On September 11, 2015 I visited MediaMarkt in Utrecht Hoog Catherijne, a well-known electronics shop in The Netherlands. Since summer 2014, the biggest independent Dutch phone retail company Phone House also operates (white labeled) from within MediaMarkt locations as a store-in-a-store concept. I had a few questions about my phone subscription so I talked to a Phone House employee. We were discussing the new Samsung Galaxy S6 Edge phone and I was thinking about buying one.
Somewhere in the conversation the service & sales guy asked me what I did for a living so I told him I earned my money as a freelancer by hacking (with authorization) into computer systems of businesses and writing security reports about it. He thought that was cool so we talked a few more minutes about this subject. I even told him I had noticed some months ago that one of his MediaMarkt colleagues had written a password on a post-it and attached it onto a computer monitor near a cash desk, in plain sight where any customer could see it :
As you can see, the password to unlock MediaMarkt computers was media321. A very strong one!
We both laughed about how irresponsible and naive that was.
The conversation continued about my desire for a new phone and about all associated kinds of subscriptions I could choose of. After about ten minutes I made up my mind and ordered a new phone and a new subscription. I’m still in shock about what happened next!
Context
But first two things about the context:
- As Phone House is not a telecom operator itself, it functions as a dealer for telecom operators in The Netherlands such as Vodafone, KPN, Telfort, T-Mobile, Tele2, UPC and others. So, they can basically cover the complete Dutch telecom market.
- The telecom service & sales desk is located in the middle of the MediaMarkt store and designed in such a way, that customers can look at the computer monitors used by the employees. No effort is made to block your view on the monitor and customers can look straight in on MediaMarkt’s service computers.
Opening up the password file
The sales guy started renewing my Vodafone subscription and therefor needed to log in at a dealer portal from Vodafone. He didn’t remember the login password, and, here it comes, on the screen he opened an Excel file which contained *all* their passwords.
Is this happening for real? I had just told him minutes ago I’m an experienced professional hacker and we had both laughed about the password-taped-on-monitor leak.
Curiously and intensively I looked on the screen to get a picture of the treasure trove that was in front of me. Passwords to view and modify customer data of KPN, Vodafone, Telfort, T-Mobile, UPC, Tele2 and other companies were in plain view.
A curious detail was that the Excel password database was stored on Google Docs and the login details of their Google Account were also in front of me. Neat! I could look up their passwords anytime I wanted from any computer in the world.
Passwords stored unencrypted on Google Docs
As Google is a company located in the United States, the Google Docs servers are probably also located there, or at least subject to the Patriot Act. I think it’s safe to say the NSA probably (still) has direct access to documents stored in Google Docs. The password database is stored without encryption in the cloud so it can be assumed the NSA has access to it. So much for all the encryption effort made by Dutch telecom providers after the Edward Snowden leaks: Phone House is trusting their passwords to an American company.
Leaving the file open
The sales & service guy who assists me is frequently approached by his colleagues for help. Apparently he’s the senior of the telecom department.
He printed a renewal contract for me which I had to sign. I told him I first wanted to read it. He said: “You’re the first person in years who wants to read the contract”. I often hear that. Apparently nobody takes time to read only one page of small text. Most people seem to blindly trust companies, but I’m not like that. The sales guy said: “Take your time”, and then moved away from his desk to reorganize products in his part of the shop. He left the password sheet open right in front of me. I couldn’t believe what he had just done. Was he testing me?
The battery of my old phone had died (hence I wanted a new phone) and unfortunately I couldn’t take a picture of what had just happened. I silently cursed. Without any evidence, would a stranger believe me if I told him what had just happened? I think it’s a small chance: seeing is believing.
Documenting the password gate
I left the shop and returned three weeks later on October 3rd (2015) curious to see if the same employee I spoke to in September was working there again. But he wasn’t! Well, let’s try with his colleague to see if I could social engineer him in such a way that he would open the password file again. I asked him something about my subscription. To answer that, he needed to login to the Vodafone portal, and yeah, there we meet again, my precious password file:
I also made a high resolution photo of the screen:
 All passwords in above screenshot are changed by now and I’ve removed parts of user names, so that brute forcing passwords of those accounts is not that easy anymore for villains.
All passwords in above screenshot are changed by now and I’ve removed parts of user names, so that brute forcing passwords of those accounts is not that easy anymore for villains.
It was not just an incident in which one employee was careless with the company password database, apparently multiple employees were. Seems like a structural problem and a fundamental lack of security and privacy awareness within Phone House and MediaMarkt.
Password strength analysis
As a customer you would expect the company you trust your personal data to, to make the utmost effort in protecting those, right? Doesn’t seem to be the case here. Your personal details were protected via passwords such as:
- m
- 12345678
- Utrecht
- beginnen01
- Utrecht12345
- upc12345
- Welkom03
- Mediautr03
For the non Dutch readers, I’ll translate the following Dutch words:
- ‘beginnen’ means ‘to begin’.
- ‘welkom’ means ‘welcome’.
- ‘utrecht’ is the city the shop is located in, sometimes abbreviated as ‘utr’.
As you can see, there is even an account that has an one-character password and the password 12345678 is used in multiple accounts. And that last password is the fourth most used password in 2014. Phone House employees must lack creativity or just don’t care. Also the dealer portals don’t enforce strong passwords.
Looking at the passwords Welkom03 and Mediautr03 it seemed that a password change policy was active on some systems that forces users to regularly change their passwords. It seems like Phone House employees have found a system to circumvent that protection by incrementing the digit of their password each time. They have probably already done so twice. Giving user accounts the initial password Welcome01 is de facto standard in companies, as this one complies to most password policies: it consists of upper and lower case characters, and also contains multiple digits. You should welcome your new users, right?
User name analysis
All the user names in the password file are non-personal. This means that telecom providers and Phone House can’t hold account of who exactly logged in with a given user account. Also, if a Phone House employee quits the company, all passwords of the shared non-personal accounts should be changed. Given the circumstances I highly doubt this to be the case.
Even if the passwords for some accounts are regularly changed, the most important password, that of the Google Account in which the password database is stored, seems to be static: Utrecht12345.
Opening up the dealer portals
The password sheet contained all kinds of portal names, but their internet addresses weren’t located in the file. In order to estimate the risk involved, I needed to find out if these portals were freely accessible over the internet, so I started googling them. Within a minute I found that the employees of a Phone House store located in the city of Joure created a public link directory with all locations of the dealer portals they use:
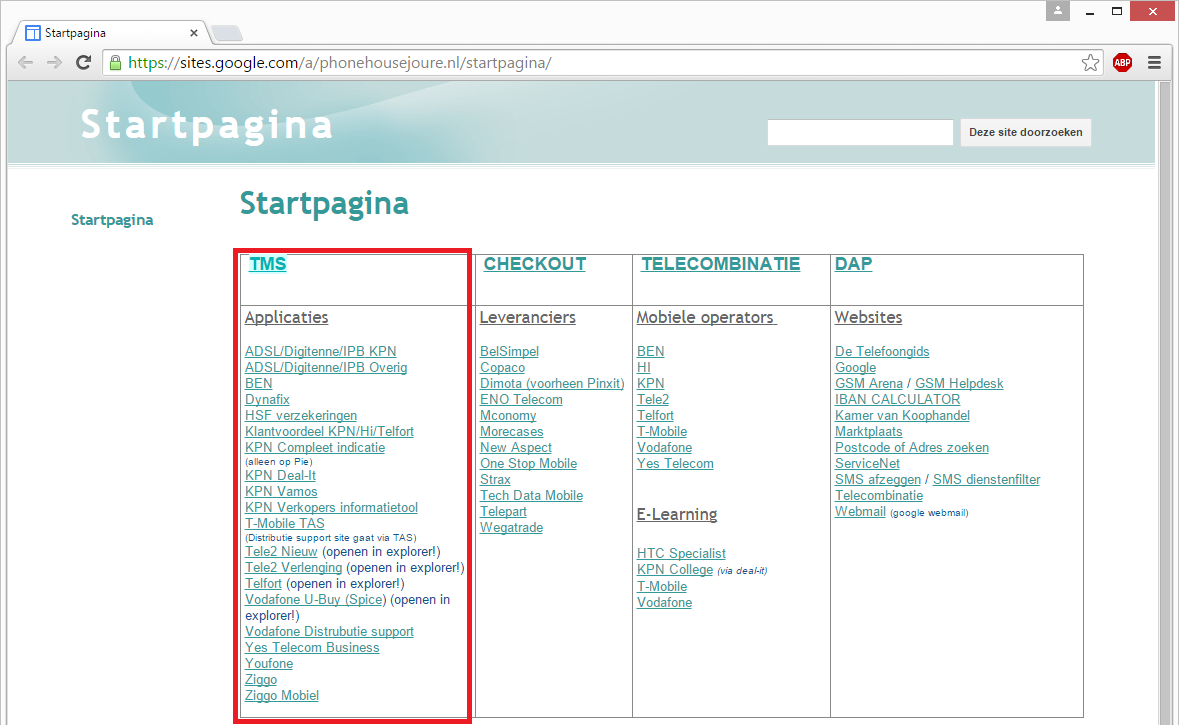 This link directory has been taken offline after reporting it to them.
This link directory has been taken offline after reporting it to them.
I clicked on all dealer portals to see if they were freely accessible via internet, and quite a lot of them actually were:
| ADSL/Digitenne/IPB KPN | : | Login screen visible |
| ADSL/Digitenne/IPB Overig | : | Login screen visible |
| BEN | : | Just links to the main Ben website |
| Dynafix | : | Login screen visible |
| HSF verzekeringen | : | Login screen visible |
| Klantvoordeel KPN/Hi/Telfort | : | Error message is shown |
| KPN Compleet indicatie | : | Error message is shown |
| KPN Deal-It | : | Login screen for business market visible. Login screen for customer markted protected via IP address whitelisting |
| KPN Vamos | : | Error message is shown |
| KPN Verkopers informatietool | : | Link redirects to main KPN website |
| T-Mobile TAS | : | Login screen visible |
| Tele2 Nieuw | : | Login screen visible |
| Tele2 Verlenging | : | Login screen visible |
| Telfort | : | Error message is shown |
| Vodafone U-Buy (Spice) | : | Error message is shown |
| Vodafone Distrubutie support | : | Login screen visible |
| Yes Telecom Business | : | Login screen visible |
| Youfone | : | Login screen visible |
| Ziggo | : | Login screen visible |
| Ziggo Mobiel | : | Link redirects to main Ziggo website |
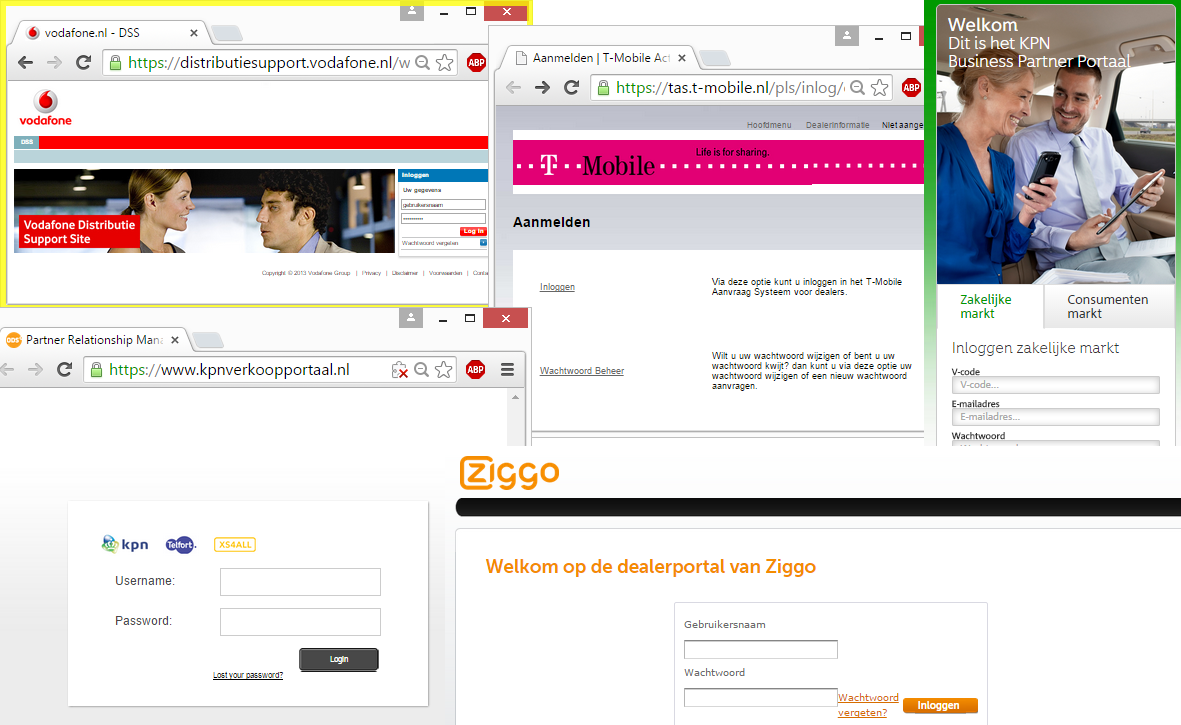 Some examples of accessible dealer portals.
