As everybody has read in the newspapers, the recent American elections involved multiple and severe hacking attacks. Tens of thousands of confidential and private emails from Hillary Clinton and the Democratic National Committee (DNC) were leaked via WikiLeaks. It is thought by many that this helped Trump to win the election.
Journalists from Dutch TV station RTL contacted me last week and wanted to know whether the Dutch elections could be hacked. They had been tipped off that the current Dutch electoral software used weak cryptography in certain parts of its system (SHA1).
I was stunned and couldn’t believe what I had just heard. Are we still relying on computers for our voting process?
Voting machines banned in 2009
The Dutch government banned electronic voting for cyber security reasons on June 4th, 2009. We returned to using red pencil and paper and have done so ever since. This video demonstrates the manual vote counting process in The Netherlands that is active since 2009:
Seems pretty solid right with all the visible paper? Hold on! RTL told me that voters use pencil and paper, and that votes are counted manually. However, for efficiency reasons the vote totals are then, for each city, entered into a computer program by election officials.
Voting machines have continued to be used in the background since 2009
This computer program generates multiple files containing the voting total entered by the election official from each district. The data is put on a USB-stick and transferred to a higher district, and so on. In the end the central Electoral Council gets all votes combined in a digital file.
Critical weakness in voting system
If nobody questions the (digital) results of the election, no final paper audit is performed to see if the analog and digital vote count is the same.
I immediately realized that this optional final paper audit forms a critical weakness in our current voting system (risk #1 critical). It means that our pencil-and-paper voting is basically security theater in its current implementation. Because when analog voting results are inserted into computers, which subsequently calculate the results, we are still, effectively, using electronic voting.
I was both amazed and frightened by this fact.
Anyone with a certain level of IT-security knowledge will tell you that a computer cannot be trusted. Whatever steps you take to secure a computer, it will always be possible to hack it. And against state-sponsored hackers you have almost zero chance. To put it bluntly: you can’t protect a computer system against experienced and well-funded state-employed hackers.
Electoral Council unaware of current cyber threats
The Dutch Electoral Council is massively unaware of possible cyber threats and simply states their software is secure and everything is under control.
I became curious about this software which (since 2009) has quietly decided who gets to run my country.
