thinking of a ‘gray hat’ hacker, bro.
What if the law itself is unethical?
Unfortunately it isn’t our jobs to decide what is ethical and what isn’t.
It’s our governments!
You’re wrong. It’s the governments job to decide the law. The law does not necessary have something to do with ethics. When you have a good government, the laws will coincide with what most of the population views as moral. However, that’s not always the case.
Laws can in principal be very immoral.
Remember there were laws in the third reich too. Would you also cosider killing jews ethical if your government tells you to. Towards me it seems like you missed out a lot in 7th grade history (Maybe you never got that far idk)
This is sarcasm, right?
Deciding what is ethical and what isn’t is absolutely your responsibility, and something that should be as far removed from government as possible.
truth
He’s not a college student though, he stated that he was the one giving the lecture and that he kept contact with his teachers after graduating.
So just because they’re a sketchy company means that their data shouldn’t be protected? It’s not like this is whistleblowing conspiracy-level information that needs to be broadcasted to the world; this could have easily been a different scenario where customer data was exposed. The content of this article shouldn’t change even if you swap out “Unilever” for any other company name.
Two wrongs don’t make a right. Part of being an ethical hacker is being universally ethical. The data exposed here wouldn’t just hurt Unilever, it would hurt all of the people whose data is contained within said databases. Also, it’s not even Unilever’s, it’s Savvy’s, and they have multiple clients and potentially hundreds of individuals that could be harmed by this.
The ethics here are not around whether Unilever is a good or evil company, but about the client info that their leaking database would make available. It would be wrong to assume that because you dislike Unilever that you should open their client information to abuse.
That is the ethical point to this article, it’s about the people who’s data was involved, not the company that made the mess.
Why would you send random employees from the company (Droisys) whose database is exposed emails? They were probably not sysadmins, so what’s the point. Just contact them directly, their website has enough information.
My guess is that these random employees build the MongoDB. I’ve contacted them twice. Last time I’ve also sent my mail to the main e-mail address of the company. Unfortunately no response so far.
> Since I didn’t get e-mail bouncers the e-mail addresses I mailed to should still exist. Did Droisys ignore me?
You’re a “hacker” and don’t know that e-mail bouncers have been turned off for a long time now to prevent spammers from checking for valid emails?
Almost every company I know sends mail bouncers when an invalid e-mail address is used. Those that don’t have that setting have a catch-all mail box configured in my experience.
Wow, so this is what college students consider hacking now… punch an IP into shodan and using their data?
There’s a bit of useless info in this report (eg; why do you need to explain how to connect to a mongodb?) but not bad for your first article on the matter.
This article needs more linux 😉
I wrote the article for non technical people, just to show how easy it can be to hack into a system. You are obviously very elite, so you might skip the install MongoVue part 😉
You’re cringy as fuck.
Stop being so elitist and get a life.
Nice article. But is this really the level of our universities?
Any enthousiast can do this at a young age.
That’s exactly my point, that anybody could perform this ‘hack’. It’s not complicated. Didn’t even expected to find anything.
you didn’t ‘hack’ anything…you used a public dataset to expose a poorly secured supposedly ‘dev’ only non-production set of data…
It’s not really hacking indeed. There was no security in place.
Good read from @sruwhof: http://sijmen.ruwhof.net/weblog/%5B..] Cold sweat: https://www.shodan.io/search?query=MongoDB+Server+Information
@fullung @sruwhof remember? Nosql = noauthentication eheheh
It’s so funny how everyone is so l33t and hating on this article. Give me a break. 90% of the people hating on this article don’t even have a background in computer science. Probably ITT tech drop outs doing technical support somewhere.
*insert thank-you.gif*
Sijmen,
I really appreciate your efforts in writing this article. That was very informative for a student like me who has just stepped into the field of vulnerability assessment.
Thanks a lot.
This guy orange is acting like asshole and talking about maturity bc
Good article. Just ignore the haters.
– Someone who actually matters
Great write-up that shows just how easy it is to find vulnerable servers. This is something every company should do from time to time to make sure they’re not sitting wide open, especially when trusting a third party to manage your information.
I wouldn’t call this ‘hacking’ per se, but the point was clearly made.