Some examples of accessible dealer portals.
Six portals seemed to use mutual SSL/TLS authentication and/or IP address restriction, like it should be, but twelve portals were freely accessible. This means that I could log in as a Phone House employee on those dealer portals and manage the configuration of customers. I didn’t log in. If I had done so, I would have broken the law and I never do this.
I could use the easy to use Tor Browser Bundle in order to masquerade my IP address. That way I could perform the unauthorized access completely anonymous, leaving no traces. That ‘crime’ would be hard to solve.
Circumventing IP address restriction
The portals that have IP address range restriction set-up, can easily be defeated by covertly installing a LAN Turtle or mobile broadband enabled WiFi Pineapple in one of the MediaMarkt shops, so remote access is gained to their internal network and thus the IP address restriction can be circumvented.
Finding a network cable or socket to attach the remote access device to is fairly simple, as MediaMarkt is an electronics shop, and customers have easy access to all kinds of occasional unmanned support desks which are located everywhere in the shop. I had quickly located several vulnerable spots.
Impact of leak
My personal estimation is that Phone House, via dealerships, has access to personal data of basically all Dutch citizens who own a mobile phone. That would be somewhere between 10 and 14 million people; only counting the people who are alive. But I guess these portals also contain data of deceased people. Black hat private detectives, stalkers and fraudsters would love to have direct internet access to such a trove of personal data.
I discovered my findings had been applicable to all MediaMarkt and Phone House stores for over a very long period of time. More on that later.
Back to Phone House Joure
The Phone House store in Joure created a Google Sites website in order to host their links on. Wondering how recent the link directory was, I clicked on the ‘recent site activity’ link in the footer:
The complete history of all site modifications was shown. Including a change to a specific file that had nothing to do with the link directory:
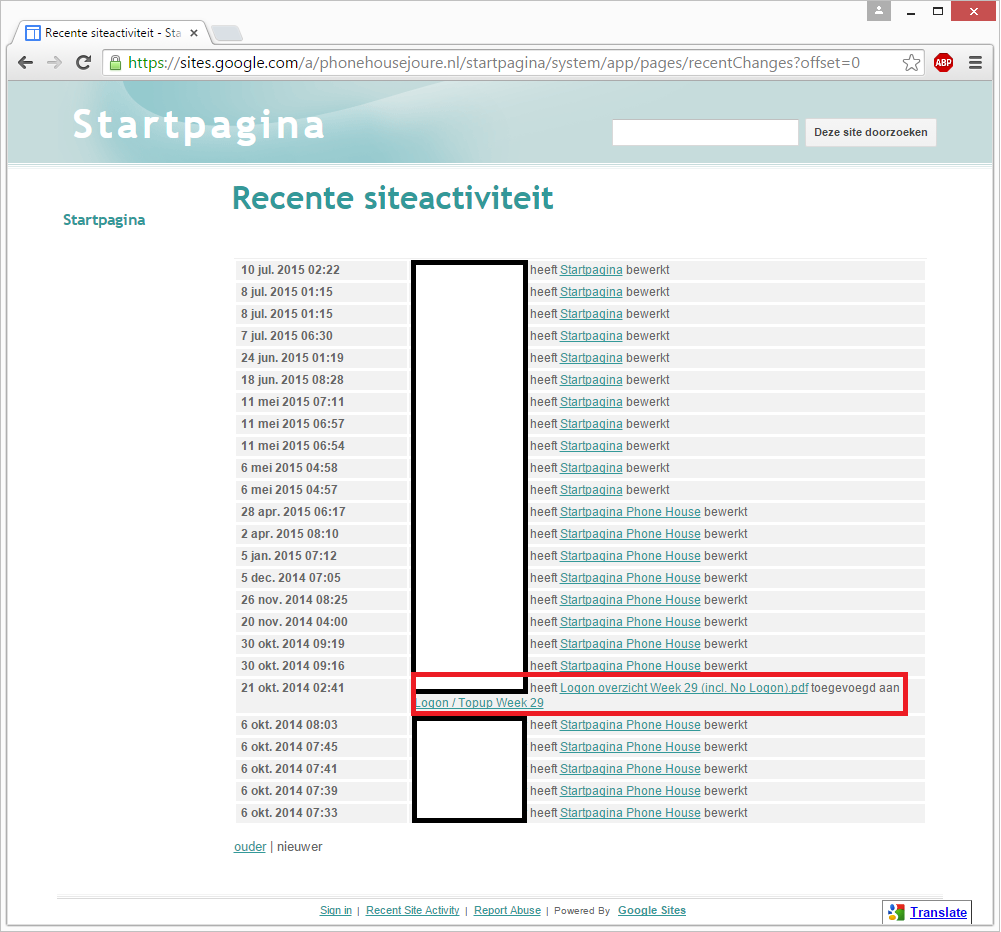
This is the change log of Phone House Joure’s modifications to their internal website. I removed employee information from those that were responsible for the changes made.
I clicked on that specific file to see what it could contain:
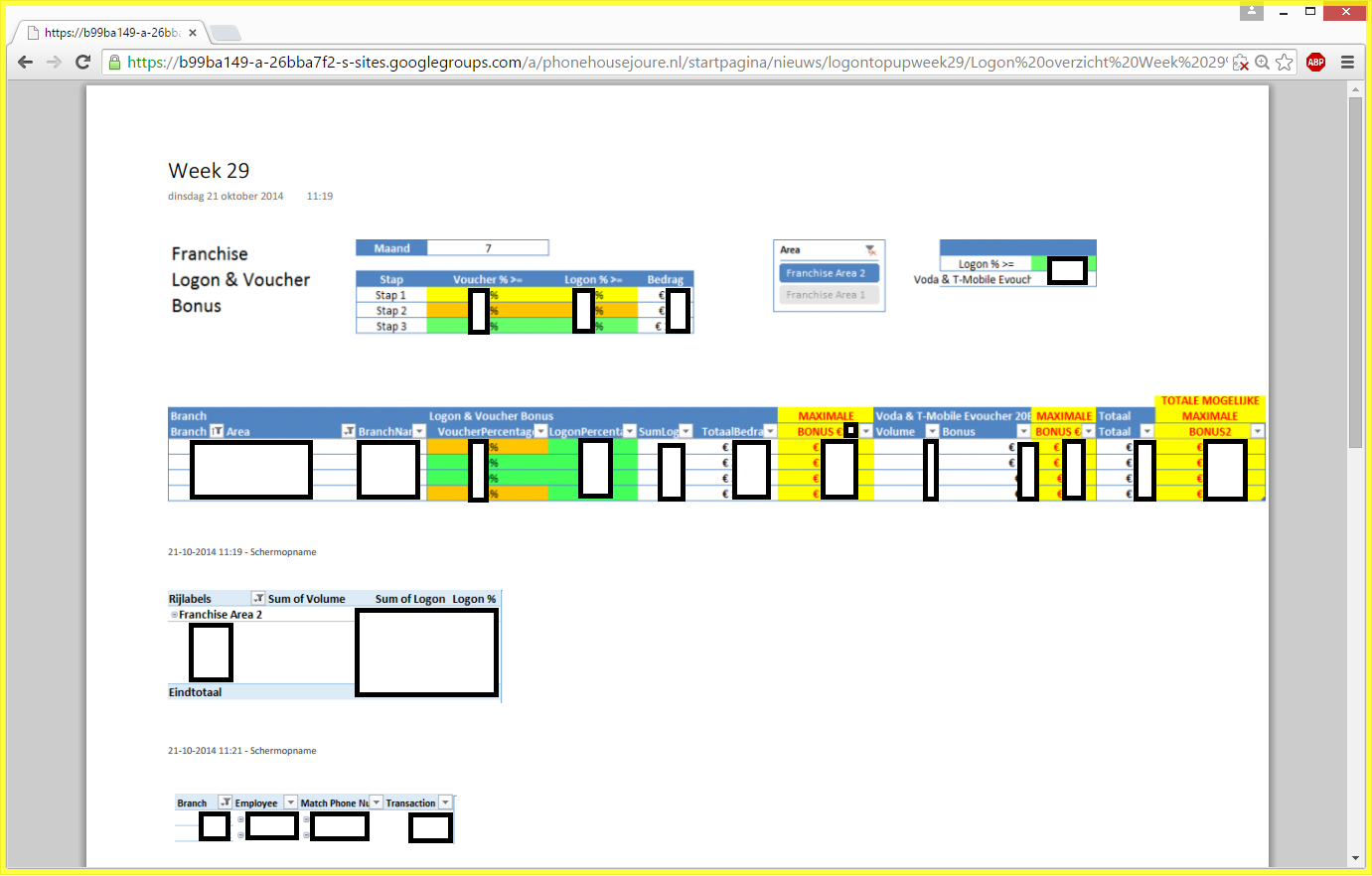
This is the Phone House financial administration. I removed all numbers and names.
Things were getting weirder. What I saw seemed to be internal financial administration of Phone House Joure. Somehow I got the feeling this was private company data and not meant to be seen by others. Or has Phone House got a really transparent policy towards their provision and sales data? Okay, I’m not to investigate this particular matter any further. I digress. Back to the password story.
Computers are never locked
What I noticed as well, was that every time service & sales employees leave their computers, they never-ever lock it. So people walking by have full and easy access to it. Furthermore, on all occasions that I was able to look at the password file, it had already been opened by the employee. They just had to press ALT + TAB to re-activate it.
Leaving a computer unlocked when walking away makes it very easy for an attacker to obtain passwords. Also, I noticed this specific computer had easy-to-reach USB ports. I could perform a USB drive by attack with a prepared Rubber Ducky or Teensy, with which I could have gained remote access to the computer within 10 seconds.
Auto completion of passwords
Web browsers of Phone House computers are configured to save user names and passwords and pre-fill them (most of the times) whenever they’re navigating to a login screen. A computer user only has to press the ‘login’ button to enter the system. Permanently storing passwords in browsers is risky as they are by default stored non-encrypted on the computer. A master password could be configured to open the browser password store (and add encryption), but practice unfortunately shows that most users never configure one.
Opening up a customer file
Another remarkable thing I noticed, was that I only had to give my telephone number to the Phone House employee and subsequently my Vodafone file would be opened. No other security questions were asked to validate my identity. However, a reverse validation question was indeed asked: “Do you live at address [..]?”. I malicious person would of course reply: “Yeah I definitely live there”.
What should have been the case
Summarizing the situation; how should it have been done ideally?
Improvement points for Phone House and MediaMarkt:
- Don’t write passwords on post-its stuck onto monitors.
- Don’t let (potential) customers look in on the screen an employee operates on.
- Physically shield the viewing angle of the computer monitor.
- Apply a privacy screen on the monitor to further minimize the viewing angle.
- Create strong passwords.
- Change passwords frequently.
- Lock computer screens when leaving the computer.
- Never use a non-personal account with multiple people. Create individual user accounts for all employees.
- Change the passwords of non-personal accounts when an employee who had access to those accounts quits the company.
- Use a safe password store, such as KeePass, that shields passwords and uses strong file encryption.
- Don’t store the password database in the cloud.
- If a cloud solution is nevertheless used (and still, keep your password database out of it), use a cloud provider with a data center in The Netherlands so that intelligence agencies such as NSA and GCHQ don’t have direct access to your files.
- Never store passwords on a computer without encrypting them.
- Always close the password database file after coping the password that was needed.
- Protect user accounts (such as the Google Account) with multi-factor authentication (such as Google Authenticator).
- Don’t publish links to dealer portals publicly on the internet and also shield your financial administration.
- Perform decent checks to validate if a customer is really who he says he is:
- When working with personal data in a store, always ask to see the customer’s identity card. It’s mandatory in The Netherlands to have one on you at all times.