First start: YouTube
The Dutch Electoral Council made several YouTube-instruction videos on using their software. I thought this would make a good start for my investigation. In one video an instructor from the Electoral Council explains how to perform an election recount with their software:
Instructor leaks internal network share-names
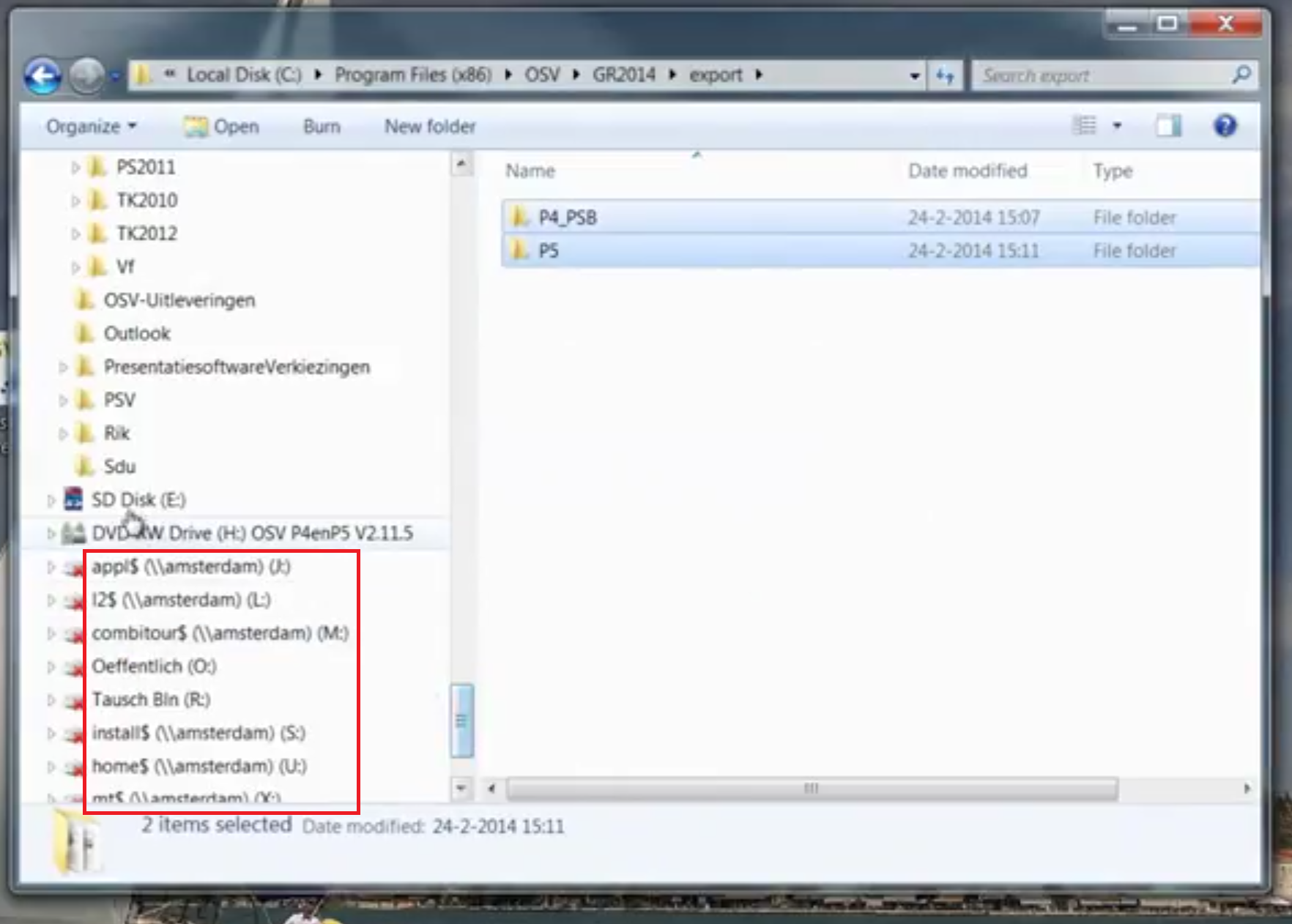
The beginning of the video is rather boring but it becomes interesting at 01:19 minutes. The instructor has opened Windows Explorer and as many as eight internal network shares (from an internal server called Amsterdam) are shortly visible:
The set-up of internal networks is considered confidential technical information. Unfortunately, the instructor remains unaware of this leak (risk #2 very low). I get the feeling that this introduction into our voting system is getting interesting!
Desktop voting-software uses web server
While the instruction video continues I noticed the voting-software initial installs a web server on the user’s computer. Users have to open a web browser before they can use the voting-software. From a security standpoint it is a very bad idea to use a web server and browser for an ordinary desktop application (risk #3 medium):
- Introducing a web server on a desktop in order to run a desktop-only application creates a significant attack surface for hackers.
- The voting-software does not use the internet to communicate data. Also, all voting-software can be used offline. So there is absolutely no need to start opening TCP ports on a computer.
- The web server can possibly be accessed by others on the network if the host-based firewall is missing or misconfigured.
- If the router supports United Plug and Play (UPnP) this can cause the voting web server to be directly reachable from the internet. And really, that is the last thing you want!
In conclusion: a very odd and insecure digital architecture was chosen for the voting software.
Voting software can be installed on any computer
To go even further, the voting software-application can be installed on any computer. The Dutch Electoral Council has not set up any security baseline for this (risk #4 high):
- Old computers that lack security updates can be used. This applies equally to computers without anti-virus scanners.
- Personal (BYOD) computers are not prohibited.
- Windows XP computers are supported according to the system requirements of the software. All Chrome and Firefox versions also, even those with missing security patches.
If you want to create a high security level then please use only properly secured computers without internet/network connection (air-gapped).
The system requirements document for the software state that WiFi should be turned off on the computer, but nowhere it’s mentioned that the internet cable should be unplugged from the computer. This omission made me giggle, but when reality kicked back in, I was shocked.
