In today’s episode of the insecure internet I present you the company Ticketscript. This event ticketing company provides tools and features to make selling tickets for events easier. According to their website:
“[..] Ticket buyers are your biggest asset. Why share your customers with anyone else? Stop sending your hard earned traffic to third party ticket selling websites and agents. [..] The secret to event success? Own your data 100%. [..]”
Well, it appears that their data got owned!
Let me tell you a story.
I came in contact with the crew of Dutch television show Opgelicht?! from AVROTROS and they wanted to make a special item about cybercrime and data breaches. They asked me if I had found a critical vulnerability in a Dutch company recently what hasn’t been reported yet. I stumble across these every week during my professional engagements, but all of them fall under non-disclosure agreements. I told them I could easy find a new one for them. They said that if that was true, that would be a good news story to tell: to inform and create awareness among their viewers about the dangers of the internet.
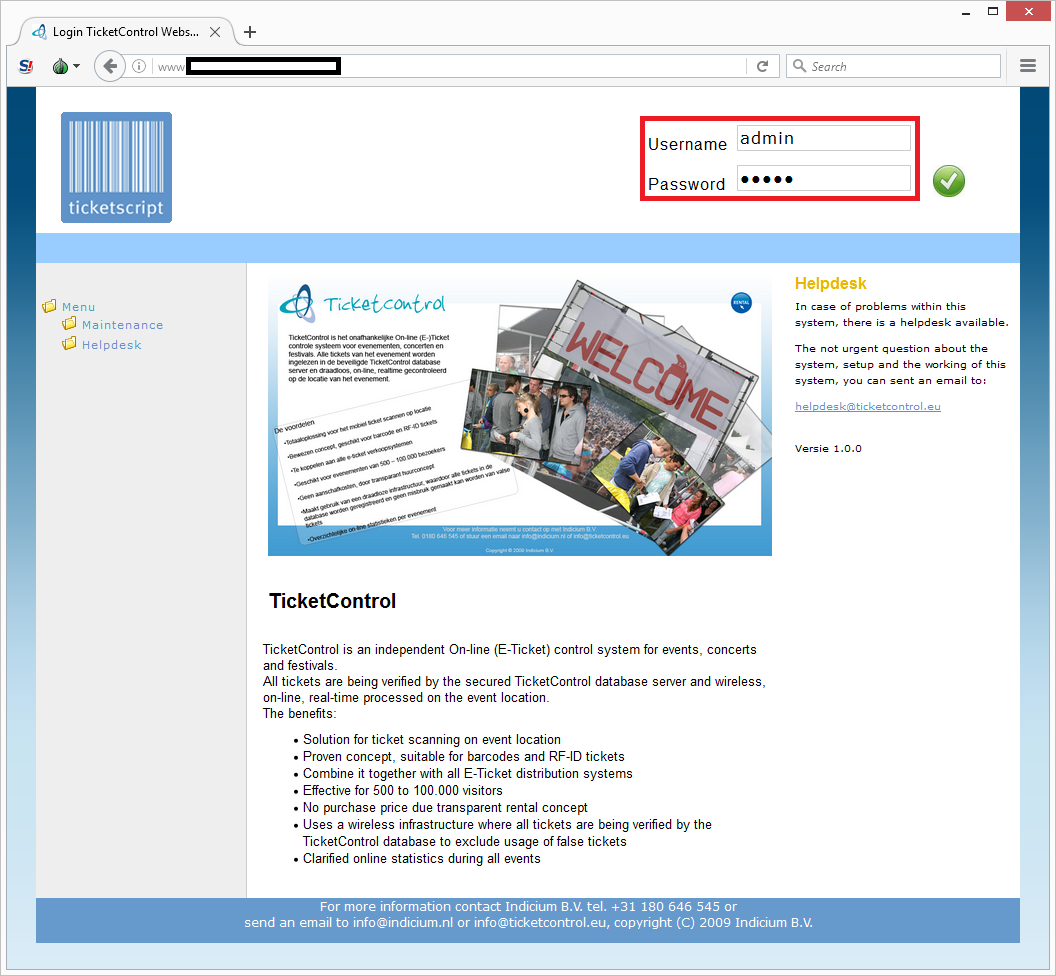
So for the greater good and under journalistic cover from AVROTROS, I started googling for administrator login screens of Dutch companies. When I had found one, I would try out to see if it had set the default administrator password ‘admin’. I didn’t have to search long and only after a few login screens I tried the password out on, I hit jackpot:
Whoaah! I was now logged in!
For a few moments I was stumbled of what just happened, and when reality kicked back in, I realized I was now logged in as an administrator on some kind of system. I looked around and realized it was an administration system that manages the sales and validation of tickets and events of customers of a company called Ticketscript.
In order to estimate the impact of this vulnerability to see if it was news worthy, I clicked around the system to get a grasp of its function and the data it contained.