- If a customer calls the service desk, call him back on the telephone number that is linked to the customer’s account.
- Disable USB ports on computers via a software or hardware solution.
- Train your employees in IT security and privacy practices.
- Create the right corporate culture so that security and privacy is propagated by your employees.
Improvement points for telecom operators:
- Make sure dealers have the possibility to create individual user accounts for their employees.
- Apply IP address restriction on dealer web portals.
- Require a client HTTPS (X.509) certificate when setting up a connection to a dealer web portal.
- Enforce a strong password policy, such as:
- a minimum password strength of eight characters;
- a password that isn’t known in brute force password lists;
- add custom complexity rules: enforce the use of upper, lower case, numbers and special characters;
- passwords can’t be the same as user names;
- enforce that passwords are regularly changed;
- enforce that changed passwords aren’t re-used and are substantially different in comparison to previously configured passwords.
- Make sure that your web portal supports multi-factor authentication.
- Disable the HTML AutoComplete option in web forms that process authentication data such as passwords.
When summing it all up, you see it’s quite a list of things that went wrong (!).
It makes me very sad that all mentioned above still isn’t regular practice for businesses in 2015.
MediaMarkt threatens to sue me and denies everything
It’s time to contact Phone House and MediaMarkt and tell them about my findings (October 4, 2015). As I had the direct e-mail address of the responsible MediaMarkt department in Utrecht (it was visible in the password file), I mailed them my findings. They didn’t respond.
A few days later I got an e-mail from the store manager of MediaMarkt Utrecht Hoog Catherijne and he threatened to sue me if I went public. There you stand as a good willing civilian just wanting to make the world a safer place. I think it’s childish and also a very hostile response towards someone who simply notifies you of a critical security vulnerability that your company is responsible for. It’s like shooting the messenger.
To go even further, MediaMarkt denied I could get access to web portals which are hooked up to the internet with the captured login details. This response demonstrates the fundamental lack of knowledge about how the internet works. I’m not crazy: if I have login details and if the login screen is accessible over the internet, then I can log in with those credentials. Simple as that. But I didn’t do so, since it’s illegal.
MediaMarkt dismissed all my findings as “appearance of insecurity”. Talking about ignorance … They concluded their e-mail demanding I destroy the pictures I took of their passwords within 24 hours.
I replied explaining how responsible disclosures work and that this attitude towards me is damaging their own company. To eliminate any possible anxiety people have when in contact with a hacker, I clearly stated my intentions were good. This luckily had a positive effect and the next day I was invited for a cup of coffee. More on that later.
Contacting the affected telecom providers
As I had anticipated such a lame initial response from MediaMarkt and Phone House to be possible, I had also taken time to inform the telecom providers involved. These providers are very important stakeholders for Phone House and can apply the right company-pressure in order to fundamentally improve security and privacy practices. In comparison to MediaMarkt, all involved providers were very polite towards me.
I have to give special credits to the KPN computer emergency response (CERT) team. They contacted me frequently about their progress and also immediately set a minimum password strength policy on their dealer portal, so one character passwords weren’t possible anymore. KPN has become very capable of handling responsible disclosures ever since they were badly hacked in 2012. Kudos for them. They were also the only party involved to give me a nice bounty:
The Vodafone security guy also was very kind towards me, as well as Tele2, who took time to learn about the whole story.
Status: two weeks after disclosure
Two weeks after I had contacted all parties involved, I went back to the MediaMarkt store, cause I was in need of a birthday present for a friend. I also had a genuine question about my Vodafone subscription.
When entering the shop, I saw no more passwords written on post-its stuck onto monitors. Things were looking better! So I went to the telecom desk with my question. The employee logged in on Windows with a password that ended with 1234. I couldn’t see it clearly, but I think the first password part was media. Cool, they had also changed their main Windows password and made it more secure by adding an additional character. media1234 is so much more secure compared to media321. Good job!
Then the employee logged in on another system. He hit character 1 and with one smooth and fluent movement only stopped his finger at character 8. I’ve never before seen anyone entering password 12345678 in one smooth swipe like this. It really looked cool!
Subsequently, he opened up the notorious Excel password file in front of my eyes. Some passwords had been changed, many had not. Actually, nothing really had changed.
MediaMarkt, we need to talk.
Having coffee together
A few days later (October 22nd, 2015) I went to meet the store director face-to-face. Given the circumstances, the start of the conversation was slightly uncomfortable. I was told they initially misinterpreted my intentions and had seen me as a bad hacker.
Once the ice had been broken, I told him password gate had not yet been fixed and urged him to take action immediately. He said he was waiting for Phone House to act since it was their infrastructure and personnel. I told him I wanted the vulnerabilities to be fixed before I was going to publish this story. To add pressure, I added that I didn’t want to wait very long with this publication.
As a quick and dirty fix that would close the most important gate in five minutes, I suggested they make the font color of the passwords in the Excel file black, as well as the background color of the cell. This would still enable the telecom employee to copy the password to the clipboard, but the password would not be visible anymore when shoulder surfing. I told him to apply this patch himself and shouldn’t wait for Phone House to do so.
A week later
Curious to see if progress had been made, I sat down with the director a week later (October 28th, 2015). Our earlier conversation had impact since directly afterwards various actions had been performed and internal company pressure had increased to set priorities right:
- All my recommendations (as mentioned above) had been sent to all fifty MediaMarkt stores in The Netherlands and to Phone House as well.
- They had chosen a safe software product to store their passwords on. A lengthy manual had been written (they even showed it to me); so their employees would know how to use it.
- Privacy screens had been installed and the secure password database was now implemented in the MediaMarkt store in Utrecht.
The director asked me to wait with publication for a few more weeks as Phone House had planned a road trip to install their new password store software in all their shops, of which there are quite a lot.
I told the director I had not heard anything from Phone House yet and given the circumstances I felt as if I was being ignored. He relayed that feeling and the next day I got a friendly call from Phone House.
Having coffee together helps!
TalkTalk gets hacked
As I first began writing this story, the large British telecom provider TalkTalk got hacked. On October 30, 2015 they confirmed the following numbers:
- Total number of customers whose personal details were accessed is 156,959;
- Of these customers, 15,656 bank account numbers and sort codes were accessed;
- 28,000 obscured credit and debit card numbers were accessed.
According to TalkTalk “these criminals were very smart” and the attacks were “sophisticated”.
A week later the BBC reported that four people have been arrested over the hack so far: a boy of 15 in Northern Ireland, a 16-year-old boy from west London, a 20-year-old Staffordshire man, and a 16-year-old boy in Norwich.
When it can be performed by teenagers, I wouldn’t call a cyber attack very smart and sophisticated. But, perhaps calling it that way says more about the competence of the telecom company than about the perpetrators.
Controversial detail is that this is the third hack on the TalkTalk website since February this year.
Apparently TalkTalk is not the only telecom provider with bad IT security.
Final words
The password database gate of Phone House could be exploited by anyone with basic computer skills. You only needed a camera and knowledge of how to use a login form. I hope this story is a wake-up call for everyone who works with computers and handles personal data of others.
As an IT security consultant and professional ethical hacker, I work for many different kinds of businesses every week and analyse their security. I won’t (specifically) name my customers as I’m very loyal to them. But believe me when I say that Phone House and MediaMarkt aren’t the only big companies with terrible IT security. Nowadays it’s actually standard (really!). Only banks and the military have the budget to get the right IT security. Unfortunately even they get very vulnerable on occasion.
Should things be fundamentally changed in our society regarding IT security? Or do we accept the fact that we’re inherently insecure? How about in 10 years time when our houses, cars and human bodies are hooked up to the internet? And what about our critical water, food and energy infrastructures? Oh uh, those have already been connected to the internet.
Update, December 10th, 2015
Via a trusted friend I heard that not too long ago, he noticed that the MediaMarkt in the city of Drachten also uses a very weak password, a similar numeric password as used by MediaMarkt Utrecht. One that can be entered with a fluent finger swipe as well and which isn’t eight characters long 😉
Also, from another trusted source, I heard MediaMarkt Utrecht still uses weak passwords. Phone House seems to be incorrigible on this matter. Or perhaps strong passwords are simply too difficult?
Furthermore, a lot of journalists have recently contacted Phone House to verify my story. Their initial response on the first day of the publication was complete denial; a typical example of damage control by large companies. As media picked up on my story (despite the denial), Phone House soon realized the genie was out of the bottle and admitted to a journalist that names and addresses of customers, and also in some cases a copy of the drivers license and passport could be visible in customer files in internet-facing dealer portals.
The existence of the infamous password Excel file has been confirmed by various readers (#1, #2, #3, #4) on well known Dutch news site Tweakers and also on Twitter and Reddit. More shocking however, is the fact that one reader found out the Excel file was still being used at a particular location last week. Allegedly a MediaMarkt employee anonymously states on onemorething.nl that no security changes have been implemented by MediaMarkt yet (in the specific location he/she works in?). Despite all efforts, the security problem seems to be far from fixed! 🙁
Anonymous comments on Tweakers from (ex) (dealer) telecom employees (#1, #2, #3 #4) who work with these vulnerable systems, show us that MediaMarkt employees were all shocked by the (easy) accessibility of personal details via their computers. They confirmed they had access to millions of records but stated that these records could only be retrieved one-by-one (after performing a simple search for a specific customer record). One comment named the following personal details to be visible in Phone House’s computer systems:
- Name;
- Address;
- Telephone number;
- E-mail address;
- Date of birth;
- Bank account number (without the last three digits);
- (Often) a complete copy of an identity card including the personal state registration number (in Dutch: burgerservicenummer).
In reaction to this blog post many people point out that Phone House (as well as MediaMarkt, probably) is liable to receive a fine of up to ‚¬ 820.000 if this incorrect security situation is still persistent on January 1st, 2016. Since on this date new strict privacy legislation enters into force in The Netherlands which obliges companies to report security incidents. The government then subsequently has authorization to fine companies if a grave violation in protecting personal privacy indeed has been committed.
I might have saved MediaMarkt and Phone House quite a lot of money! Sebastiaan Pouyet suggests on Twitter Phone House should haven given me a ten minute free shopping spree in MediaMarkt. Of course I could never turn down such a tempting offer 😉
Update, December 13th, 2015
It turns out MediaMarkt is not the only one with passwords attached to their monitors. The official Dutch state news organization (NOS) appears to be ‘guilty’ here as well. Luckily, this time I didn’t have to take a picture since a NOS employee had already done so himself and even posted it on Twitter on December 11th, 2015:
The password is Welkom01. The very same weak password Phone House used.
When someone on Twitter notified the NOS employee of this password leak and also alerted him to my (blog) story, he replied by saying that he had already read my story and thought it to be good. Although it had not immediately made him change his own weak password or remove the password-notice that was taped onto his monitor.
Timeline of notable events in password gate
| September 11, 2015 | First observation of the Phone House password gate. Can’t take photo of password file. |
| October 3, 2015 | Second observation of the Phone House password gate. Took a photo of password file. |
| October 4, 2015 | Report the vulnerability to MediaMarkt and telecom operators. |
| October 6, 2015 | MediaMarkt sends threatening (juridical) mail. |
| October 17, 2015 | Validate that password gate is not yet closed. |
| October 22, 2015 | Have coffee with MediaMarkt store director. |
| October 28, 2015 | Have coffee part two: “We patched one store, but we need weeks of more time because of a big patch road trip”. |
| October 30, 2015 | Details about the hacked British telecom provider TalkTalk are published. |
| December 8, 2015 | This story is published. |
| December 11, 2015 | NOS employee posts a picture on Twitter on which you can see his password taped onto his monitor. |
Sites that link to this story
- Softpedia.com
- Net-Security.org
- Security.nl
- OneMoreThing.nl
- Tweakers.net
- Telegraaf.nl
- RadarTV.nl
- SecurityLab.ru
- DasKapital.nl
- BNR.nl (link to Dutch 4 minute radio interview)
- Retecool.com
- NRC.nl
- Reddit.com
- Emerce.nl
- TechSnacks podcast (items starts at 22:20 and ends at 30:20)
- MobielVergelijken.nl
- Ycombinator.com : Hacker News
- Z24.nl
- BOF.nl
- MarketingFacts.nl
- Chip.cz
- MediaMarkt.nl
- SecurityAffairs.co
- FlexBV.wordpress.com
- LatestHackingNews.com






Holy crap, what a mess @sruwhof found: “Personal data of Dutch telecom providers extremely poorly protected”: http://sijmen.ruwhof.net/weblog/%5B..]