Unsecured HTTP connection used
The browser for the election software connects to a local host via an unsecured HTTP connection (risk #5 medium). Since the browser-traffic doesn’t leave the computer it is not an immediate threat. Even so, this introduces various security risks, such as:
- Possibly leaking HTTP referrer headers to other websites when the voting web portal contains links to other external sites.
- Creating a cyber attack surface between web browser and server. This can be intercepted and altered by other malicious software which could already be active on the computer on which the software is installed.
- If an HTTPS connection is active, the web browser activates several additional security measures such as tightening web page cache settings.
In conclusion: even HTTP traffic that only travels on a local host should be secured with HTTPS.
Instruction manual doesn’t enforce hash check and bad crypto
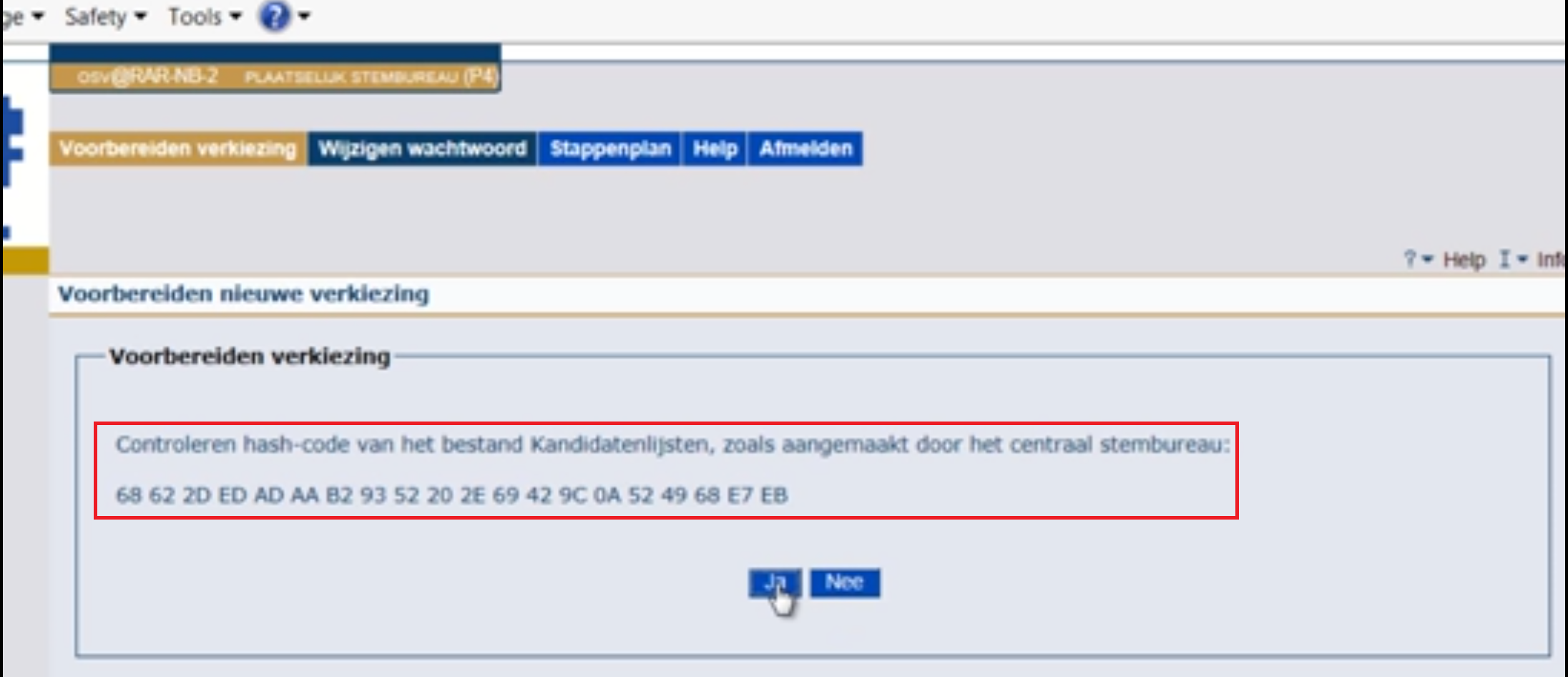
I am now two-and-a-half minutes into the instruction video (02:41) when I see the following screen:
The instructor remains quiet and quickly clicks the ‘yes’ button to proceed to the next screen. Hey, hold on – what did I see there? I rewind the video and see a very important security question being asked by the voting-software in which the user has to manually compare a 40 character code to see if the election has been tampered with. Yet the instructor does not mention this important security check at all (risk #6 high). Worse, the voting-software doesn’t even force the user to enter the hash code (risk #7 high). Shockingly they seem to use the insecure, old and deprecated SHA1 hash algorithm RTL told me already about (risk#8 high).