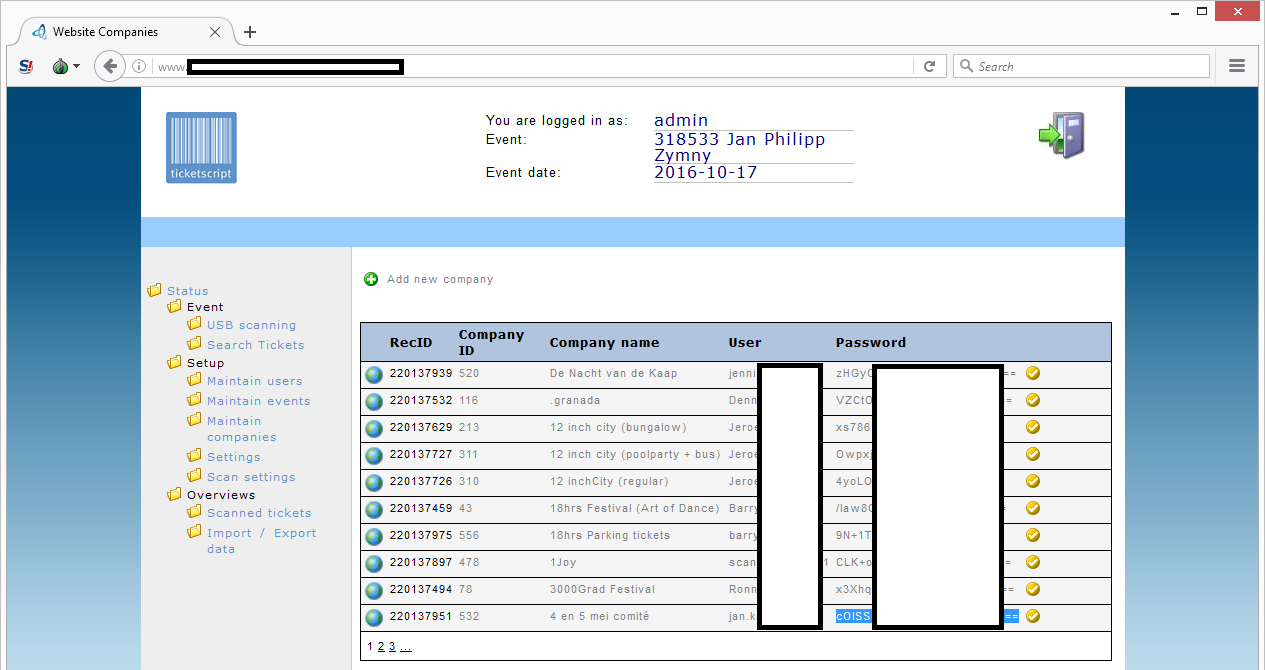
I clicked on the ‘maintain companies’ menu option and saw a list of user names and (base64) encoded passwords:
Oh my! Showing (encoded) passwords in a web page is never a good idea! An administrator should never see these.
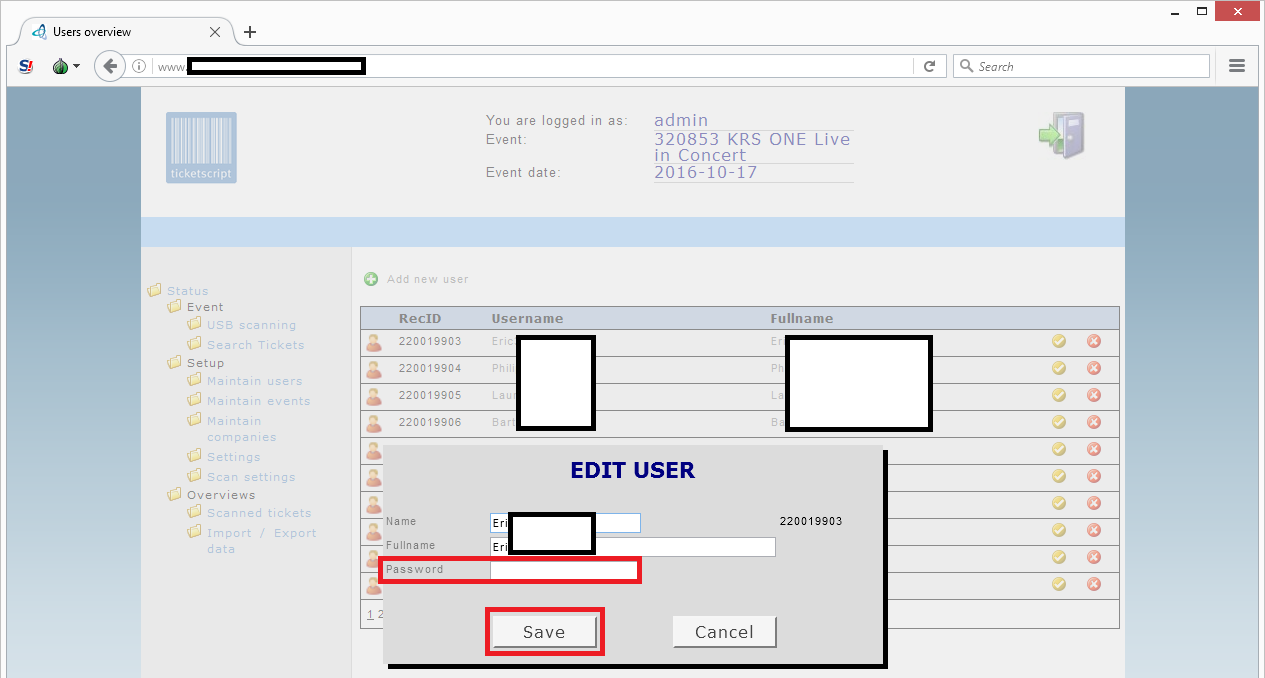
Configuring new account passwords
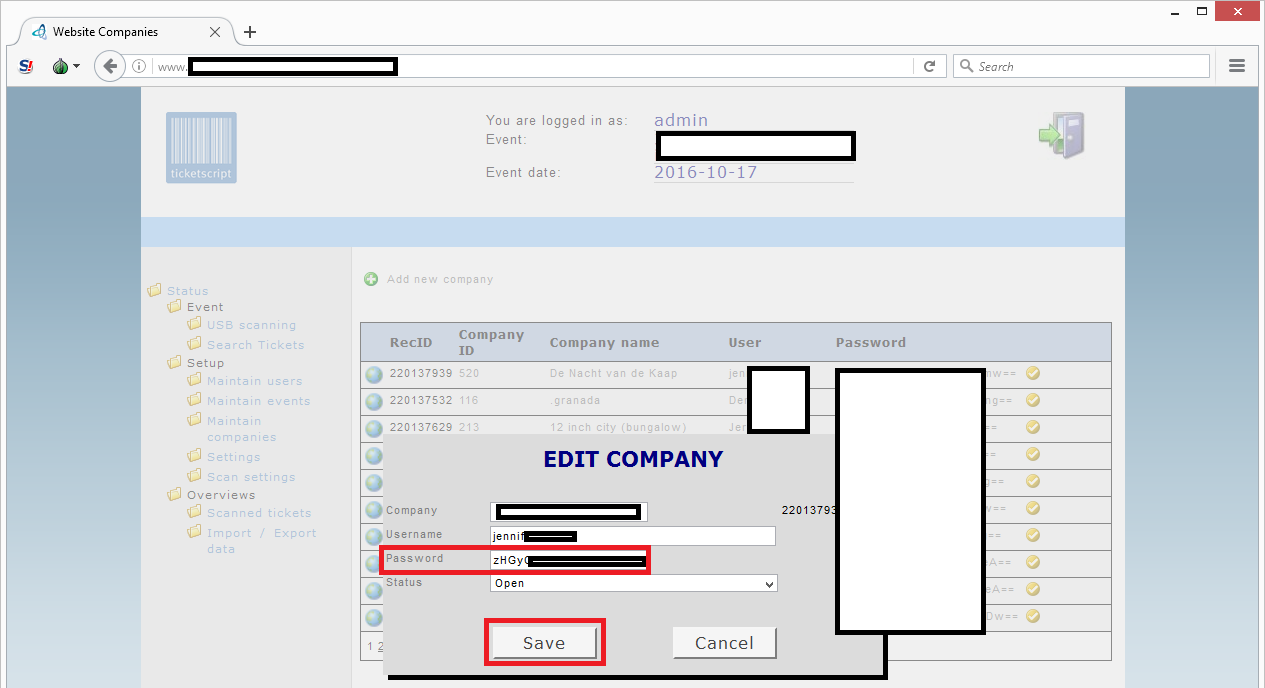
I clicked on a random company and apparently I can configure a new password for the account:
Via the menu option ‘maintain users’ I can also set new passwords for other users in the system if I wanted:
This administrator account has some serious power! It seems I got full access to their ticketing system.
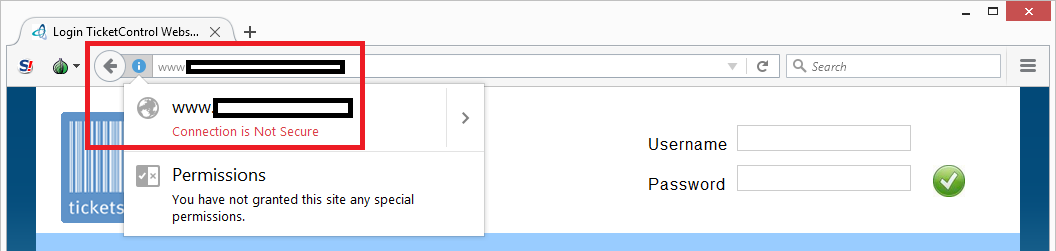
Insecure connection
The system runs over an insecure (HTTP) connection:
This means that all customer details and passwords are sent in readable format over the internet and susceptible for (man-in-the-middle) hack attacks. Every decent website that handles large amounts of personal records has implemented secure (HTTPS) lines nowadays. Ticketscript didn’t think security was important, or lacks fundamental knowledge about it.