Very sharp. Great article! It is, hopefully for a lot of people, very learn-full.
Thank you!
And what a dramatic state of insecurity. Indeed, sadly not the an exception.
Sijmen may have just saved Phone House a potential million euro fine. On January 1, 2016, a new Dutch law introduces general data breach notification obligation and considerably higher sanctions.
Great work on helping this organization fix their (blatant) mistake, but I am afraid the next time we’ll read an article like this it *will* end with a hefty fine.
I certainly saved them quite a lot of money indeed if the situation persisted after January 1, 2016. I think they aren’t aware of that.
Enjoyed reading your story, my compliments!
Thanks a lot Roderick!
Well-written insights by @sruwhof. Forget pentesting and vuln scans. Begin with education, hardening and auditing.
@mboelen Thanks! The human component in information security is often forgotten.
Human factors is the achilles heel of any and all security; we are naive, lazy, sloppy at times, and always will be.
@sruwhof nice find!
@sruwhof Nice catch and great article!
How not to password. Great post on depressing security situation at Dutch telcos, by @sruwhof. http://sijmen.ruwhof.net/weblog/%5B..] (HT @Schellevis)
“I’ve never seen anyone entering password 12345678 in one smooth swipe like this. It really looked cool!” – @sruwhof
Good stuff! A good example of simple social engineering….
The human factor is always the way in….
The biggest security breaches always include some form of social engineering
Almost all technical security measures can be circumvented by its users. And so experienced hackers first target humans in their attack plan.
In my experience, it’s a bad idea to rely solely on password protection. Individual logins will still be shared among workers. Users will always choose a password that is easy to remember and therefore be easy to guess. Enforcing complexity rules doesn’t help because if a password is too complex to remember users will write them down, even when specifically instructed not to. Complexity rules also cause a steep increase in the number of failed logins and subsequent loss of productivity as well as an increase in support calls. Middle-managers often encourage simple logins and security circumvention because of this. People are people and will always look for an easy way out of what they consider pointless hassle.
In a public area like the mediamarkt stores and with personel with a ‘who cares’ attitude it’s frankly impossible to prevent the possibility of password peeking. A smartcard, combined with a login and location/time conditions would be a more prudent approach:
-Have users check-in and check-out of the workplace with a smartcard and password in a restricted access area.
-Have frequent id-card check at check-in.
-Have users athenticate themselves to the shore terminals with the card for every transaction.
-No password usage in public areas.
-Set a very short lockscreen timeout.
-Make sure the smartcard is valid only when checked-in, during shop hours, and in departments assigned to the user.
-Set a fine for missed check-outs or make worked hours without check-out unpayable to the employee.
-Any unintented or malicious use of smartcard or logins will result in termination of contract as well as liability for incurred costs.
-Keep detailed logs of user activity.
Excellent addition!
@sruwhof Unfortunately i believe this is commonplace across the globe – example https://www.oaic.gov.au/privacy-law/commissioner-initiated-investigation-reports/vodafone-hutchison-australia @troyhunt
“As you can see, the password to unlock Media Markt computers was media321. A very strong one!” <= needs sarcasm tag 😛
Haha, hopefully that would be stating the obvious. Or… perhaps you’re right!
Tijd voor een goede Security Awareness training!
Topverhaal, geen verrassing maar grondig aangepakt en gedocumenteerd. Net op tijd opgelost om de meldplicht datalekken te ontlopen. 🙂
Lastig om na te gaan of Phone House inderdaad toegang bood tot 12 miljoen gegevens, maar bizar slordig is het wel http://sijmen.ruwhof.net/%5B..]
@danielverlaan ja PH zegt dus van niet, is inmiddels gedicht dus niet meer te verifiëren helaas…
This is mindblowing:
“Personal data of Dutch telecom providers extremely poorly protected†— http://sijmen.ruwhof.net/weblog/%5B..]
/ht @yoeran
Een goed verhaal voor de donkere winteravonden http://sijmen.ruwhof.net/weblog/%5B..]
Schandalig dat dit nog steeds gebeurt.
Wow. Fijne beveiliging bij The Phone House en portals van telecomaanbieders http://sijmen.ruwhof.net/weblog/%5B..]
Leuk leesvoer. Herkenning in veel punten. http://sijmen.ruwhof.net/weblog/%5B..] #infosec #security #hacking
@tokmetzis Leuk stukkie: Personal data of Dutch telecom providers extremely poorly protected http://sijmen.ruwhof.net/weblog/%5B..]
This shows how crazy simple it could be to access personal data. But good work and he got a cool t-shirt from KPN. http://sijmen.ruwhof.net/weblog/%5B..]
Politie en AIVD kunnen gewoon naar de winkel voor telecomgegevens, is geen hackwet voor nodig. http://sijmen.ruwhof.net/weblog/%5B..]
Lazy employees and passwords, with possible 12 million NL phone subscription data access by anyone! http://sijmen.ruwhof.net/weblog/%5B..]
@MathieuH Is ook leuk materiaal voor een blog van #Arnoud @ictrecht. http://sijmen.ruwhof.net/weblog/%5B..]
@mertenhou @ictrecht inderdaad! Ben benieuwd hoe dit zich gaat ontwikkelen en hoe handhaving toegepast zal worden.
Bizar verhaal over totaal gebrek aan security van klant data door Media Markt en Phone House.WW op post-it in winkel http://sijmen.ruwhof.net/weblog/%5B..]
Great article. What a breach! I really want to know how the CBP will act on this one after januari 1st. Looks to me like a penalty scorer for 810k each.
Its unbelievable that when you act as Ethical hacker with a responsible disclosure, like you did in this case, companies dont even fool themselves but try to threat you! They should like you (no love you) for being a responsible citizen and give you flowers, offer you a job or give you at least your phone for free. Instead, unfortunately, they dont understand cybercrime, think it will not happen to them, dont understand the business impact, dont act on it and even start to threat you. Unbelievable.
Auw! – Personal data of Dutch telecom providers poorly protected: 12+ million records #phonehousegate #SijmeRuwhof http://sijmen.ruwhof.net/weblog/%5B..]
Wow, al je gegevens van je mobiele provider beschikbaar met wachtwoorden als 12345678.. #leukerkunnenwehetnietmaken http://sijmen.ruwhof.net/weblog/%5B..]
@sebastiaan Holy fuck
Goed voorbeeld van extreem slordige omgang met wachtwoorden: http://sijmen.ruwhof.net/weblog/%5B..] (Phone House ontkent toegang tot 12M gegevens)
@Schellevis @PrivacyBaro Telco’s en hun vertegenwoordigers zijn een #security risico
A great write-up of a horrible situation security-wise. http://sijmen.ruwhof.net/weblog/%5B..]
Nice! Passwords to access customer data of each dutch telco stored in Google Docs… What could possibly go wrong? http://sijmen.ruwhof.net/weblog/%5B..]
@xotoxot If it had happened after 1/1/2016, they could’ve been nominated for a fine up to €810k or 10% of annual revenue. Interesting times.
Suwen nagelt zo ongeveer hele NL bedrijfsleven aan de schandpaal. Criminele nalatigheid. #security http://sijmen.ruwhof.net/weblog/%5B..]
Weer een goed verhaal!
Beveiliging van gegevens blijft lastig… maar dit is wel heel erg bizar http://sijmen.ruwhof.net/weblog/%5B..]
Absolutely brilliant blog about serious lack of IT security at a Dutch Telecom reseller #responsibledisclosure http://sijmen.ruwhof.net/weblog/%5B..]
Volgens mij hebben we nog een lange weg te gaan op security gebied.. #mediamarkt #phonehouse http://sijmen.ruwhof.net/weblog/%5B..]
Thanks for this detailed and complete write up. Cool that you managed to make a difference here, hopefully they’ll stick to their recommendations as well. It’s still a bit worrying that a store like phone house even has access to personal information in the first place, I wonder what the telco’s privacy policy and terms and conditions say about that…
It certainly is worrisome that intermediate companies seem to have quite a lot of access to telecom provider data.
Ook bij andere organisaties is security bewustzijn een aandachtspunt. Zie https://lnkd.in/e-MPVJF voor hoe Mediamarkt dit aanpakt. Mooi voo…
Golden story about ‘security’ at (media) stores: http://sijmen.ruwhof.net/weblog/%5B..]
Such poor security practices it’s not even funny anymore: “How I could access 12+ million records #phonehousegate” http://sijmen.ruwhof.net/weblog/%5B..]
Whoa nice article about misconceptions in security by many people: http://sijmen.ruwhof.net/weblog/%5B..]
@Stephanvs this on made it on hacker news. Quite interesting article.
Very good blog about password policies at Mediamarkt, Phonehouse and several NL telco’s. http://sijmen.ruwhof.net/weblog/%5B..]
@mediamarkt_nl @thephonehouseNL do you have any formal security program to prevent these from happening again?
Beveiliging is zo sterk als de zwakste schakel…
Wow!
Great story. No matter how much you invest in security measures, it’s all about the people’s awareness.
Reading the story was like reading an exciting thriller book. Amazing research Sijmen!
By the way, great screenshots!
Schokkend! Ik neem aan dat hier boetes gaan volgen. Klantdata 12 miljoen klanten PhoneHouse vrijwel onbeveiligd: http://sijmen.ruwhof.net/weblog/%5B..]
Words fail.
Just read this post by Sijmen Ruwhof. http://sijmen.ruwhof.net/weblog/%5B..]
Heerlijk stukje leesvoer, hoe o.a. de jeugd met de IOT omgaat. Geef ze eens ongelijk ze maken optimaal en snel gebruik van de dingen die we bieden. Cloudservices, web, socialmedia, iedereen kan erbij en lekker snel. Zij moeten immers elke dag 30 keer inloggen binnen 1 minuut of hun chef begint te brommen waarom het zo lang moet duren. Hoezo geen security? We gebruiken toch “verschillende” wachtwoorden is het weer niet goed 😉
Goed artikel Sijmen en helaas zijn de uitkomsten niet verrassend. Benieuwd of de toezichthouder gaat optreden.
Volgens mij kunnen de toezichthouders pas vanaf 1/1/2016 optreden als de situatie nog onveranderd is. Zou wel een hele mooie eerste case geweest zijn!
Please use proper password policies: http://sijmen.ruwhof.net/weblog/%5B..]
Goed bezig ….
Man man man. Wat een faalpaal van @mediamarkt_nl en @ThePhoneHouseNL http://sijmen.ruwhof.net/weblog/%5B..] #privacy cc @ncilla
Big fat kudo’s for you. Incredible how you handled this, in light / despite all (initial) negative responses. This hopefully increases white-hat hacker friendlyness.
@sruwhof Nice find Sijmen and excellent blog. It’s like they say: retail is detail 🙂
Great story about bad security: http://sijmen.ruwhof.net/weblog/%5B..]
Slechte zaak, goed artikel!
Net op tijd voor de aangescherpte WBP (meldplicht datalekken) die per 1 januari ingaat. Als Sijmen er in januari mee was gekomen dan hadden de gevolgen voor de mediamarkt en de phonehouse een stuk groter kunnen zijn De boetes kunnen hoog oplopen: variërend van maximaal 20.250 euro in de laagste categorie tot maximaal 810.000 euro in de hoogste categorie.
Dit muisje krijgt nog een groot staartje #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
Zullen KPN, Vodafone, T-mobile inmiddels hun wachtwoorden hebben aangepast? http://sijmen.ruwhof.net/weblog/%5B..]
Mediamarkt dreigt klant die tekortkomingen constateert met rechtszaak ipv hem in te huren als consultant http://sijmen.ruwhof.net/weblog/%5B..]
Dit voor veel organizaties een normale werkwijze is. (helaas)
Het onbeheerd achterlaten van een geopend portal komt ook vrij vaak voor.
Daarnaast was het voor deze meneer wel degelijk mogelijk om bij zowel klant als uitgebreide product eigenschappen te komen en aan te passen.
Tja, vind je het gek. Bij elektronicazaken zoals de MediaMarkt is dat meer standaard dan uitzondering. Dat komt omdat er vooral mensen werken met een relatief beperkte kennis van ict. KeePass hebben zij echt nog nooit van gehoord gemiddeld gezien.
Wat is hun kennis? Word en Excel (of in dit geval google docs). Voornamelijk omdat alle omzetlijstjes, planningen e.d. per filiaal ook in excel gemaakt werden. Opzich is het dan vrij logisch dat men ook een excel lijstje maakt voor alle tientallen dealer portals die er zijn met hun wachtwoorden, want uit je hoofd leren is niet te doen.