The nay-sayers are missing a few key points:
1. Ethical hacking has just as much to do with the moral compass of the person using the tools than the technical prowess of whatever tool.
2. In all learning, there are beginners and those who know more. Wisdom is understanding that no one will possess all the knowledge in a field. Any teacher will tell you that they learn as much from their students as the students do from the texts.
3. Be kind and pay it forward. I’ve been in IT for 25+ years and much of that was spent asking questions of those who knew more than me. As a result, I am happy to help someone else learn what I know, as a way to repay & remember the help that I was given.
4. Last, how different would your comments be if the name of the company was left out entirely? As a classroom exercise, the object is to learn and understand the ethical responses to what the tools or data show.
Your own moral compass determines whether you respond to protect the client company or instead release the data to the world in the name of social justice.
Sijmen,
If they didn’t respond and there’s personal data in those database, https://autoriteitpersoonsgegevens.nl/ would very much like to know about it.
Great article thanks. As somebody who is not super cool and l33t like some other posters, it really opened my eyes as to how trivial it is to look for vulnerable databases. Going to check my company now
Finds financial transactions, drools over couple of email addresses. Lol
Sorry if i misinterpreted.
Fuck all the haters in the comments. It’s a nice article and made me giggle. Author didn’t mention “I’m hacking their servers I’m such a l335 h4x0r!”, he just found the data and then all the frustrated basement dwellers crawled out of the woodwork to puff their chest and point out what “real hacking” is…puh-lease!
Dear Sijmen,
On behalf of Savvy Congress we would like to comment on your findings.
First of all, you’re right OUR database (Unilever has no link to this issue) was not properly secured. As we emailed you already on the 16th of April, we are thankful that you found this and reported this to us. We fixed the vulnerability right away and notified the proper authorities.
To clarify about our product and our online database please consider the following.
It was a database to use for our online product development. During the development period we set-up a couple of pilot projects for different clients and different purposes.
One of those pilots was called “unileverâ€. The database for this pilot saved up a total of 13.2GB, but consisted only a mere 840MB (mostly application cache). Mongo uses more space than it actually stores, so that it can later save data more efficient. The 11 databases you found was actually just one database, spread over 3 servers in a cluster. Nine IPs leading to the same server.
The Pilot we’ve run was a public webinar, everybody could log-on with an e-mail address and watch the webinar. We also provided a questions&answer option to “chat†with the presenter of the webinar.
In total there where not more than 200 viewers during this particular pilot.
So yes you’re right in your conclusion; please be aware with mongo databases and always firewall them!
As promised your T-shirt is on it’s way.
Again thank you for your findings and informing us about it.
Kind regards,
D. Eijpe,
CTO
Savvy Congress
Sijmen,
It’s good to see at least someone is trying to spread security awareness in the world. That’s the point eventually, right? Although it is not really “hacking”, it is still a good find. I appreciate you are spreading the awareness. Just ignore the people in the comments who think they are pro hackers, they don’t seem to understand what security is. Security is more than (for example) protecting a network or protecting whatever you want, it’s also about implementing the right processes and awareness within an organisation (and much more).
People can continue looking for the advanced hacks, but why would you do that if a large part of the world is not even ready to secure a basic database? (unless you’re a grey/black hat).
You sir, are a real Security Consultant/Ethical hacker.
All the best,
Rick
Thanks Rick! 🙂
l33t? Had to look that up. Why not just write “elite” so everyone can understand what you mean.
He had to write ‘l33t’ because that’s how adolescents do it. 🙂
Great article. I’d say it accomplishes its purpose in calling people’s attention to the issue and reminding them to be sure their own data is as secure as they hope it is.
I am a bit surprised (actually, not much) at all the hate and the fact that, in spite of apparently being super-l33t, some folks still have to take the time to post a comment trying to prove that they know more by pointing out how super easy all this was. I don’t think the author ever tried to claim that it was hard. If anything, the fact that it was so easy to discover and access is what he was calling attention to.
For those of you who actually have amazing hacking skills, write up an article explaining it. I’d love to read it.
You gain far more respect by doing something yourself than bashing other people’s work.