Usage of SHA1 seems to be only a small problem in comparison about what comes next.
Hash codes sent together with data files
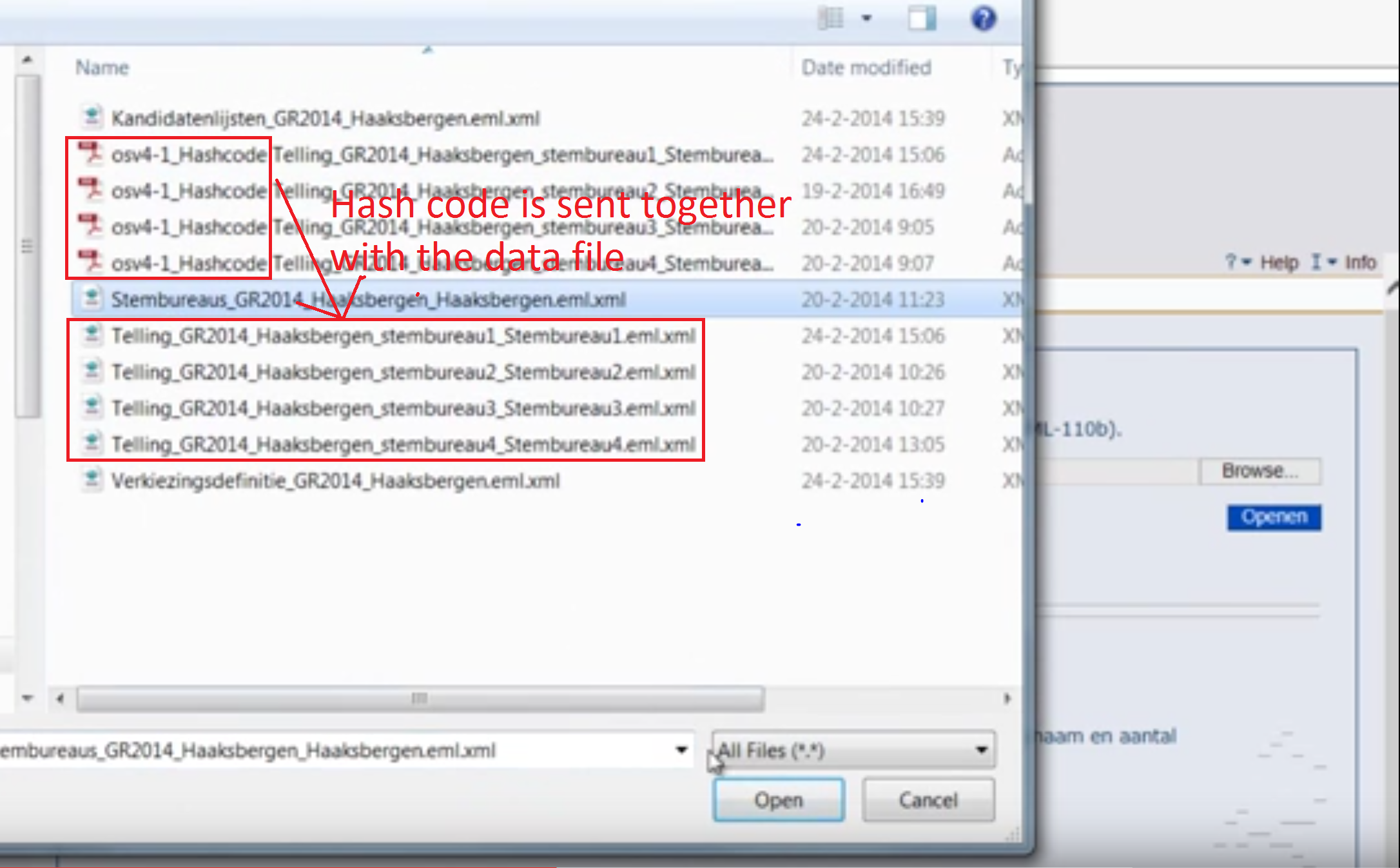
At 02:52 into the instruction video I see the following screen:
The PDF files contain the SHA1 hash code which protects the XML files. The XML files contain important data from the election. It’s of utmost importance that the XML files are of high integrity because these can contain voting totals on election day. To protect the integrity of the XML files, a SHA1 hash code is generated so the XML file can later be checked on generating this same SHA1 code. Manipulating the XML file by hacking, results in the generation of a completely different SHA1 code.