Telco’s zijn natuurlijk sterren in het delen van onze gegevens.
– Schijnbaar delen ze alle informatie al onderling met elkaar (wtf, waarom? mag dat?)
РZe zijn altijd vrij co̦peratief geweest met het verlenen van persoonlijke communicatie van hun klanten naar de overheid.
– Ze laten in de regel ook buitenlandse veiligheidsdiensten vrij spel hebben binnen hun netwerken.
Dat dit zo makkelijk gebeurd verbaast mij niets.
Aah er is dus niets verandert sinds ik weg ben bij Phone House. Wat een geklooi was dat altijd met die wachtwoord-sheets 😉
LOL… als hij was aangeklaagd, dan had de rechter hem uitgelachen omdat niet die onderzoeker fout zit maar de Media Markt/Phone House de wet overtraden.
Die systemen staan btw wel vaker onbeheerd ongelockt, ook in Rotterdam Centrum.
Beveiliging bij KPN is btw ook niet in orde.. toen de zaak waar ik werkte problemen had met een toestel kon ik rustig met mijn toestel van alles opvragen tot abbo gegevens aan toe en… zelfs een monteur verzoek inplannen terwijl ik belde met mijn mobiel en nee… die is NIET bekend bij KPN.
Dan meld het! Zullen ze erg blij mee zijn, want blijkbaar weten ze hoe ze er mee om moeten gaan.
Eens
Oh. My. God. #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..] #data #privacy
@ncilla Mooi (kuch) verhaal is dat. Laat goed zien wat er allemaal mis kan gaan als je derden toegang geeft tot je bedrijfsgegevens.
Extremely bad but sadly real… http://sijmen.ruwhof.net/weblog/%5B..] by @sruwhof (ping @ncsc_nl)
Niet alleen je ouders zijn “onhandig” met wachtwoorden… RT @ncilla: Oh. My. God. #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..] #data #privacy
Iets met beveiligen van persoonsgegevens. http://sijmen.ruwhof.net/weblog/%5B..] Met een paar kleine aanpassingen is zoveel winst te behalen.
This makes a good case for better security and better passwords… http://sijmen.ruwhof.net/weblog/%5B..]
Hiervoor hoef je geen beveiligingsonderzoeker te zijn.
Was me inderdaad ook al eens opgevallen. Half november mijn contract verlengd bij TPH in de Media Markt en toen kwam er nog gewoon een Excel bestandje tevoorschijn hoor..
Vorige week gedaan en ook gewoon excel documentje. Vond het al wat apart maar lijkt er op dat ze het bij mijn media markt niet op een google drive hebben gedeeld. Wellicht intern op het netwerk.
Neemt niet weg dat dit ook zo zijn veiligheidsrisico’s met zich mee brengt en tevens openen ze zo’n excel zonder blikken of blozen waar de klant naast staan.
Ik mag hopen dat alles ook daadwerkelijk is aangepast, want via de foto’s kun je toch nog aardig wat achterhalen.
Moeilijke wachtwoorden ook! 8)7
Je digitale gegevens zijn zo veilig als de zwakste schakel. http://sijmen.ruwhof.net/weblog/%5B..]
2FA anyone? Is it still so hard to implement a 2nd factor?
2FA would be much better, but also not that user friendly. It would help a lot if IP address filtering was implemented for all portals.
Wat is het wachtwoord. m. Ja leuk hoor lolbroek, even serieus graag. Ik ben serieus, het wachtwoord is m http://sijmen.ruwhof.net/weblog/%5B..] mediamarkt
Very revealing story about how a @mediamarkt_nl customer could access 12+ million records #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
@harmsnaphaan Dit is smullen voor jou Harm: http://sijmen.ruwhof.net/weblog/%5B..]
omg… echt. – how I could access 12+ million records #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
@marcovoets wtf haha pfff 🙂
@Blackout_music Your neighbours have terrible #infosec http://sijmen.ruwhof.net/weblog/%5B..]
Almost Investigational Journalism!
Another reason to not buy a phone: #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
@rolfje are you suggesting any other methods of obtaining a Phone? 😉
@koenbroumels Apple store, simlock free. Then order prepaid sim at a non-phone house provider. For instance. Or second hand phone.
@sruwhof Wow, nice finding
It’s been awhile since i heard such finding from you, Data in US’ Google Docs? What a bumpy privacy!
#infosec
@AbubakarTokaraw Thanks! As I have a very busy professional schedule, it’s hard to find time for unpaid security research.
Even voor de duidelijkheid, enkele gebruikte wachtwoorden waren:
– m
– vodafone14454
– Welkom03
– beginnen01
– msh0041
Jep. Een éénletterig wachtwoord (“m”) werd bij KPN geaccepteerd als wachtwoord voor een portaal met NAW gegevens van bijna alle Nederlandse inwoners. Eén letter.
En dat allemaal óók nog eens in, jawel, Google Drive.
Bron: https://ic.tweakimg.net/ext/i/2000874186.png (feitelijke screenshot van de spreadsheet, afkomstig van Tweakers.net)
Het is gewoon echt diep triest. Security heeft prioriteit 0. Hier faalt management en ICT van zowel KPN, MediaMarkt als ThePhoneHouse. En niet één medewerker die hier ooit vraagtekens bij heeft gezet? Het is een grove schande.
Het klopt helemaal trouwens het schiet mij nu te binnen ik zag dit ook in januari bij Mediamarkt Utrecht, gewoon een excel bestand met inlog gegevens en waren toen zelfs nog ie6 browsers dacht ik zelfs.
Ik was het al even vergeten maar ik zat toen ook al te kijken van huh, ik zij toen al tegen medewerker of gebruik van keepas enzo en hij schreef ook gelijk op zal eens door geven zij die.
Waarom moet dat inloggen met enkel een password? Waarom geen pki-infrastructuur gecombineerd met een tweede factor?
Echt klantdata inzien zit niet in dealerportalen(althans tot enkele jaren geleden), toen waren ze alleen voorzien van raadpleegfunctie na het zoeken van de klant(beperkt tot wel of niet verlengbaar en klant is wel of niet aanmeldbaar en opgegeven adresdata). Laatst in mediamarkt wel meegekregen dat er nu meer info inzit, maar of dat het phonehouseportaal was kon ik niet opvangen.
Maar vind het een goed verhaal, log is aanrader. Mooie mix tussen ervaring, probing en ook de ethische en juridische grenzen die in de gaten gehouden worden.
Klantdata inzien is redelijk eenvoudig werkt bij iedereen hetzelfde.
Zoek de huidige klant op: postcode of achternaam met plaats (wat vaak lastig is omtrent bakker nogal wat voorkomt)
dan zeg je verlengen en het eerste wat die vraagt “Kloppen adres gegevens nog…”
En je krijgt zo alles van de klant in beeld.
Heb zelf jaren mobiele abo’s verkocht vanuit een 3rd party en het zal je verbazen hoeveel gegevens je kan opvragen.
Het artikel doet het alleen wat erger lijken, ja je hebt toegang tot miljoenen klanten maar je moet ze wel 1 voor 1 opvragen.
Heb dan ook niet de illusie dat dit met andere digitale gegevens van mij/over mij wel beter gaat.
Google Drive… Zo maken ze het voor de veiligheidsdiensten wel héél makkelijk om alles in te zien…
Dutch telecom retailer @ThePhoneHouseBV screws up badly. Millions of NL citizens’ data compromised. #phonehousegate
Weer een mooi artikel, jammer dat er nog veel organisaties zo met onze persoonlijke gegevens omgaan
.@sruwhof toont zwakke schakel aan in beveiliging klantgegevens van mobiele providers. Interessant maar zorgwekkend!
http://sijmen.ruwhof.net/weblog/%5B..]
Lees en huiver. De menselijke kant van beveiliging (persoons)gegevens. http://sijmen.ruwhof.net/weblog/%5B..]
Tsja….we zijn er nog lang niet. Wel geniaal geschreven stuk. http://sijmen.ruwhof.net/weblog/%5B..]
Wow. Long but interesting read. How secure is our data, really? http://sijmen.ruwhof.net/weblog/%5B..] #phonehousegate #data #security
http://sijmen.ruwhof.net/weblog/%5B..] Bizarre faal van @ThePhoneHouseNL / @mediamarkt_nl. Gevalletje voor @geenstijl..
Must read. Echt een MUST-READ! RT @ncilla Oh. My. God. #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..] #data #privacy
How @sruwhof hacked a bunch telcos in one blow: http://sijmen.ruwhof.net/weblog/%5B..]
@okoeroo Sportief! 😉
@helpnetsecurity @ZeljkaZorz @sruwhof Very good article.
Top Sijmen geeft duidelijk aan waar te verbeteren
Ik kan hier volledig over meepraten en ik kan zeggen: die wachtwoorden zijn nog steeds zo. MediaMarkt doet hier helemaal niks aan en er zijn nergens password managers geïnstalleerd. Daarnaast werken ze bij de PhoneHouse met zo’n oud systeem om hun abonnementen af te sluiten, dat ieder kind van drie dat kan hacken. Kortom het is nog altijd een zooitje bij beide bedrijven wat betreft klantengegevens.
@sruwhof Strakke actie. Zijn onze gegevens in ieder geval weer een beetje veiliger…
@Piratenpartij Dank! Ik doe mijn best. Echter, als ik alle reacties lees, schijnen de problemen nog steeds niet helemaal opgelost te zijn(!)
Leest als een spannend boek! http://sijmen.ruwhof.net/weblog/%5B..]
Well done Sijmen! Show the leaks and give the remedy. That’s ethical hacking.
For me is also a riddle solved when Obama (POTUS) and Xi Jingpin (China) promised to hack each other less. I thought first that ‘less hacking’ was a soft statement. But, after I read your blog I understand now: a promise to stop to hacking completely, that is impossible. It will go on when and where the guard is down. It needs an everlasting screening by every company or government.
Nice read.
Unfortunately, the password advice in this article is the usual bad practice: let’s create passwords that are almost impossible to remember (so people are encouraged to use those PostIt notes), yet, still easy for computers to guess by brute force.
Instead, a password consisting of four or five random normal words is much easier to remember and much harder to track.
xkcd says it much better than I ever could: https://www.xkcd.com/936/
I’m a fan of XKCD.
Reads like a modern day horror story. Did you see this, @troyhunt ?
must read, fine written too, about the disaster that is password policies. Will use this in class. cheers @sruwhof
@ricobrouwer Thanks Rico! Great to hear it’s useful in classrooms.
this has to be the most bizarre thing i’ve read in a long time concerning security concerns in public.
@sruwhof Mooi gedaan!
Phone House massacres security and customer privacy in the NL. Is it mayhap as bad here in Sweden? @PhoneHouseSWE
Phonehouse en Mediamarkt maken er een zooitje van. http://sijmen.ruwhof.net/weblog/%5B..]
I’m glad they use really strong password like media1234. #mediamarkt phonehouse #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
http://sijmen.ruwhof.net/weblog/%5B..] Well at least its not just CPW in the UK then
http://sijmen.ruwhof.net/weblog/%5B..] – How you should not handle security
Zo, het duurde blijkbaar een tijde totdat @mediamarkt_nl doorhad wat privacy bescherming eigenlijk is. #Utrecht http://sijmen.ruwhof.net/weblog/%5B..]
Lesje data security> En zo lagen 12 mio NL telefoonabo’s op straat > http://sijmen.ruwhof.net/weblog/%5B..]
Wauw.. mooie read-up over gigantisch datalek bij @mediamarkt #ShameOnYou
http://sijmen.ruwhof.net/weblog/%5B..]
Interesting write up on the lack of security of Dutch telco’s http://sijmen.ruwhof.net/weblog/%5B..]
Helaas herkenbaar: Epic failure of Phone House & Dutch telecom providers to protect personal data. http://sijmen.ruwhof.net/weblog/%5B..]
Interesting read about basic password and security screwups in telecoms industry. http://sijmen.ruwhof.net/weblog/%5B..]
Gaat lekker daar bij PhoneHouse
Personal data of Dutch telecom providers extremely poorly protected #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
I wonder how NZ telecom retailers would measure up? Are their systems any better? http://sijmen.ruwhof.net/weblog/%5B..]