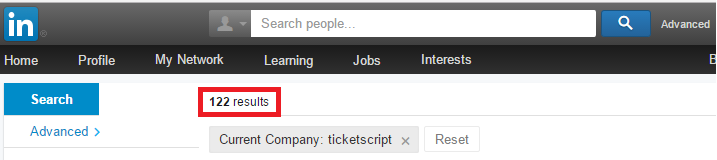
Checking LinkedIn
Just curious if I was right, I logged into LinkedIn and searched for all the Ticketscript employees. LinkedIn found 122 employees:
I’ve read all the 122 function titles and non of them have something to do with security or privacy. I think they immediately need an IT security officer, security manager and a privacy officer in order to actively and adequately defend their systems against modern day threats on the internet.
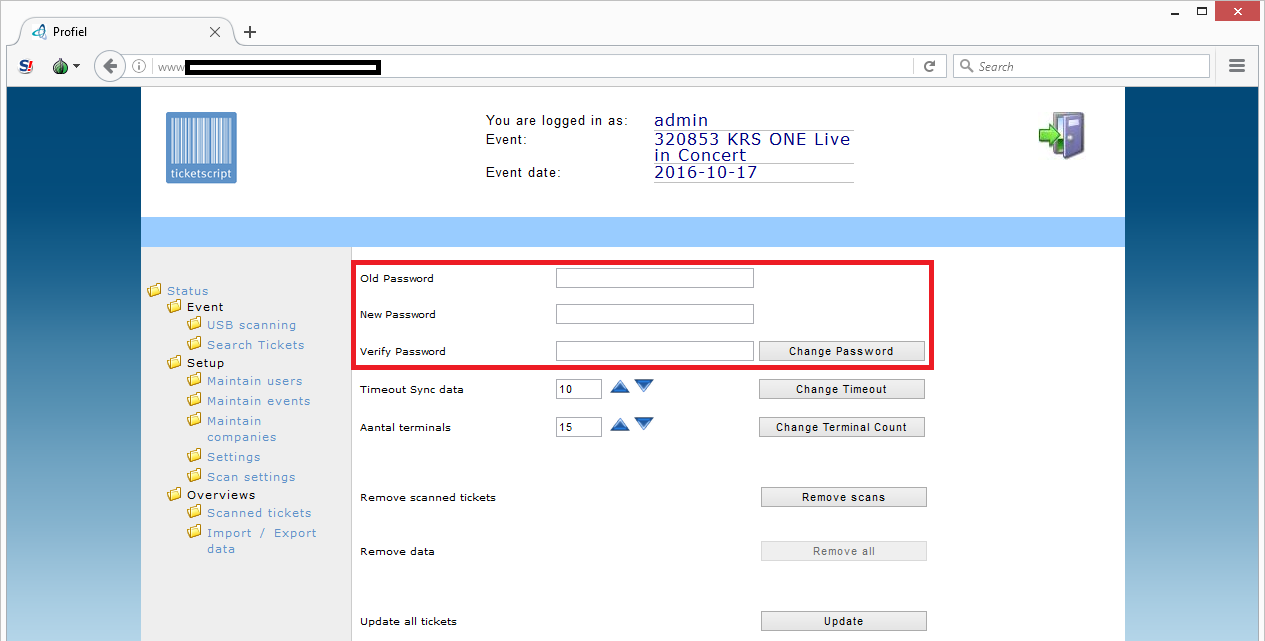
System administrator didn’t care about security
Back to the ticket administration system. Curious what this system else had to offer, I clicked on the ‘settings’ menu option:
I now have the option to change my own account password. Apparently the system administrator I was logged in as, didn’t even bother to invest one minute of his time to configure a strong password to protect all the company customer data that he is trusted with.
Default passwords everywhere!
After getting to know the system better, I figured out that they give customers the initial password ‘scan’ and then completed it with their corresponding user name. So user name ‘Esther1320’ would get the default password ‘scanEsther1320’ and it seems that all five company user names that I have logged in with to try it out, all still had the default password set.
This makes me wondering: are there any safe passwords set in this system?