Creation process of PDF and XML file
The moment the voting software generates XML files containing the voting totals, an accompanying PDF file is created with a specific SHA1 code (this PDF file is probably created for print use). The (paper) printed SHA1 code cannot be remotely changed by hackers.
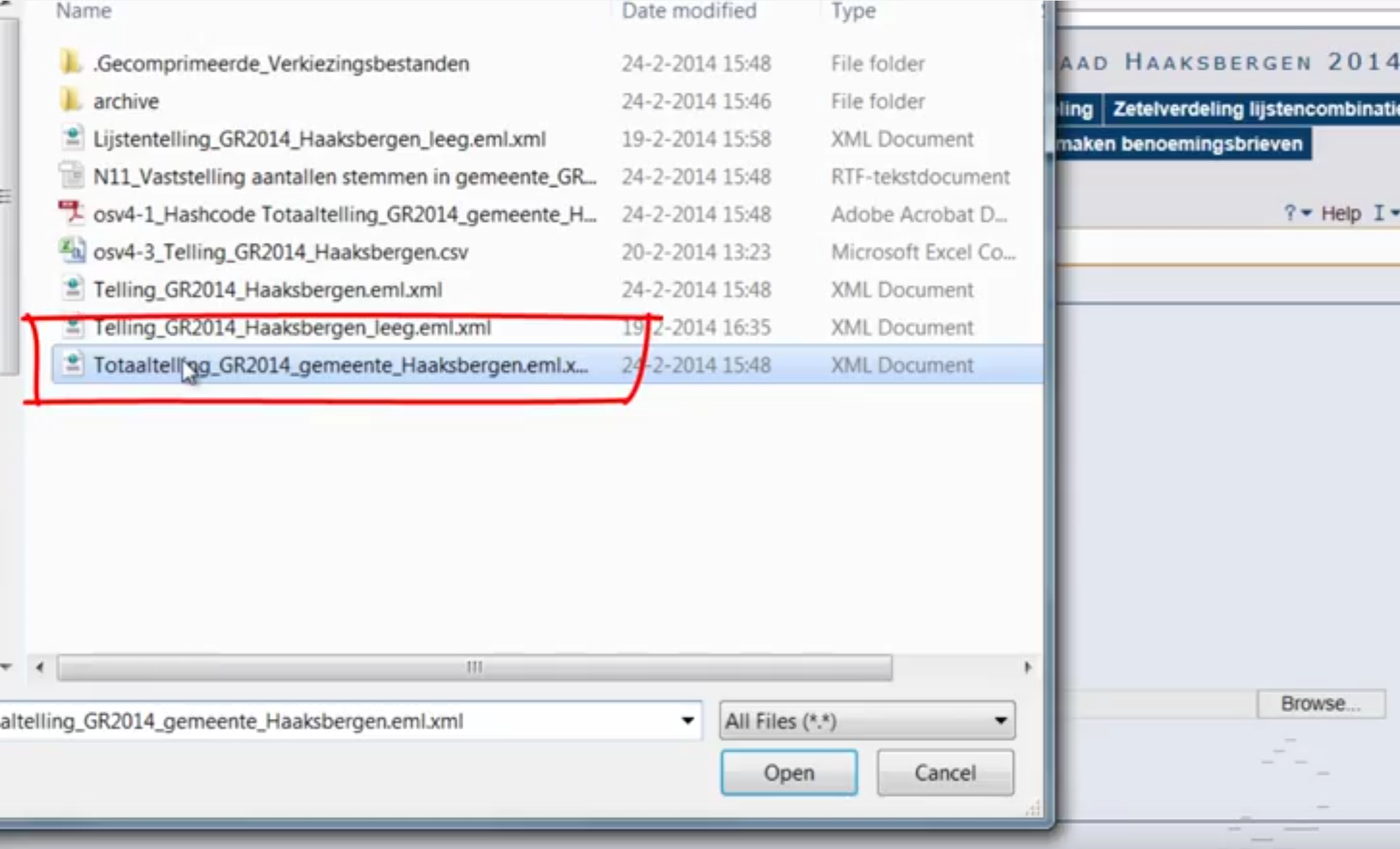
These files are subsequently copied onto an USB stick. This USB stick is then physically transferred to a higher election district. This higher district collects all the USB sticks from the lower election districts and loads all the XML files into the voting-software.
Unprotected XML files
The XML file generated by the voting-software is not encrypted. Basically anybody can change the contents during transit (risk #9 high).
