On January 2, 2018 I visited MediaMarkt in Leidsche Rein The Wall. MediaMarkt is a well-known electronics shop franchise in The Netherlands with 45 stores. I was in need of a new phone as my current one was now over two years old and my subscription ended. They had the Samsung Note I was looking for, so I came there to get it.
The sales guy from the telecom department happy greeted me and started a conversation. He wanted to check out my phone subscription to see if he could get a nice discount for me. Sure!
Sales desk
I was standing at the telecom service & sales desk, located in the middle of the MediaMarkt store. It is designed in such a way, that customers can easily look at the four monitors used by the employees in this in-store sales and service point. Customers are invited to read offers and information on the screen. No effort is made to block your view on the monitor of the service computer.
TL;DR (in Dutch): NOS News reports about the password gate
I’ve worked together with the research redaction of NOS News to investigate this story. They also wrote about this incident and talked about it in their news bulletin on Dutch national Tv:
I was invited by NOS Radio 1 Journal to talk about this story in their news bulletin:
Flash back: 2 years ago
And now I remembered the epic situation again from two years ago. In September 2015 I also bought a new phone in a MediaMarkt shop in Utrecht. During my visit, they had their password file open for quite some time while I was standing next to the sales guy when he was helping me. I photographed it as proof:

The password file that I photographed in September 2015.
Access to data from 10 to 14 million people
I did some further research back then and got to know that MediaMarkt is a dealer for all telecom operators in The Netherlands. This includes KPN, T-Mobile, Tele2, Telfort, Vodafone, Ziggo and others. MediaMarkt, via dealerships, has access to personal data of basically all Dutch citizens who own a mobile phone. That would be somewhere between 10 and 14 million people.