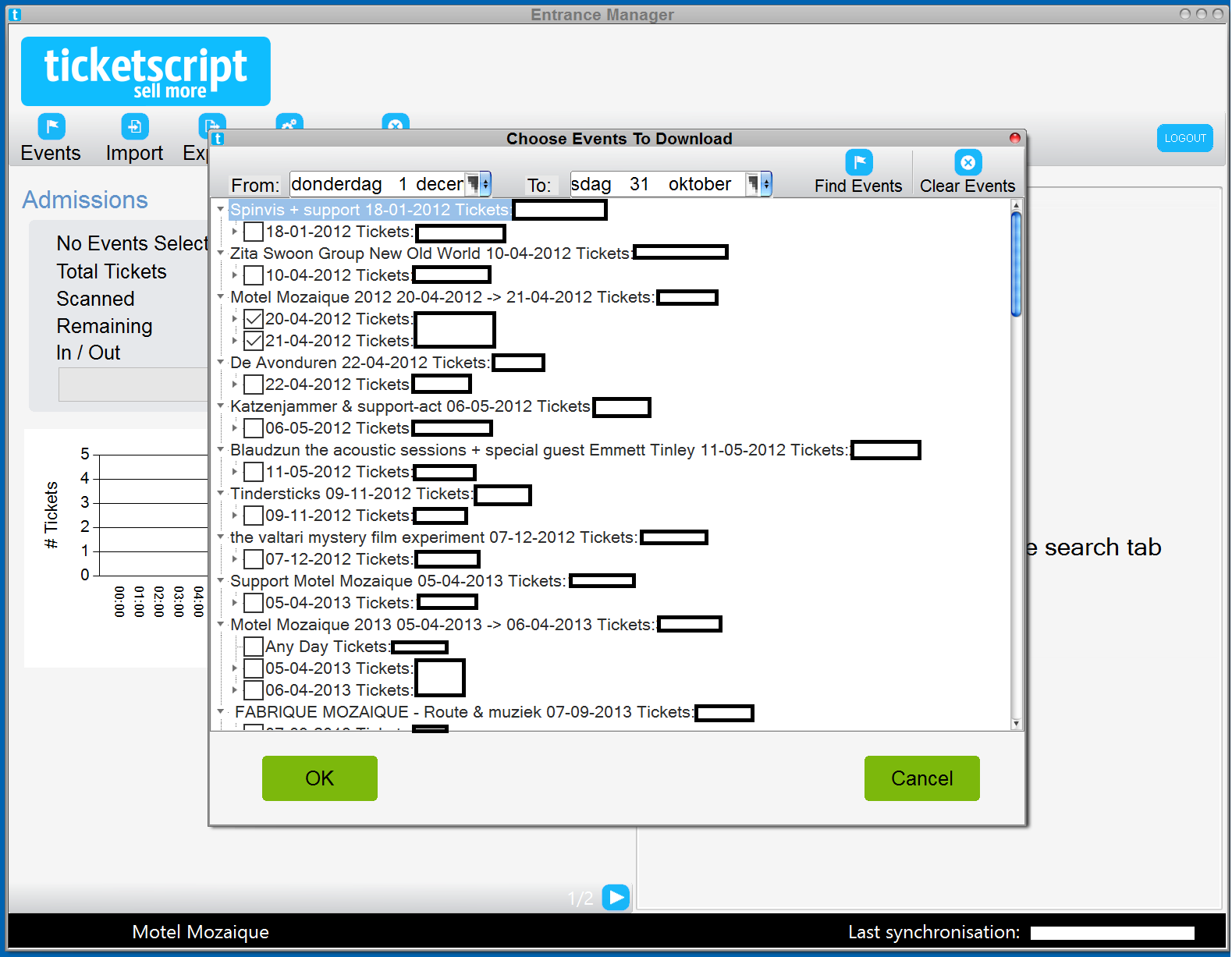
Their desktop application
Apart from this administrator web interface, they also have a desktop application where customers can log into. I logged in with an account from a customer and saw that the account had access to quite a few events:
Access to 10,000+ tickets
When I counted the total amount of tickets for only the events shown on the screen, not mentioning all the other events when I would scroll down, I already counted 10,000+ tickets!