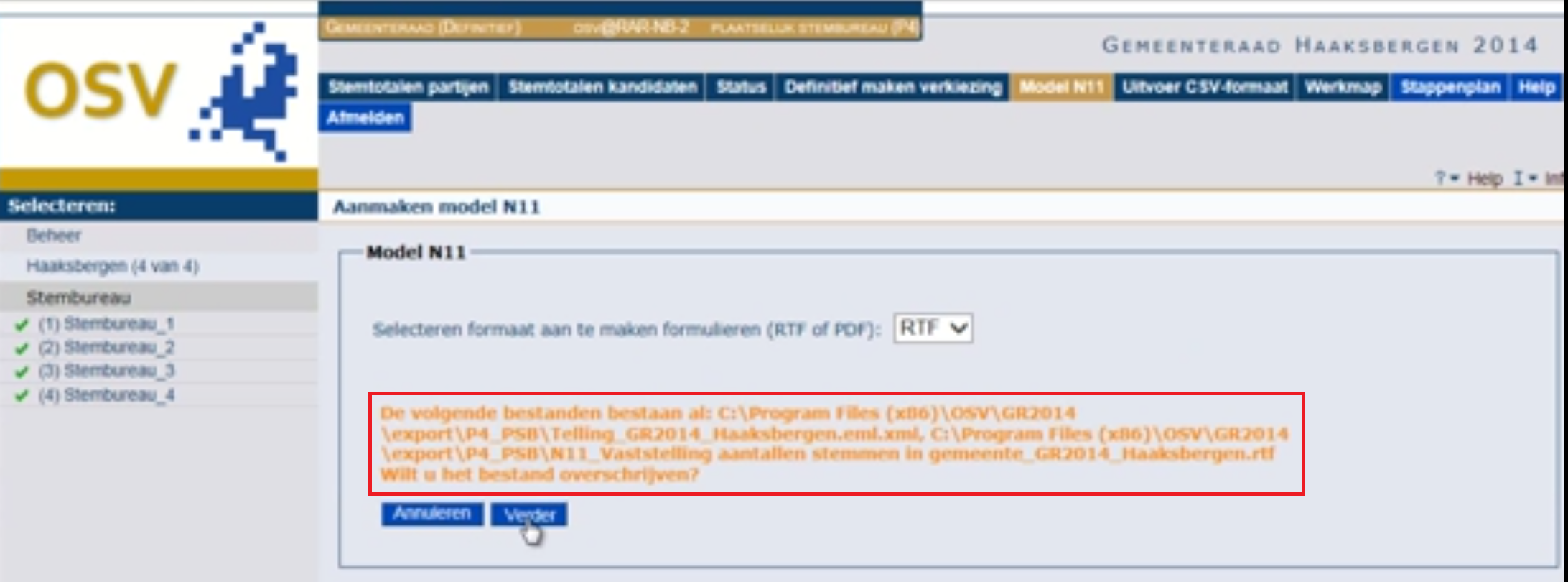
Generated PDFs should be deleted after printing
The user of the voting-software should print the PDF files, then immediately delete them. Unfortunately the video-instructor did not find it necessary to do so, and even leaves them sitting next to the XML files (risk #10 medium). The computer system does not mention this step nor enforces you to delete the PDF files (risk #11 medium). Printing the PDF files is optional so might not be done. Instead, users can open the PDF files on the USB stick while importing the XML files on to the next computer. After all, who wants to handle paper prints if there is a digital option?