I figured out that back then 11 from the 20 web portals they used where internet-facing. If I would, I could easily access that data with the passwords that I photographed! That would be of course illegal and unethical.
Responsible disclosure
Instead I reported this critical security leak to MediaMarkt. They said they fixed it. I wrote about it on my weblog. That story went viral and MediaMarkt had to publish an official statement about the incident on their site and promised to never let this happen again.
Here I stand again
Now I stand here again in 2018. I almost forgot about it. My sales guy walks me to his service computer to have a look at my phone subscription. I stand next to him and see that there’s a tab named ‘dealersheet’ in Internet Explorer. My hearth rate increases rapidly. This is the same name as the password sheet I saw in 2015! This can’t be true!
The Dealersheet
He asks me which provider I use. I told him that. He now needs to login to the dealer portal of that phone company. He didn’t remember the password, and, here it comes, he clicked on the ‘dealersheet’ tab! On the screen an Excel file opened which contained *all* their passwords visible again. I grabbed a snapshot of the sheet as proof:
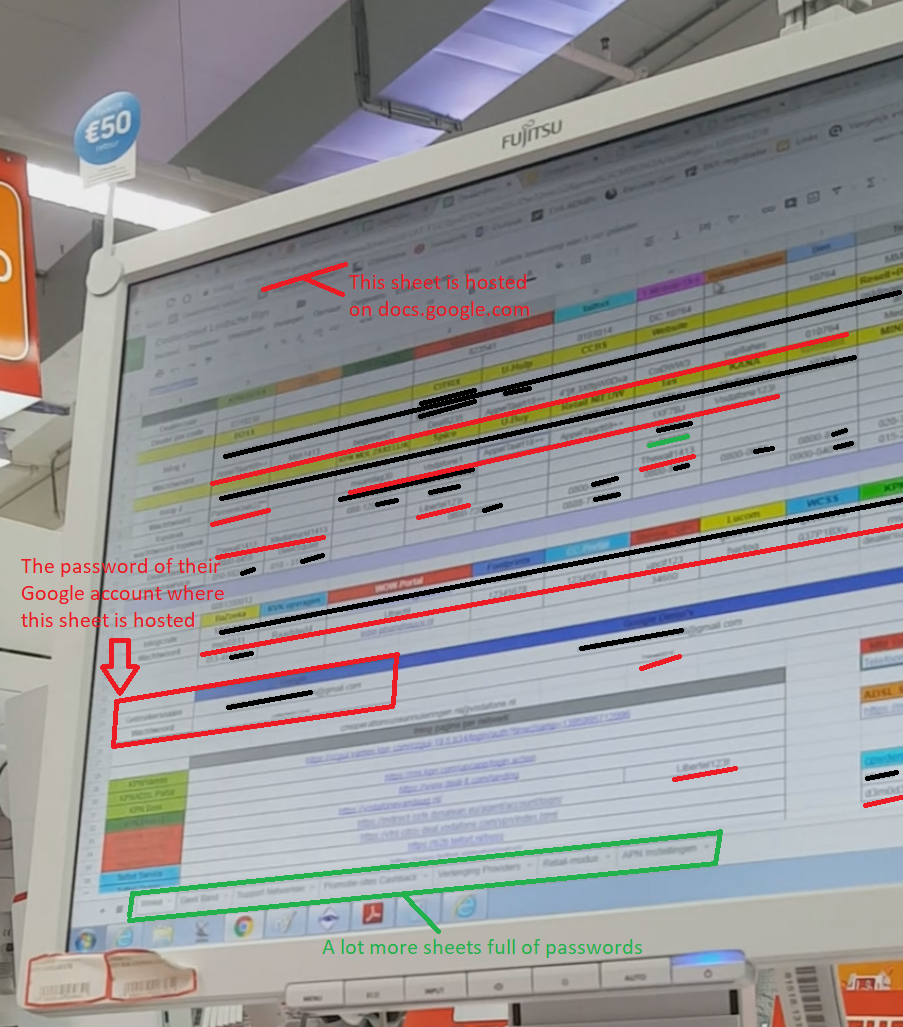
All red shaded passwords in above screenshot are changed by now. I’ve removed user names and phone numbers with a black marker.
Password sheet visible in the background
The sales guy takes his time and copies the password. He ALT + TABs to the login screen and pasted the password. He then continues working in the window he opened on top of the password file to look at my subscription and customer information:
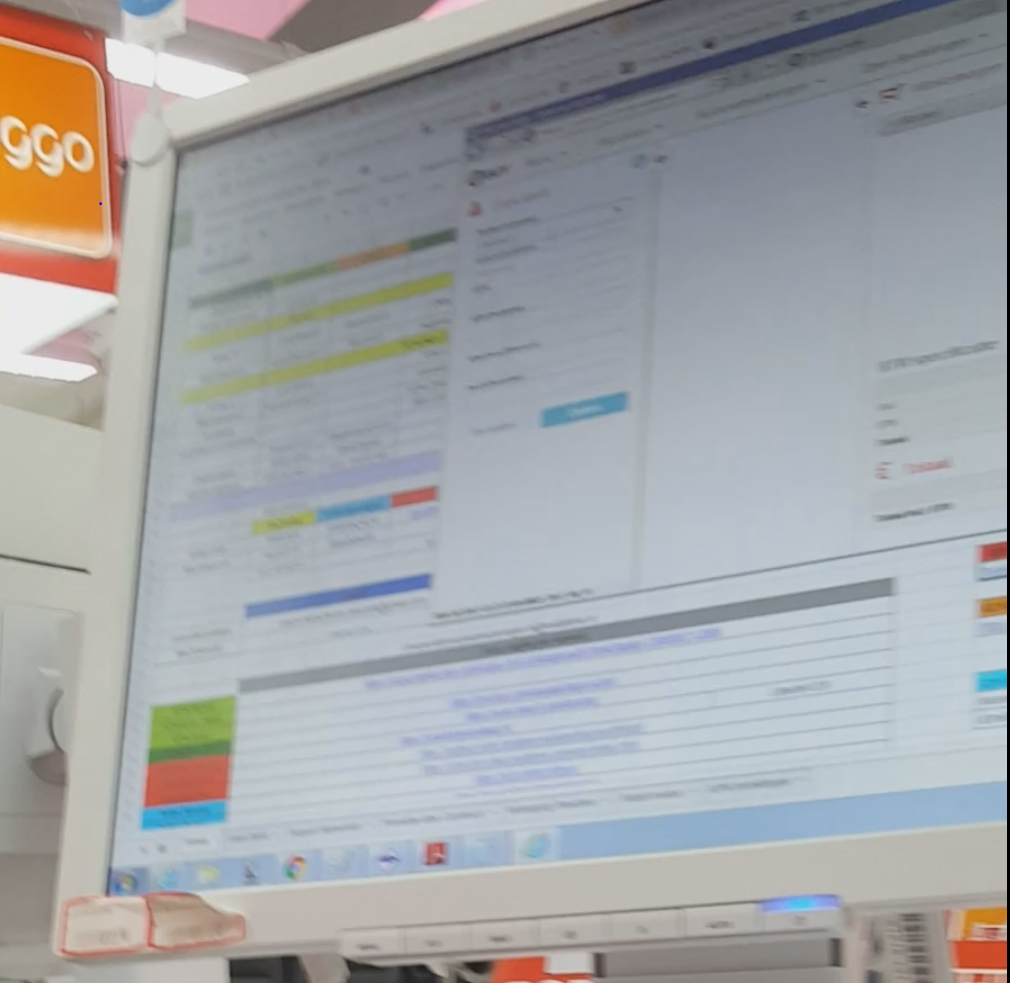
After 45 seconds he realizes that half the password sheet is still visible the whole time he was checking out my record while I stood next to him. He then silently maximizes the window so it now covers the whole password sheet. To late! Haha! I already took a picture of it.