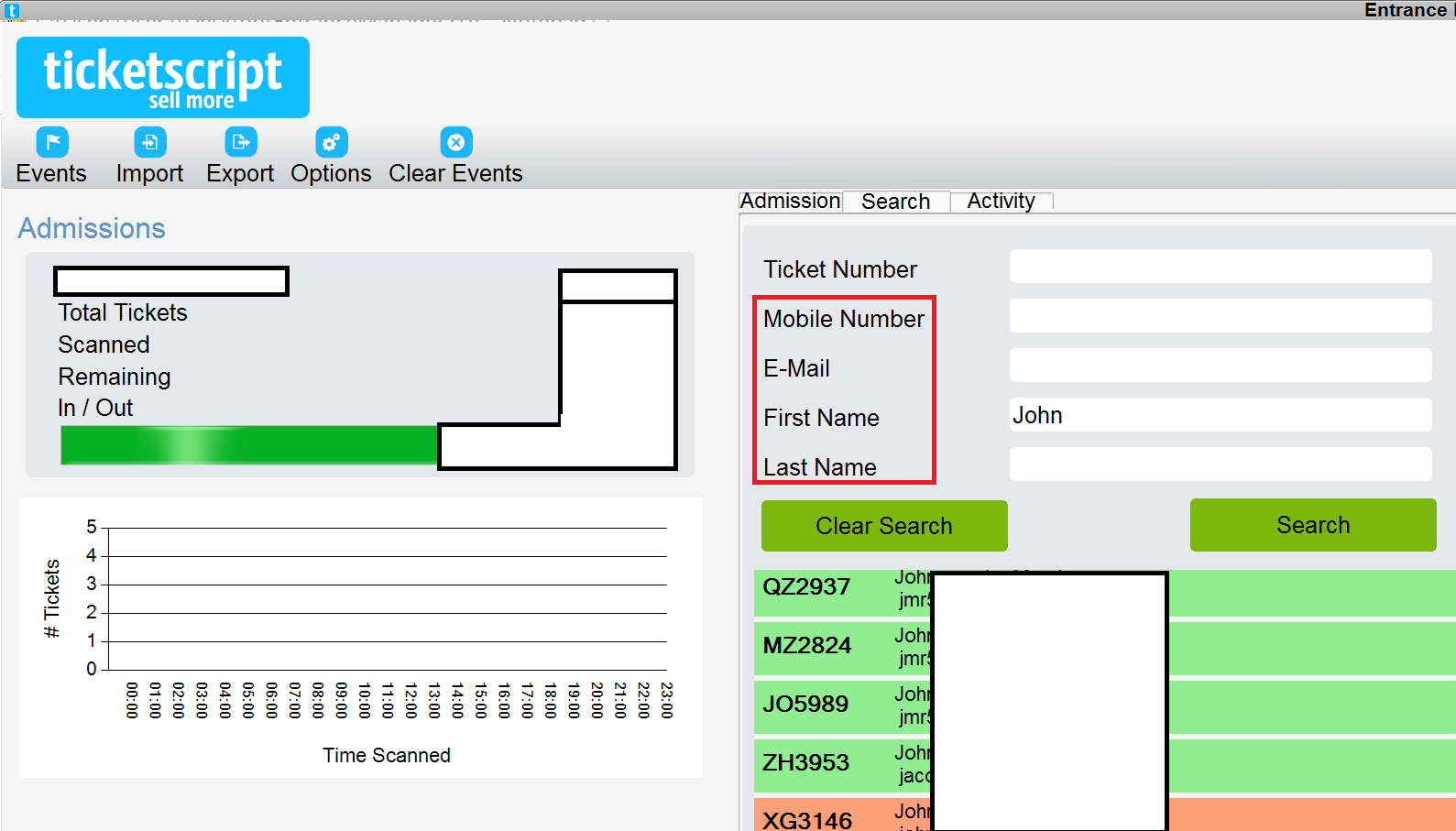
I selected an event and got access to personal details of attendees:
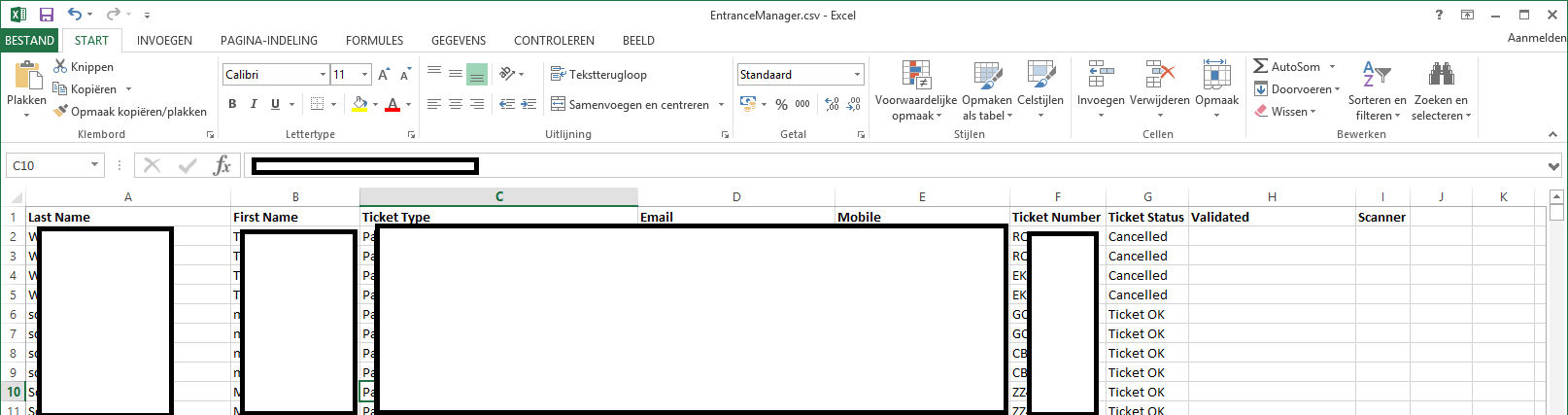
When I clicked on the ‘export’ menu option, I was served with a downloadable Excel file with all the personal details of the event attendees in it. In this case over 6,500 records:
The first name, last name, e-mail address and telephone number of attendees was easily exported from the system.