Epic @PhonehouseHelpt fail http://sijmen.ruwhof.net/weblog/%5B..] should have used #QtPass
Schandalig, indien waar RT @Schellevis: Goed voorbeeld van extreem slordige omgang met wachtwoorden: http://sijmen.ruwhof.net/weblog/%5B..]
Security,zo gaat het zo episch fout – Epic failure of Phone House & Dutch telecom providers to protect personal data http://sijmen.ruwhof.net/weblog/%5B..]
Well, this is rather embarrassing; “Epic failure of Phone House & Dutch telecom providers to protect personal data” http://sijmen.ruwhof.net/weblog/%5B..]
Basically failing on basic computer security, because no one bothered to get it sorted, or no one cared until it was pointed out to them.
Seriously, read the whole thing, it’s a compounding facepalm, LOL
twee mooie artikelen over computerbeveiliging voor niet it’ers https://decorrespondent.nl/3708/Eerste-hulp-bij-hacken-de-lessen-die-ik-heb-geleerd/ … en http://sijmen.ruwhof.net/weblog/%5B..]
“He didn’t remember the login password, and, here it comes, on the screen he opened an Excel file which contained all their passwords.”
You have got to be kidding me…
Amazing write up by the way, really interesting.
In plain text? Dear god.
I had a (shared, front desk) secretary with such an excel file once… she walked in to my office on my second to ask my password so she could write it down because ‘people keep forgetting them’.
Shocking thing was all other people (about 20) working on that floor never raised an eyebrow about this practice. Some dislike me to this day because I had them all forced to make a new password and had the secretary re-evaluated.
You cannot force people to care about security. If someone doesn’t care about security, and you give them a password to remember, they’ll write it on a post-it note. If you give them 20 passwords to remember, they’ll organize them whichever way is most convenient.
(Password manager? They’ll write down the master password for it. Still an improvement since now you have to actually use the computer to get the passwords, instead of just passively observing)
I think these people usually don’t care simply because they’ve never seen any consequences come from not caring. (Perhaps because such consequences are rare; how many years do you think Media Markt were doing this before someone took advantage?)
That is 12M records on a population of 17M people.
Well, they cover all mobile phone providers, so those are all the non-roaming and non-prepaid phones, so in other words, all contracted people in the Netherlands.
I loved the part where he typed in 12345678 in one swipe
It’s the 1980s “slide to unlock” 😉
that is hilarious!
for shits and giggles I tried, and it takes some practice.
It depends on the keyboard. It’s super easy to do on flat laptop keyboards, but harder to do on a keyboard where the keys have a bit of height.
This is terrible. I’m really glad they are changing the Wet Bescherming Persoonsgegevens to include an obligation to inform people when their personal information has potentially leaked.
If I understand the law correctly, this incident would mean a letter on the door of every dutch person under next years law. (Although one could argue that OP actually had to have logged in on these systems.)
Not necessarily, the law says that they need to report it to the CBP. From there on investigation will be done whether the data of the people has been compromised. They should be able to confirm this with the logs and since the researcher reported this problem openly there is a chance this won’t have to be reported to the end-user. This means it would depend on the logging of each individual telecom provider. One provider might be able to prove nothing happened while the other is unable to.
Goed gedaan! Mooi opgeschreven ook.
Gotta love these password spreadsheets! Very nice writeup, very good story telling.
Very awesome writeup! Kudos!
It is my duty as a Belgian to laugh at the Dutch: hahaha.
Quite amazing though. Makes me wonder how many big hacks have been as ‘simple’ as this one…
Quite a few.
As a fellow Belgian I want to go to Media Markt tomorrow
I’d wager at least 60% of big data accesses did, or could have, come from simple “social engineering” like this, to use the jargon.
Wouldn’t surprise me if Belgian retail chains had the same issue. Don’t Belgacom stores have the pc’s right in the store too, ready to be exploited when the sales employee is distracted?
As a fellow Belgian I can assure you, we’re dealing with similar issues. To give you an example. At this point I’m finishing up a private vulnerability disclosure for one of our bigger telecom companies. It’s a bit more technical than OP, but nonetheless quite bad..
Will you be able to post it somewhere in the future? Sounds like something I’d want to read 🙂
It does include a responsible disclosure section, which means I will post it in the future, after making sure they somehow fix it. Also, because they’re a telecom company, they’ll have to notify every party of the flaw, consequences and risks that occurred. I’d be surprised if it doesn’t leak out before I can write my own post about it, but we’ll just see how long it’ll take for them to act. At this stage I’m just making sure that the head of security is receiving all of the necessary information in a secure fashion for them to act and fix the issues. 🙂
Isn’t the Phone House originally a Belgian chain or am I mixing them up with someone else?
Originally English. Phone House Belgium was acquired by Belgacom a few years ago.
En dit komt dan niet in het nieuws?
Niet in het nieuws??
NRC
Tweakers
De Telegraaf
Just to name a few..
@sruwhof Amazing story Sijmen! Thanks for sharing
Goed verhaal! Bedankt @ThePhoneHouseNL & @mediamarkt_nl http://sijmen.ruwhof.net/weblog/%5B..]
Dramatische beveiliging van 12 miljoen persoonsgegevens bij Phone House en telecomproviders. http://sijmen.ruwhof.net/weblog/%5B..] #phonehousegate
Hmm, nice Catch http://sijmen.ruwhof.net/weblog/ @sruwhof how NOT to protect our personal data! #password #12345678 with one swipe 🙂
Bizar hoe slordig sommige bedrijven omgaan met hun wachtwoorden: “How I could access 12+ million records” http://sijmen.ruwhof.net/weblog/%5B..]
It’s getting worse: Epic failure of Dutch telecom providers to protect personal data: access to 12+ million records http://sijmen.ruwhof.net/weblog/%5B..]
Epic story of several Dutch telecom providers and their security blunders. http://sijmen.ruwhof.net/weblog/%5B..]
http://sijmen.ruwhof.net/weblog/%5B..] This is so bad I’m having trouble sitting still.
Comedy gold!
Afgezien van de waardeloze beveiliging betekend dit blijkbaar dat elke verkoper in een telecomwinkel de NAW gegevens van iedereen met een abonnement kan inzien? Dat lijkt me nog veel erger dan dit gebrek aan beveiliging.
Moeilijk wachtwoord om in te loggen op mijn werk?….. Ik ben toch zeker niet gek!
Zolang snelle verwerkbaarheid voor alle werknemers prevaleert, boven tijd/geldrovende inlog procedures.
Word het nooit wat met data sanity in Nederland.
Ik verwacht dat het grosso modo van MKB ook gebruikt maakt van luizige wachtwoorden.
Veiligheids denken zit niet ingebakken in de cultuur, Ook niet in veel individuele gebruikers.
Inloggen wordt gezien als een vervelende/tijdrovende bezigheid.
Eenmaal ingelogd hou je dus je venster open.
Dat dit nu pas naar boven komt….
Al vele jaren zijn die dealers portals van telecomproviders slecht beveiligd.
En dat is niet het enige.
Zo was enkele jaren geleden een webservice van een telecomprovider voor een behoorlijke tijd onbeveiligd omdat een certificaat niet wilde werken.
Iedereen kon zo met wat simple handelingen van alles doen, mits je de deeplink had.
Maar zodra er maar iets fout gaat bij een dealer, dan werd je nog net niet voor een vuurpeleton gezet.
Zo ook die prijswijzigingen van abbo’s in de afgelopen jaren..
Wist van alle providers al weken, soms zelfs enkele maanden van te voren dat de prijzen werden verhoogd.
Maar er is geen sprake van prijsafspraken volgens onderzoeken…bullshit…corrupte bende die telecomwereld.
2FA scheelt..
En dan adverteren met “ik ben toch niet gek…”
“Door Anoniem:Zolang snelle verwerkbaarheid voor alle werknemers prevaleert, boven tijd/geldrovende inlog procedures. Word het nooit wat met data sanity in Nederland.
Je kaart exact de root-cause aan. Waarom moet security met tijd/geldrovende inlog procedures gepaard gaan?”
Als je veilig en niet tijdrovend kan krijgen tegen acceptable kosten dan kan het wat worden. Begin met risico/impact….
Waar blijft die benadering?
Very cool write-up!
Excellent article and great reporting! I’m actually not surprised at all of such a blatant security risk. This is something to be expected from a shared computer on a retail floor with a few shifts a day using the same terminal. I’m actually shocked that this was not exploited earlier.
Nice article, as said before it reads like a good book. Good to hear KPN improved their game recently.
Thanks Barry!
Take good care of the T-Shirt. It’s a collectable ;-).
I certainly will! From what I know only a very small amount of people got the t-shirt, so I’m proud of it! 🙂
As old employee its no surprise for me… there is no IT department in MM, no documentation or procedures. Most of IT maintenance is done on the fly by managers with no idea,knowledge or IT experience … the internal network is network is not secured at all, some random devices, (wireless routers,switches, NASes) are hooked up to the internal network… The PC’s run windows 7(single machines with XP)with no patches, POS run on outdated custom linux distro… CMS is very outdated(like 90s)
It comes to surprise me that after 3+ years the password media321 is still in use… I’m sure that most old system passwords are still in use.
You all know this is not a media markt problem, right?
In my opinion:
1) Password is obsolete;
2) Usually only one or few logins are provided to retail stores;
3) Stores use several different portals;
4) Store employees rotate quite quickly – many times no training is provided and no bother memorizing useless passwords.
5) Stores want to sell, no burocracy – all they care about is money;
6) Mobile operators want to sell – all they care about is money;
This said, no one cares about customer data protection unless you can get a really big fine. Sorry that your data was caught in between this process.
Protection will not be provided by default as it will cost mobile operators/stores money and will make selling process more bureaucratic, which means that you may loose a customer for an operator with a less bureaucratic/easy process.
Sterk verhaal over de menselijke kant van security, goed beschreven en deze organisaties mogen dankbaar zijn voor deze gedegen aanpak van Sijmen Ruwhof.
Dit verhaal doet Diginotar verbleken. Een goed geschreven verhaal over ‘the state of the practice’ op security gebied bij Mediamarkt en Phonehouse door Sijmen Ruwhof. Ik wil iedere dag wel zo’n verhaal lezen, failliet gaan is hun enige straf 😉 http://sijmen.ruwhof.net/weblog/%5B..]
Goed bezig, Sijmen!
Sterk Sijmen!
It would be interesting to see if using the in-store Wifi allows you to bypass the IP-level blocking.
That would certainly be interesting! Especially if customers are granted access to that WiFi channel.
Interesting read. But are you sure KeePass is safe?
http://www.blackmoreops.com/2015/11/04/anti-hacking-tool-got-hacked-keefarce-can-break-your-keepass-password-safe/
Interesting link, thanks! I’m unfamiliar with the linked research and going to study it.
I have come across this article before. It changed my mind about Keepass.
Good story of what would have been called a sophisticated attack… http://sijmen.ruwhof.net/weblog/%5B..]
Should we give up the idea that personal data is safe w/big companies,their staff,contractors,etc.? @ThePhoneHouseNL http://sijmen.ruwhof.net/weblog/%5B..]
Oh boy… http://sijmen.ruwhof.net/weblog/%5B..] #security #cleartext #password #whitehat
Wow! Check this out: http://sijmen.ruwhof.net/weblog/%5B..] an ethical hacker just hacked on of the biggest mobile resellers in The Netherlands!
Very interesting story about IT security. Security awareness on all levels in an organization is critical http://sijmen.ruwhof.net/weblog/%5B..]
Slordig omgaan met klantinformatie door makkelijk te bereiken wachtwoorden. goed verhaal! http://sijmen.ruwhof.net/weblog/%5B..]
Security, or the lack thereof… http://sijmen.ruwhof.net/weblog/%5B..]
voor een ieder wie diens veiligheid dierbaar is:
LEZEN!!! http://sijmen.ruwhof.net/weblog/%5B..]
Well worth a read. http://sijmen.ruwhof.net/weblog/%5B..]
Insightful and a bit shocking: “Epic fail to protect personal data: I could access 12+ mio records” #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
There’s a product waiting to be developed for easier sharing of passwords: http://sijmen.ruwhof.net/weblog/%5B..]
@DrWhax Jaw-dropping. But there’s no technology solution for an idiocracy.
passwords of Dutch telcos stored in clear on Google Docs, and other epic fails http://sijmen.ruwhof.net/weblog/%5B..]
Humans are the weakest link, but the lack of *enforced* policies contributes to the problem as well: http://sijmen.ruwhof.net/weblog/%5B..] #infosec
@blaskov Really interesting story. Thanks for sharing.