I bought the phone and left the store. Outside I stood still. I was baffled. What had just happened?
Back to September 2015
In 2015 all 45 MediaMarkt locations in The Netherlands had received detailed new security policy regarding storing and protecting passwords. They had to implement privacy screens, the KeePass password database and use stronger passwords. This was shortly after the password gate incident two years ago, that led to quite some media attention. So you would assume that they would take this new security policy seriously, right?
Apparently not all the individual shop owners of the MediaMarkt franchise thought it was important enough to protect the telecom password database and literally did nothing. Nobody checked if all shops complied with the new security policy. And so the MediaMarkt password gate happened again in 2018.
Password file hosted on Google Docs
The password Excel file is hosted in the cloud at Google Docs. The username and password for this account was also visible in the sheet. If I would, I could just download the latest password file by logging into their Google Account!
Internet-facing dealer portals
The visible passwords in my photograph can be used in internet-facing portals of telecom providers. I could find some of them via Google. It looks like a username and password is all that is needed to login at the:
- Ziggo dealerportal
- Tele2 Partnerweb
- Tele2 Partnerzone
- Tele2 Reseller Portal
- Vodafone Partner Portal
- Vodafone Distributie support
- Vodafone points
- KPN Deal IT
- Telfort resellertool
- Youfone Dealerportal
- Bazoeka partner portal
I could use the easy to use Tor Browser Bundle in order to masquerade my IP address. That way I could perform the unauthorized access completely anonymous if I wanted, leaving no traces. That ‘crime’ would be hard to solve.
Circumventing IP address restriction
The portals that have IP address range restriction set-up, can easily be defeated by covertly installing a LAN Turtle or mobile broadband enabled WiFi Pineapple in one of the MediaMarkt shops, so remote access is gained to their internal network and thus the IP address restriction can be circumvented.
Finding a network cable or socket to attach the remote access device to is fairly simple, as MediaMarkt is an electronics shop, and customers have easy access to all kinds of occasional unmanned support desks which are located everywhere in the shop. I had quickly located several vulnerable spots.
Weak passwords
The password sheet contains some very weak passwords, such as 12345678, Utrecht, hertog and Vodafone1. It seems that only non personal user accounts are used to access dealer portals. This way it’s very hard to attribute fraudulent actions made with an user account if every employee in the department uses the same account. This illustrates the lack of security awareness here nicely.
Computers are never locked
What I noticed as well, was that every time the two telecom sales employees who manned the service point, left their computers, they never lock them (with Windows key + L). So people walking by in the shop have full and easy access to it. I saw the ‘dealership’ tab open on both computers. The sales guys seem to want to have easy access to it. They just have to press CTRL + TAB to re-activate it. And so could any malicious person walking by.
The two computers had easy-to-reach USB ports. I could perform a USB drive-by attack with a prepared Rubber Ducky or Teensy, with which I could have gained remote access to the computer within seconds.
Impact of leak
My personal estimation is that MediaMarkt, via dealerships, has access to personal data of basically all Dutch citizens who own a mobile phone. That would be somewhere between 10 and 14 million people.
Some of the dealer portals only display customer details after specific information about that person is supplied, such as a telephone number and corresponding birth date. This prevents the mass downloading of data, which is a good thing.