Fraud scenario’s
A malicious person can use this information to send spear phishing e-mails to event attendees that seems to be coming from Ticketscript, are personalized with someone’s first name and are about the event they have booked for. The phisher could attach a malicious PDF file that contains a JavaScript exploit against recent versions of Acrobat Reader and is about the invoice that hasn’t been paid yet. To increase to pressure the phishing mail states that the invoice is about to raise because the lack of payment yet. The moment an event attendee opens the PDF file and if they haven’t updated their PDF viewer, their system will get hacked.
It takes around 8 to 16 hours to set up and execute such an attack for a skilled hacker. I would bet that you’ll get thousands of new bots in your botnet if you would do that. If you fill in your bank account number in the fake invoice, you might also get some money occasionally 😉
About Ticketscript
The company behind this vulnerable system is Ticketscript:
“[..] Founded in 2006 we’re now Europe’s market leader in digital self-service ticketing with offices in Amsterdam, London, Berlin, Antwerp, and Barcelona with more than 100 employees.
It’s our mission to help event organisers get the most from their online ticketing and yes, you’ve guessed it, sell more tickets. Our services are used by over 125,000 events, selling over 20m tickets across Europe for festivals, exhibitions, air shows, fairs, sports events and more.
As a result we work with a wide range of renowned event organisers, both internationally and locally. These include Art of Dance (NL), Dutch Design Week (NL), Brighton Pride (UK), Tesco Wine Fair (UK), Waterstones (UK), Love Family Park (DE), Groezrock (BE) and Affordable Art Fair (INT). [..]
Impact of the breach
In above text it’s said that their clients sold over 20 million tickets. On their front page they say their clients sold over 25 million tickets. Are all those tickets managed via the ticket administration interface I had access to? I saw another login screen for a dashboard somewhere else.
With the administrator account I had access to, I could manage 1,100+ events, including those from the above mentioned Dutch Design Week and Tesco Wine Fair. If we take an average of 500 attendees and multiply that with 1,100, then we get 550,000. Let’s stay on the safe side and estimate that there are somewhere between 200,000 and 300,000 tickets managed in this system. That’s still quite a lot!
This data set would probably include the mobile phone numbers and e-mail addresses of famous DJs and VIPs. I could check that out, but then I had to download more data from the system and I don’t think that it would be an ethical thing to do. So far I only have shortly logged in under a few random accounts, clicked on a few screens and opened a few random events.
Free access to 1,100+ events!
I saw that I could register new tickets in the system for any given event or hijack existing tickets. This means that I and all my friends now had the ability to get free entry to 1,100+ events if I wanted to!
Responsible disclosure
Of course I wasn’t going to do that. Instead, I reported back to AVROTROS and they disclosed the findings to Ticketscript. Ticketscript responded formally through their attorney:
AVROTROS has made us aware of a vulnerability in a platform of one of our suppliers. This vulnerability was an unsafe user name/password combination. Immediately after this report, we have contacted our supplier and they fixed the vulnerability.
Further research has shown that the limited amount of data that was present on this platform was not compromised by any other person than the ethical hacker. The vulnerability was therefor not misused. Moreover, it involved only a limited number of non-sensitive data. Nevertheless, we regret the situation very much and appreciate it that AVROTROS has informed us about it so we could act adequately.
Good to hear they closed the hole!
Is it a data breach?
I made an effort to see and download as few personal records as possible during my research to estimate the impact of the vulnerability. The lawyer acknowledges this, and uses it to claim it’s therefor technically speaking not a data breach. Custom written summary of his reasoning:
“My client has proven by research that the ethical hacker has only accessed a limited amount of data. That data won’t be shared with others, and no other hacker has accessed the database. It’s technically speaking not a data breach and therefor it’s not mandatory to report this case to the Dutch authorities (Autoriteit Persoonsgegevens).”
That’s quite interesting reasoning and interpretation of the law!
Opgelicht?! Cyber Crime
This whole story was filmed and featured in episode three of TV show Opgelicht?! Cyber Crime, including an interview with me (it’s in Dutch):
Sites that link to this story

The response from Ticketscript is ‘nobody has seen the info’, but how do they know that? I don’t believe that they can prove that.
I dont think they have intrusion detection with not even having the most basic of basic security checks in place. This isnt even security officer stuff, its sysops 101 stuff.
Pingback: Gegevens 100.000 Nederlandse concertbezoekers door fout openbaar | Computer kennis en informatie
De Europese en Nederlandse grenzen zijn ook zo lek als een vrachtwagen vol mandjes,fijne [kerst] feestdagen nog in dit verloren landje.