An … interesting … real life case of #security #pebkac #snafu by @sruwhof http://sijmen.ruwhof.net/weblog/%5B..]
Oh god. How could these people be SO BAD!? http://sijmen.ruwhof.net/weblog/%5B..]
Sijmen hackt the phone house vrij gemakkelijk #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
Deze al gelezen? Hoe The Phone House en Media Markt een potje maken van de bescherming van gegevens van klanten. http://sijmen.ruwhof.net/weblog/%5B..]
Media Markt: ik ben toch niet gek…
How I could access 12+ million records | http://sijmen.ruwhof.net/weblog/%5B..]
Met dank aan @ThomasMarzano
@zoisdat_ Ben er nog steeds beduusd van @ThomasMarzano
@Tactloos echt waanzinnig gewoon, hoe slecht Media Markt dit handelt
@zoisdat_ De ISP’s ook. Portals zonder enige vorm van beveiliging???
@Tactloos tja de slogan kunnen we bevestigen, ze zijn gek @mediamarkt_nl
@zoisdat_ Dat zeker, en dan nog gaan dreigen ook als ze er op gewezen worden @mediamarkt_nl
@Tactloos slechte PR dit. Kat in het nauw maakt rare sprongen. @mediamarkt_nl
@zoisdat_ @Tactloos @mediamarkt_nl Mediamarkt weer es een stunt gebakken lees ik?
@FlopOV ja en niet zo’n charmante @Tactloos @mediamarkt_nl
Dutch professional #hacker @sruwhof putting on a clinic in store-level #retail insecurity: http://sijmen.ruwhof.net/weblog/%5B..]
OMG Epic Fail can’t even begin to describe it http://sijmen.ruwhof.net/weblog/%5B..]
“12 miljoen gegevens van Nederlanders op straat” | http://sijmen.ruwhof.net/weblog/%5B..] @ZiggoCompany @tmobile_webcare hebben jullie stappen ondernomen?
Wow. How a hacker could access 12 million telecom records, from a public terminal in Media Markt. http://sijmen.ruwhof.net/weblog/%5B..]
Data security horror story in NL: http://sijmen.ruwhof.net/weblog/%5B..]
Interessant verhaal over een onderzoeker die toegang kreeg tot miljoenen persoonsgegevens van @ThePhoneHouseNL. http://sijmen.ruwhof.net/weblog/%5B..]
Intersting read about Dutch telecom records and security 🙂 http://sijmen.ruwhof.net/weblog/%5B..]
@ThePhoneHouseNL Ich bin toch niet gek? Tsss… 10.000.000 customers leaked #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
http://sijmen.ruwhof.net/weblog/%5B..]
En dit is er mis met data beveiliging. #Gebruikers
Mind is blown na het lezen van dit artikel (en hoe zit het in België…?): http://sijmen.ruwhof.net/weblog/%5B..]
@roelvangils Bizar inderdaad.
Recommended read; dutch hacker uncovers bad policys and a lot of private phone data. http://sijmen.ruwhof.net/weblog/%5B..]
Article on Hacking Dutch telecom providers & Social Engineering in the MediaMarkt http://sijmen.ruwhof.net/weblog/%5B..]
Accessing 12+ million records: A security tale.
http://sijmen.ruwhof.net/weblog/%5B..]
#hacking #cybersecurity
Oeps #mediamarkt #phonehouse http://sijmen.ruwhof.net/weblog/%5B..]
Wauw, daar zakt de broek van af – http://sijmen.ruwhof.net/weblog/%5B..] #security #fail
@sruwhof heeft wel een minuutje of tien gratis shoppen in de @mediamarkt_nl & @ThePhoneHouseNL verdiend!
@srpouyet @mediamarkt_nl @ThePhoneHouseNL Mee eens! 😉
Ter voorbereiding @sruwhof: http://www.trending.nl/artikel/opmerkelijk/deze-belg-mocht-100-seconden-gratis-winkelen-in-de-media-markt … 😀 @mediamarkt_nl @ThePhoneHouseNL
@srpouyet @mediamarkt_nl @ThePhoneHouseNL Dat zou wel een *hele* positieve draai geven aan het verhaal voor hun. Ben benieuwd!
@srpouyet @mediamarkt_nl @ThePhoneHouseNL En ook voor mij trouwens haha :D. Mooi filmpje trouwens!
http://sijmen.ruwhof.net/weblog/%5B..] Zoveelste voorbeeld van het niet hebben van een legitiem doel voor het hebben/verwerken van persoonsgegevens… \-:
@VogonCaptain dat was best een stuk tekst…, wel leerzaam 😉
Wees op je hoede en gebruik ajb een wachtwoord manager (be viligant & use password manager)! http://sijmen.ruwhof.net/weblog/%5B..] #Security #PersonalData
I don’t regular read a whole blog this size… but this is a good one: Epic failure of Phone House & providers http://sijmen.ruwhof.net/weblog/%5B..]
This is a must read for anyone struggling to get people to take information security seriously. http://sijmen.ruwhof.net/weblog/%5B..]
Geweldig verhaal van deze vriendelijke hacker die security fuck-ups bij Phone House en Mediamarkt probeert te fixen. http://sijmen.ruwhof.net/weblog/%5B..]
@RogerBloem prachtig om te lezen.
@martinbal92 @RogerBloem Thanks mannen!
@sruwhof @martinbal92 jij bedankt! Goed werk en awesome story.
Hoe #SijmenRuwhof de hele wereld hackte. Met dank aan de #Mediamarkt in Utrecht. http://sijmen.ruwhof.net/weblog/%5B..] #phonehouse #data #privacy
Wow! – “Epic failure of Phone House & Dutch telecom providers to protect personal data” #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
Great story and example of #whitehat #hacking in action, in the Netherlands. Kudos for his patience & perseverance! http://sijmen.ruwhof.net/weblog/%5B..]
Ah, wunderbar, ein PostIt mit Passwort und auch sonst alles was dazugehört: http://sijmen.ruwhof.net/weblog/%5B..] #ScheißDieWandAn
Onveilige praktijken in een winkel leiden tot groot datalek: http://sijmen.ruwhof.net/weblog/%5B..] #phonehousegate hat tip: @skoopnl
It would be very cool if the government could fine businesses for negligence like this, and even better if they would reward those who report it, which they could pay out of the fined amount of course. That way the reporter doesn’t have to deal with the stress of being threatened by a lawsuit, and the company always knows the reported problem is something they have to respond to seriously.
Right now there is only form of pressure on these companies: Selling phones and subscriptions with as little overhead as possible, and they’re all struggling to do so.
It also is a bootstrapping problem, right now companies just don’t know about security best practices. It was probably some 16yr old store employee who suggested they use google docs to sync their passwords in the first place. If they new of a better way to do it I believe they would have, but there’s no incentive to figure that out. If good security practices were more commonplace in all businesses then they wouldn’t struggle so much with doing the right thing.
Excellent article and reporting! I’m actually not surprised at all of such a blatant security risk. This is something to be expected from a shared computer on a retail floor with a few shifts a day using the same terminal. I’m actually shocked that this was not exploited earlier.
I wonder if what these companies are (not) doing is actually a crime under the European personal data protection laws?
original site appears down for me. Wayback link: http://web.archive.org/web/20151208100120/http://sijmen.ruwhof.net/weblog/608-personal-data-of-dutch-telecom-providers-extremely-poorly-protected-how-i-could-access-12-million-records
I just bought my new phone and subscription through those companies. Very happy there are people like Sijmen out there fighting the good fight.
This one’s a painful and interesting read – shared account passwords in an unencrypted Google Doc is just the start: http://sijmen.ruwhof.net/weblog/%5B..]
Epic failure #hack #phonehousegate | http://sijmen.ruwhof.net/weblog/%5B..]
read this article on security http://sijmen.ruwhof.net/weblog/%5B..] #mediamarkt
@bertboerland qua adviezen niks nieuws, wel grappig om te zien hoe je partners je beveiliging te grabbel kunnen gooien als je niet monitort
@Maarteuh @bertboerland De adviezen zijn inderdaad niet nieuw, maar blijkbaar wel zeer onbekend bij het grote publiek!
@sruwhof @bertboerland ja, maar vooral ook eng om te zien hoe weinig grip je dus op je beveiliging hebt als je partners hebt
@haroldteunissen wat een verhaal ppfff
YOLOOOOOOOO
just wtf
@sruwhof ik heb met veel plezier je weblog gelezen en zal je beschreven casus zeker gebruiken voor security awareness doeleinden
@OlofDieckhaus Leuk om te horen! We hebben nog een hoop te doen als het gaat om beveiligingsbewustzijn.
@sruwhof alle waardering voor je werk!
(we may need to talk one day tho…)
Dank!
>A curious detail was that the Excel password database was stored on Google Docs and the login details of their Google Account were also in front of me. Neat! I could lookup their passwords anytime I wanted from any computer in the world.
psh, data-security is only for geeks.
fun read, thanks
I challenge /g/ to social engineer their own local electronics store like this. Careless employees should be carelessly fired.
Damn this shows that we have too many retarda in the world.
Interesting read about the importance of proper password tooling and staff education. http://sijmen.ruwhof.net/weblog/%5B..]
Interesting read about the importance of proper password tooling and staff education.
OMFGWTFBBQ
Shall we all, for now and forever, agree to stop using passwords starting with ‘welkom’?
I cant take writer/journalist serious IF he/she uses The Word epic in The headline.
This is a great story about a bad situation.
I was impressed that the author waited for the company to fix things before publishing results.
Het programma van Radar op tv gisteravond was ook interessant over het doorgeven en opslaan van medische gegevens.
Je bedoelt vast de uitzending van Zembla over ‘Data: het nieuwe goud II’? Die is inderdaad erg sterk en een aanrader!
http://zembla.vara.nl/seizoenen/2015/afleveringen/09-12-2015
http://zembla.vara.nl/seizoenen/2015/afleveringen/02-12-2015
Of course, in the olden days we had “telephone books” that were easily hackable and they contained the names, addresses and phone numbers of just about everybody.
Yeah, these were the good old days, for stalkers and detectives 😉
I`ve had the same thing happen to me once in a phonestore. I told the employee that i could see all the passwords and even personal information of the customer he served before me. The guy turned out to be the storemanager, and he instantly sent an e-mail to all the store employees telling them te be more carefull and lock their screens when they walked away from the computer. A few weeks later i was in the same store again to pickup a phone i brought in for repairs. And i watched some eployees as they were walking away from their pc. All of them locked their screens and none of them had a password file open. 🙂
Good journalism&hacking, great article. Just one nitpick: I wish people would stop perpetuating the myth that the TOR-network is safe or anonymous. This is especially odious coming from someone with computer-security knowledge.
I’m very familiar with the shortcomings of Tor. If used with the right precautions, Tor can be quite anonymous. To become really anonymous, you should definitely read about the Tor do’s and don’ts; if using Tor, RTFM 😉
leuke bevindingen!
Thanks for this terrific story!! This was one of the best written articles I´ve ever read (all categories included). I am myself a retired IT manager so it was more ‘hitting close to home’ over it. It was at the same time interesting, amusing and scary. With this Hollywood-like Happy Ending, someone could make a movie out of this 🙂
Really brilliant!
Really awesome to hear Leif! Thanks a lot!
People ask why I try to protect my personal data, but given data security practices like these, is it any wonder? http://sijmen.ruwhof.net/weblog/%5B..]
Hey Sijmen, heb je op BNR gehoord. Het waren in eerste instantie toch alleen naw gegevens, niet?
Oh, en top artikel!
Had je het live op BNR gehoord? Leuk om te horen dat je het verhaal waardeert!
Volgens een anonieme Tweakers gebruiker betrof het de volgende gegevens:
– Name;
– Address details;
– Telephone number;
– E-mail address;
– Birth date;
– Bank account number (without the last three numbers);
– Often a full copy of an identity card including governmental person number (in Dutch: burgerservicenummer).
While the tech world worries about weak crypto bills, NSA-style dragnets, most people still use 123456 on a sticky. http://sijmen.ruwhof.net/weblog/%5B..]
Personal data of Dutch telecom providers extremely poorly protected http://sijmen.ruwhof.net/weblog/%5B..] Amazing (yet simple, so it seems..) job, Sijmen!
Thought your data was safe with your phone provider? Think again… http://sijmen.ruwhof.net/weblog/%5B..] #privacy #horrorstory
Se vad “lite” okunskap kan leda till… http://sijmen.ruwhof.net/weblog/%5B..]