Nonetheless, even individual access to personal data such as full name, home address, postal code, city and phone subscription details is a goldmine for cyber criminals and intelligence agencies. With this password database in hand you could easily performing identity theft and trace individuals and VIPs. Stalkers and fraudsters would love to have direct internet access to such a treasure trove of personal data. The telephone subscriptions of customers can be viewed and changed via these portals. New orders can be entered into the system.
So it’s of the utmost importance that passwords that give acces to these dealer portals are protected very well!
What to do next?
What should I do? I could call MediaMarkt and point them to my weblog article from 2015. I’m sure that they’ll fix the password hole in that specific shop. But what about the other 40+ MediaMarkt shops? They had their chance in 2015 to fix it.
Outsourcing the responsible disclosure
So I called tech investigative journalist Joost Schellevis from NOS News. I told him about what I just witnessed. He validated my story and contacted MediaMarkt. They exchanged messages and replied to him after a week with an update:
“In your e-mail, you informed us that Sijmen Ruwhof has again found similar shortcomings at a MediaMarkt store. We immediately investigated this. MediaMarkt currently has no indications that it has been misused. However, MediaMarkt takes this very seriously. We therefore immediately took the following additional measures:
– the passwords at the relevant store and all other stores have changed;
– the password policy has been tightened;
– employees are once again pointed out that customers should not be able to look at passwords;
– password manager program usage has been tightened;
– compliance with safety protocol has been tightened. Here we describe for employees which safety and security measures we use within MediaMarkt.In addition, we contacted all telecom providers and informed them.”
Good to hear that they immediately took action!
All telecom providers notified
They were legally complied to inform all telecom providers about this incident and that a possible data breach might have occurred in the past. Since January 1, 2016 this duty to report is mandatory for Dutch companies because of new legislation.
A few days after the update from MediaMarkt I received a call from the chief security officer (CISO) of KPN. She wanted more information. MediaMarkt didn’t share any technical details with them. It was a friendly call and I told her what I knew and mailed the KPN security team (CERT) more information.