T-Mobile past ook goed in dit rijtje. Ik kreeg diverse nota’s van een derde, leken echte T-Mobile nota’s, die correct afgeleid waren van mijn BELGEDRAG.
Ontsluiting van persoonlijk identificeerbare gegevens is een algemeen geaccepteerde datalek. Als jullie de reputatieschade overleven, laat dit een wijze les voor jullie zijn.
Sinds wanneer wordt een hack gezien als “kinderlijk eenvoudig”? Voor een hacker was dit misschien eenvoudig, maar om het nu kinderlijk eenvoudig te noemen… Het blijft een hack, ongeacht de moeilijkheidsgraad. Of je nu een fiets met een dun of dik slot op slot zet, het blijft diefstal, niet iedereen kan een slot van 80 euro betalen, zelfde geld voor beveiligingssoftware en IT kennis. Men moet leren of van andermans spullen af te blijven, ook in de digitale wereld.
Da’s wel heel vreemde stelling, we hebben geen datalek want niet alle data is gelekt. Kan iemand dit stel incompentente sukkels uitleggen dat je dan spreekt van een datalek als zouden maar de gegevens van 1 klant zijn gelekt.
Doe maar gewoon VVV zoals vroeger was altijd goed
Het bedrijf moet voor zijn wandaad voor de rechter gesleept worden met een extreem hoge boete in het vooruit zicht. Nooit geen tickets hier meer bestellen omdat je niet weet of jouw gegevens inmiddels vor crimineel gebruik op straat liggen.
Ticketscript mag niet liegen en om het goed te praten is nog veel dommer en maakt Ticketscipt nog ongeloofwaardiger!
Toegang tot namen, telefoonnummers en e-mailadressen is een datalek beste vrienden van Ticketscript. Wat een stelletje amateurs! Hopelijk krijgen jullie een hele grote boete van de de AP. Zal wel niet, want die zitten ook met twee man en een paardenkop…..
@brenno zeg jij d’r ‘s wat van http://www.telegraaf.nl/%5B..] @ticketscript_nl
kan iemand aan @ticketscript_nl uitleggen dat een gedeeltelijke #datalek ook een datalek is. stel sukkels #admin
De meetup in oktober bij @ticketscript_nl was leuk maar hoe ze met het datalek omgaan is erg teleurstellend. Pak je verantwoordelijkheid!
@vandenhof @ticketscript_nl Zeg dat wel. Bijzondere reactie.
@Jesperw @ticketscript_nl gevalletje juiste mensen, beroerde directie/management denk ik. Erg jammer.
Best wel slordig: Ticketscript-database gaf toegang tot data kwart miljoen concertbezoekers https://tweakers.net/nieuws/119259/ticketscript-database-gaf-toegang-tot-data-kwart-miljoen-concertbezoekers.html via @tweakers
Ik hoop niet dat het SQL Injection was?
Pingback: Fout bij Ticketscript: privégegevens van 250.000 concertgangers liggen op straat
@ticketscript_nl lekker handig. admin admin. hahahhaha
Als je tickets via Ticketscript hebt gekocht, pas op phishing mails! Gegevens 100.000 concertbezoekers openbaar
Hier is geen sprake van een datalek dat gemeld moet worden aan de Autoriteit Persoonsgegevens.
Volg de stappen in de richtsnoeren meldplicht datalekken van de Autoriteit Persoonsgegevens.
Stap 1: Is er sprake van een inbreuk op de beveiliging? “Een inbreuk op de beveiliging houdt in dat zich daadwerkelijk een beveiligingsincident heeft voorgedaan. Er is niet uitsluitend sprake van een dreiging, of van een tekortkoming in de beveiliging (ook wel aangeduid als een beveiligingslek) die zou kunnen leiden tot een beveiligingsincident.” Dus dat het systeem min of meer openstond, is geen inbreuk op de beveiliging. Het bedrijf heeft kennelijk via logs geconstateerd dat er geen andere onbevoegden toegang hebben gehad, anders dan de ethical hacker. Dus ja, er was een inbreuk op de beveiliging, namelijk de toegang door de betreffende ethische hacker.
Stap 2: Zijn er bij de inbreuk persoonsgegevens verloren gegaan? Ja, want de ethische hacker heeft persoonsgegevens ingezien.
Stap 3: Is er sprake van ernstige nadelige gevolgen voor de bescherming van persoonsgegevens? Nee, het betreft hier 1 ethische hacker die bij naam bekend is. Er mag verondersteld worden dat deze ethische hacker geen complete download heeft gedaan. En tevens dat deze ethische hacker en de medewerkers van het televisieprogramma de wel vergaarde gegevens danwel ingeziene gegevens niet misbruiken.
Conclusie: dit is wel een datalek (betreft dan alleen de toegang door de ethische hacker) , maar geen datalek dat gemeld hoeft te worden aan de Autoriteit Persoonsgegevens.