Interesting article about a huge security vurnability at a dutch telecom dealer! http://sijmen.ruwhof.net/weblog/%5B..]
Number of Lessons learned since @Snowden: null, zero, nada, niente! http://sijmen.ruwhof.net/weblog/%5B..]
This is a good example of how bad security can really be when it comes to password management. http://sijmen.ruwhof.net/weblog/%5B..] *nudges @moonspook*
Read and weep. @sruwhof shows what a joke security at Media Markt and the Phone House is. Scary. http://sijmen.ruwhof.net/weblog/%5B..]
I don’t share a blog often but when I do it should bring tears to the eyes of an IT professional! @sruwhof @hacks http://sijmen.ruwhof.net/weblog/%5B..]
@SGgrc Here is one epic story for the “Doing it wrong.” http://sijmen.ruwhof.net/weblog/%5B..]
Good practice by @sruwhof: alle NL klantgegevens en kopie ID zichtbaar via computers @PhonehouseHelpt @mediamarkt_nl http://sijmen.ruwhof.net/weblog/%5B..]
#Security risk #1: people. #privacy #fail Great writeup by @sruwhof http://sijmen.ruwhof.net/weblog/%5B..]
Great post on hacking risks & responsible disclosure from @sruwhof http://sijmen.ruwhof.net/weblog/%5B..] More companies need to sort out basic security!
http://sijmen.ruwhof.net/weblog/%5B..] wow…
People wonder why some of us are so-called “paranoid” about #data #privacy? http://sijmen.ruwhof.net/weblog/%5B..] heads should (but won’t) roll for this
Thanks @blepharon – I was in @Selfridges recently. Customer emails & private data handed to me on a pad so I could add mine! I declined.
@jamesfreedman @Selfridges did you report them to @iconews? Not that ico would DO anything, but it’s important to go through motions.
@blepharon I didn’t. Perhaps someone on their social media team will seize the initiative & contact me…
“Oeps” dekt de lading net niet… “Epic failure of Phone House & Dutch telecom providers…” http://sijmen.ruwhof.net/weblog/%5B..]
@cataspanglish illustrates some bad security practice http://sijmen.ruwhof.net/weblog/%5B..] #insafe2015 ethical hacking!
Well written story about Phone House’s password insecurity: http://sijmen.ruwhof.net/weblog/%5B..] (via @Martijn02)
Great read – Hopeless failure of Dutch telecom providers; could access 12+ million records #cybersecurity #infosec http://sijmen.ruwhof.net/weblog/%5B..]
Oops > Epic failure of Phone House & Dutch telecom providers to protect personal data #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..]
Very good read on #phonehousegate http://sijmen.ruwhof.net/weblog/%5B..] Recommending the LogIn Security Do´s for a lot of shops with service desks.
You should read the whole description of the #phonehousegate . Not sure it can be worse.
Ei näin, ikinä! (Asiakas-)data on aarre ja sen #tietosuoja tärkeintä luottamuspääomaa #Privacy #Security #Digitalist
Ja het kan beter, maar ik betwijfel of @sruwhof ooit zelf in een winkel heeft gestaan, iedereen loopt zomaar langs. Het is geen kantoor.
Wat @sruwhof vergeet is dat verkopers ook gewoon moeten verkopen. Als er 10 klanten rond je nek staan, waar blijf je dan met je security?
@W00fer De essentie is dat een commercieel bedrijf de persoonsgegevens van anderen te grabbel legt. Verkoop gaat niet voor beveiliging.
@sruwhof Dat is te kort door de bocht en dat weet je zelf ook. Beveiliging mag nooit ten koste gaan van operationele bedrijfsvoering.
yes. it’s that easy in many cases. everybody dealing with customer data should take notice.
Thank you for your delightful write up.
You acted with integrity and even some additional style.
I believe the Dutch telecoms industry owes you a lot more than a chance to raid a store. The EUR800k fine is a lot less than what the damages to industry could have been if so many users details could be misused.
The least they can do is offer you free lifetime subscriptions, calls, SMS and data from EVERY network provider to do with as you see fit (it has no marginal cost to them). Then they should put in trust enough money between them that will grant you a EUR1000/month until your 65th birthday and send you a polite thank you card every years with an eloquent request from grateful beneficiaries that you might let them know if you spot any other security issues in any of their operations while they do their best to provide you with service as a regular customer (no special flags on your file or treatment to make it look like they are doing more than they are).
You saved their bacon and were nice about it, they should cover some of your rent and communications costs (remember to remind them about the fiber connections :-).
Weer een prachtige ontdekking van Sijmen Ruwhof. Gedurende mijn stageperiode bij Rabobank ICT heb ik de kans gehad om van zijn denkwijze en ervaringen te leren! (I still do ) ” Personal data of Dutch telecom providers extremely poorly protected: how I could access 12+ million records #phonehousegate
How store employees carelessly handle customer data: @sruwhof was able to access 12+ million records http://sijmen.ruwhof.net/weblog/%5B..] #passwordgate
Goed artikel over hoe beveiliging niet moet…
Ook bij de NOS ontkomen ze niet aan “Welkom01†(briefje op scherm) https://twitter.com/matijn/status/675180723259752448
@raymonmens @matijn Als ze gelijk vertelt dat ze niet de enige zijn, dan kunnen ze nog wat met het verhaal 😀
@Sebsel Daar verweest ik (onzichtbaar) naar met ‘ook’ idd =)
@raymonmens Hij ging ook wel viral genoeg om tot het gemeenschappelijke twittergeheugen te behoren ja 🙂
@Sebsel had ik al gezien, goed verhaal is dat!
@matijn yep! 🙂
@Sebsel @raymonmens @matijn Heb dit voorval in het artikel opgenomen. Illustreert mooi dat het een groot probleem is http://sijmen.ruwhof.net/weblog/%5B..]
Lees en huiver: http://sijmen.ruwhof.net/weblog/%5B..] (door @sruwhof)
This #longread is a shocking revelation on how bad IT security often is in the real world: http://sijmen.ruwhof.net/weblog/%5B..] #ITSec
Lots of analysis on Dutch telco provider #opsec weaknesses. By Sijmen Ruwhof http://sijmen.ruwhof.net/weblog/%5B..]
Lekker bezig hoor @ThePhoneHouseNL! Hoop dat jullie dit nu wel hebben aangepast?? http://sijmen.ruwhof.net/weblog/%5B..]
Natuurlijk zijn uw gegevens veilig bij The Phone House…. http://sijmen.ruwhof.net/weblog/%5B..] via @henkdebruijn
@Vigro Geniaal artikel en zorgelijk tegelijk. Ik had hem al gelezen via @SLAM
#ITsecurity might not be the forte of trusted 3rd parties accessing your customer records http://sijmen.ruwhof.net/weblog/%5B..] #phonehousegate #telco
Looks like there is work to be done in the Netherlands – and unfortunately also in Finland I’m pretty sure… http://sijmen.ruwhof.net/weblog/%5B..]
A great lesson from the Netherlands for #telco’s and other companies with large customer databases http://sijmen.ruwhof.net/weblog/%5B..] #privacy
It’s borderline not-a-hack when the pwnee almost stops short of giving it away http://sijmen.ruwhof.net/weblog/%5B..]
Epic http://sijmen.ruwhof.net/weblog/%5B..]
Wow, what a mess and unfortunately there is a lot more security out there as bad as this… http://sijmen.ruwhof.net/weblog/%5B..]
I had the exact same thing at the Phone House in Amsterdam. They open a spreadsheet on a monitor that is positioned so that you can also see the screen. And then they walk away, for instance to make a copy of your ID, and leave it open for you to look at as long as you like.
I disagree with the author on one small point: The password policy. if all his recommendations were followed, then each employee ends up with several personal passwords which are difficult to memorize and have to be changed, let’s say, every few months. After a year, at best, I guarantee they would all end up on a spreadsheet or a post-it. Or at best, they would all be the same password, meaning if someone managed to see it once, they’d get access to every telecom. But if we go into it expecting each employee to use the same password for everything, maybe something a little more advanced and less demanding of the employee’s memory can be used…
If each person had their own encrypted keepass, it would still be more secure than right now. The best solution of course would be for phonehouse to do some kind of federated single sign on to those companies instead.
Keepass, or other password managers, are no good for the average user. Believe me; I have some very average users, and they just won’t use it.
We’ve implemented it as a requirement, company-wide. When it’s the choice between using it or facing disciplinary procedures for gross negligence – they use it.
This required the support of one’s betters. If itbgets in the way of money being made / products being delivered, you can bet that policy will change. I would love to be able to tell people to use it, but as it is it’s just an option. Those who do think it’s great, those who don’t write passwords in a diary and put it in their laptop bag. At least it isn’t on a post-it on the keyboard.
There’s a difference between not good enough and them not caring
Great article, but unless I’m missing something, the author actually has no idea how many records he could of accessed?
“My personal estimation is that Phone House, via dealerships, has access to personal data of basically all Dutch citizens who own a mobile phone. That would be between 10 and 14 million people.
I didn’t log in. If I had done so, I would have broken the law and I never do this.”
could have
and what do you mean he has no idea? sounds like he had a pretty good idea (i.e. all cellphone users)
“all cellphone users”
All contracted users, that is. Not the unregistered pre-paid and roaming ones.
You could get stats on the number of subscribers from previous years, add usual growth, check average sims per person stats if they exist for NL, and some other data… The author probably checked a few places and calculated a quick estimate.
“Ruwhof schat dat The Phone House via deze weg toegang had tot de gegevens van elke Nederlander met een mobiel abonnement, naar eigen schatting tussen de 10 en 14 miljoen.”
Translated: The number was editorialized based upon his own estimation.
O_o
Joure probably likes being called a city.
What a joke…
They could have at least attempted to use KeePass. I mean thats better then an unencrypted, unbackuped excel spreadsheet on Google Docs
More stories like this one need to be published, more publicly. Maybe that will shame idiots like those into figuring out WTF they’re doing!
Shaming only happens if people realize that what’s happening is a problem, which they apparently do not, assuming these Media Markt employees are typical non-computery people.
Wow.
Nice write up man!
All I can think is “enhance, enhance, enhance”!
This is a really excellent write up taking us through the issues and how you handled it responsibly. Thank you so much for taking the time to share it – best I’ve read in awhile.
Interesting story how poorly customer data is protected http://sijmen.ruwhof.net/weblog/%5B..]
fantastic read, shocking? Not so much #infosec #privacy http://sijmen.ruwhof.net/weblog/%5B..] @sruwhof perfect find, unfortunately too common
Schokkende bevindingen door @sruwhof over slechte gegevensbescherming bij Phone House & telecom providers. http://sijmen.ruwhof.net/weblog/%5B..]
Mooi verhaal over #Beveiliging en #Mensen als lek 😉 http://sijmen.ruwhof.net/weblog/%5B..]
Breathtaking – Use fingerprint access – best passcode. The rigidity of senior management is amazing – guess they were “saving cost”.
Another link to this story: http://www.testnieuws.nl/2015/12/17/zo-slordig-gaan-bedrijven-met-persoonsgegevens-om/
Thanks Rien for the link!
Thanks for this excellent story! And sad to read how clueless many organisations are about responsible disclosure. Security researchers like you should get more recognition for the valuable help you are providing companies.
Wat een goed artikel zeg !
De 82% nieuwsbrief van deze week (http://82procent.nl/ ) is weer top! Met dit keer een regelrechte boosmaker: http://sijmen.ruwhof.net/weblog/%5B..]
Nice read http://sijmen.ruwhof.net/weblog/%5B..]
I don’t think you can realistically expect the staff to adopt strong password practices. It’s better to focus on making it harder for random customers to look on.
There’s a more fundamental issue with your recommendation 17B: “If a customer calls the service desk, call him back on the telephone number that is linked to the customer’s account.” What if the customer is trying to call the service desk from some other number because there’s a problem with that number? What if they’re calling in to report that their phone has been lost or stolen?
I once had an issue where I wasn’t receiving email sent to a particular account. An explanation and the steps I needed to take to resolve it were duly sent… to the account I couldn’t receive messages on. There needs to be a way for customers to communicate out-of-band.
Thanks for your great story and I can understand security research is so difficult
Good article and valuable information. I think – yes. It’s that easy in many cases. Thank you for sharing information.
This is a great coverage! I just don’t understand why so many organizations can be completely unaware of the relating disclosure. There should be more security researchers like you that need to be rewarded for the help you provide to many companies.