KPN adds 2FA on their portal
I saw that the KPN Deal-IT dealer portal displayed the following news message on January 15, 2018:
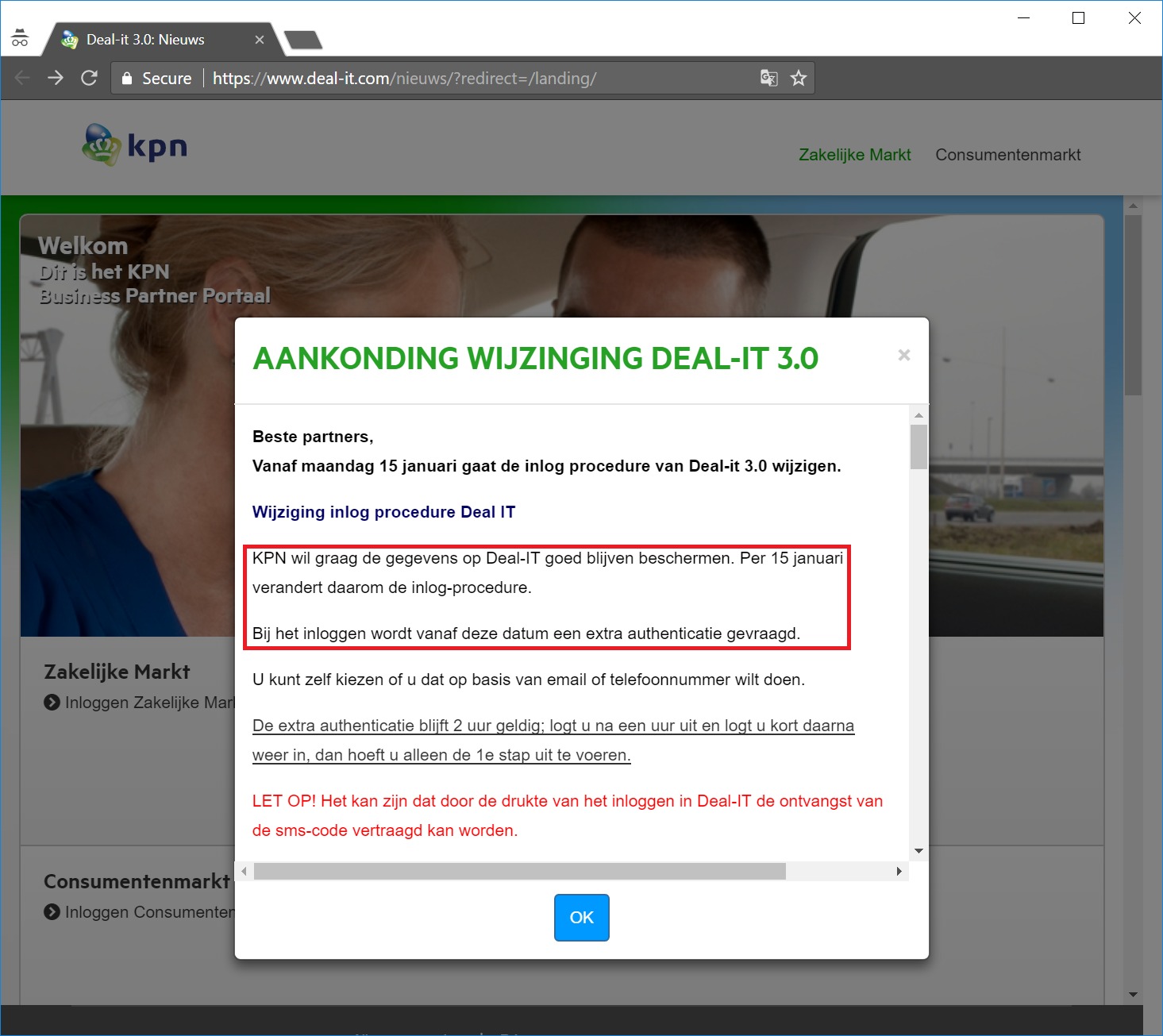
The red marked text translated to English:
“KPN would like to continue to protect the data on Deal-IT. The login procedure will therefore change on 15 January. When logging in, an additional authentication is requested from this date. You can choose whether you want to do this by email or telephone number.”
They activated two-factor authentication on their telecom dealer portal. Good! With an username and password alone no access is possible anymore.
Rounding up!
Hopefully this MediaMarkt telecom password gate is now for once and all closed!
NOS News reports about the password gate
I’ve worked together with the research redaction of NOS News to investigate this story. They also wrote about this incident and talked about it in their news bulletin on Dutch national Tv:
I was invited by NOS Radio 1 Journal to talk about this story in their news bulletin:
Sites that link to this article
- NOS.nl: ‘MediaMarkt gaat nog steeds slordig om met wachtwoorden’
- NOS.nl: ‘Wekdienst 26/1’
- NPOradio 1: ‘MediaMarkt gaat nog steeds slordig om met wachtwoorden’
- Tweakers.net: ‘Providers voeren beveiliging dealerportals op na melding over MediaMarkt’
- Nu.nl: ‘Persoonsgegevens in winkels MediaMarkt slecht beveiligd’
- RTVUtrecht.nl: ‘MediaMarkt Leidsche Rijn in de fout: persoonsgegevens miljoenen Nederlanders openbaar’
- HartVanNederland.nl: ‘Persoonsgegevens miljoenen klanten MediaMarkt slecht beveiligd’
- Radar.AVROTROS.nl: ‘MediaMarkt nog steeds slordig met wachtwoorden’
- Security.nl: ‘MediaMarkt weer de fout in met wachtwoorden dealerportaal’
- DUIC.nl: ‘Persoonsgegevens klanten gemakkelijk te bekijken via MediaMarkt Leidsche Rijn’
- RetailTrends.nl: ‘MediaMarkt in opspraak om wachtwoorden en prijsverhoging’
- Leidsche-Rijn.Nieuws.nl: ‘MediaMarkt in The Wall gaat te slordig om met persoonsgegevens’
- DMCC.nl: ‘Persoonsgegevens in winkels MediaMarkt slecht beveiligd’
- Pit-recht.nl: ‘MediaMarkt gaat nog steeds slordig om met wachtwoorden’
- Cqure.nl: ‘Password database of MediaMarkt leaks again’
- Nasze-Radio.nl: ‘Media Markt w dalszym ciągu nie chroni właściwie danych osobowych swoich klientów’

Pingback: MediaMarkt in The Wall gaat te slordig om met persoonsgegevens - Leidsche-Rijn