When explaining the SHA1 check, the instructor even shows how you can validate the SHA1 hash by showing the PDF file in a PDF reader:
I think the instructor doesn’t know that the architect of the OSV software probably wants users that they print the PDF file. The architect designed the system, but it seems that this person doesn’t review the generated (YouTube) documentation about it (risk #12 medium).
Transferring the XML file from one vote-counting computer to the next raises a critical cyber security risk as it is almost certain that non-encrypted USB sticks are being used (risk #13 high). These USB sticks carry non-encrypted XML files and the only protection lies in the apparent security of the SHA1 code. But that code is also transferred via a PDF file on to the USB stick.
The fact that USB sticks are used in the process is a serious shortcoming in the security of the voting-software as you should never insert an unknown USB stick into your computer. Doing so can result in your computer getting hacked via:
- Malicious software on the USB stick that is automatically executed by the computer (via AutoRun technology).
- A BadUSB attack.
Even if the cryptographic signing was implemented well, it all can be bypassed if malicious software is loaded on an USB stick (risk #14 high).
Instructor uses short password and auto-completes it
At 03:07 minutes the voting-software login screen shows:
The instructor types ‘OSV’ and hits the TAB key. His web browser then auto-completes the password (risk #15 medium), yet the instructor does not notice this and manually enters his three letter password (risk #16 medium). This is funny, I bet his password is also ‘OSV’ …
Apparently a non-personal account is being used (risk # 17 low) and the computer-system allows weak passwords to be configured (risk #18 medium).
The USB stick is very vulnerable to manipulation during the time it travels all those kilometers to a higher election district.
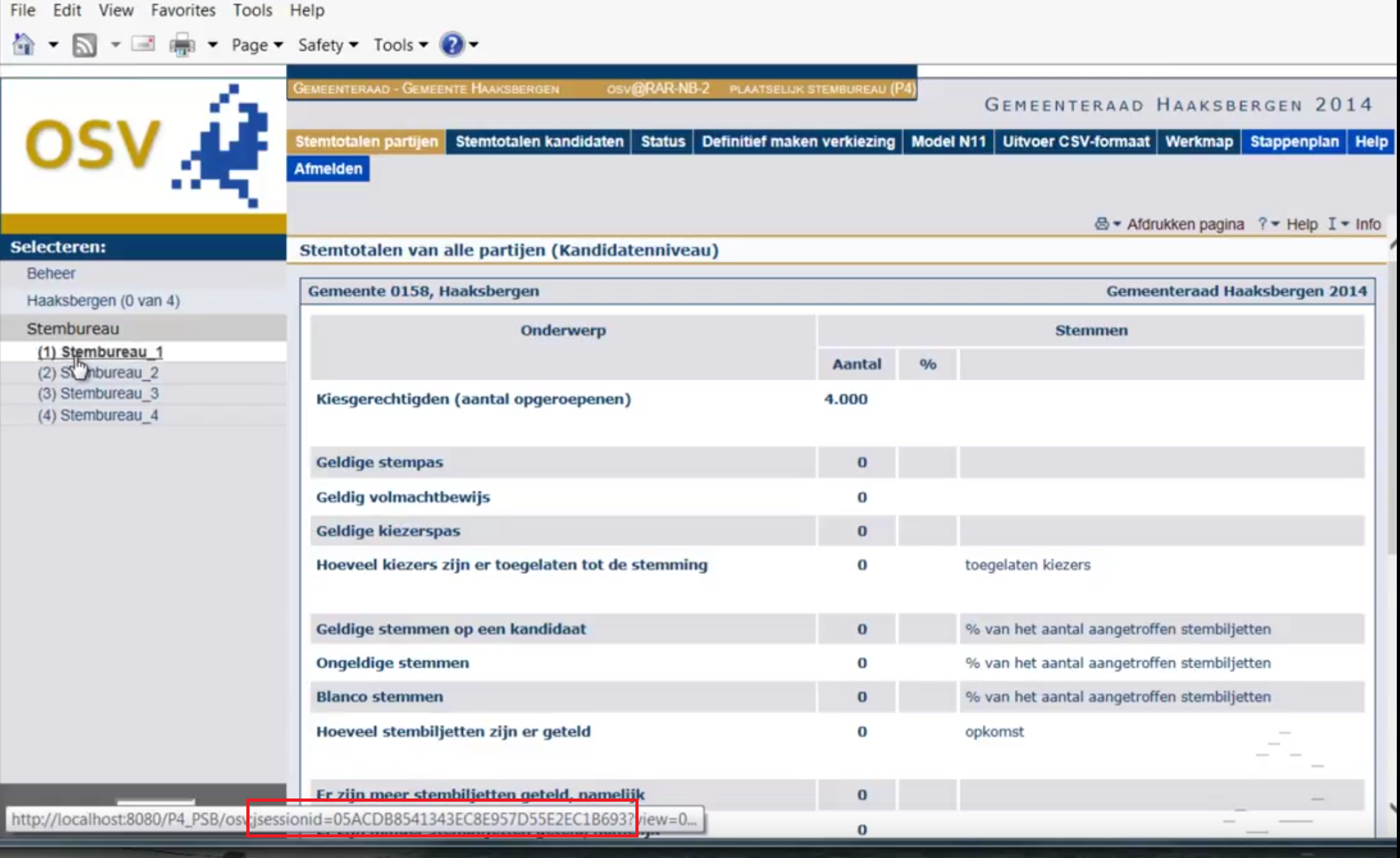
Secret identification code put into address bar
After having passed the login screen the instructor hovers over a link in the web portal and Internet Explorer shows its internet address:
Look closely and you’ll notice the Java session identifier is visible in the internet address (risk #19 low). This is an important token that should only be stored safely in a well protected cookie (that is, with HttpOnly, Secure and SameSite options set):
- When a hacker is able to copy the token he/she can bypass the login screen.
- As the web portal runs over an non-secured HTTP connection, this token can also leak to other websites.
- Also, the token will be saved in the browser history.
Running software under administrator privileges
I am now at 03:44 minutes into this epic instruction video and I notice that the instructor seems to be running Windows via an administrator account:
The software writes user files in its installation directory: C:\Program Files (x86)\OSV\
This is possible only if the instructor has administrative rights on Windows (risk #20 medium). It is really not a good idea to run a daily task with high-privilege access. The instructor should instead have used a low privileged account to run this software.
The makers of this voting-software don’t seem to be familiar with the concept of user isolation or hardening. Thus the voting-software saves user files by default into the normally restricted C:/Program Files/ directory (risk #21 medium).
Malware can easily tamper with votes
The instruction video is now at 04:08 minutes and shows a generated XML file. The instructor again has to import the file via the user interface:
Since the file has just been generated on the very same computer no automatic SHA1 hash check is in place (risk #22 high).
The computer running the vote-counting software can easily be infected with malware during daily use while browsing the internet or reading mail. If indeed the computer contains malware which specifically targets the election, then it only has to change the XML file in the C:\Program Files (x86)\OSV\ directory. Because the XML file is not encrypted, no automatic hash check is in place. Changing the XML files is extremely easy to do once a hacker has managed to gain remote access to the computer.
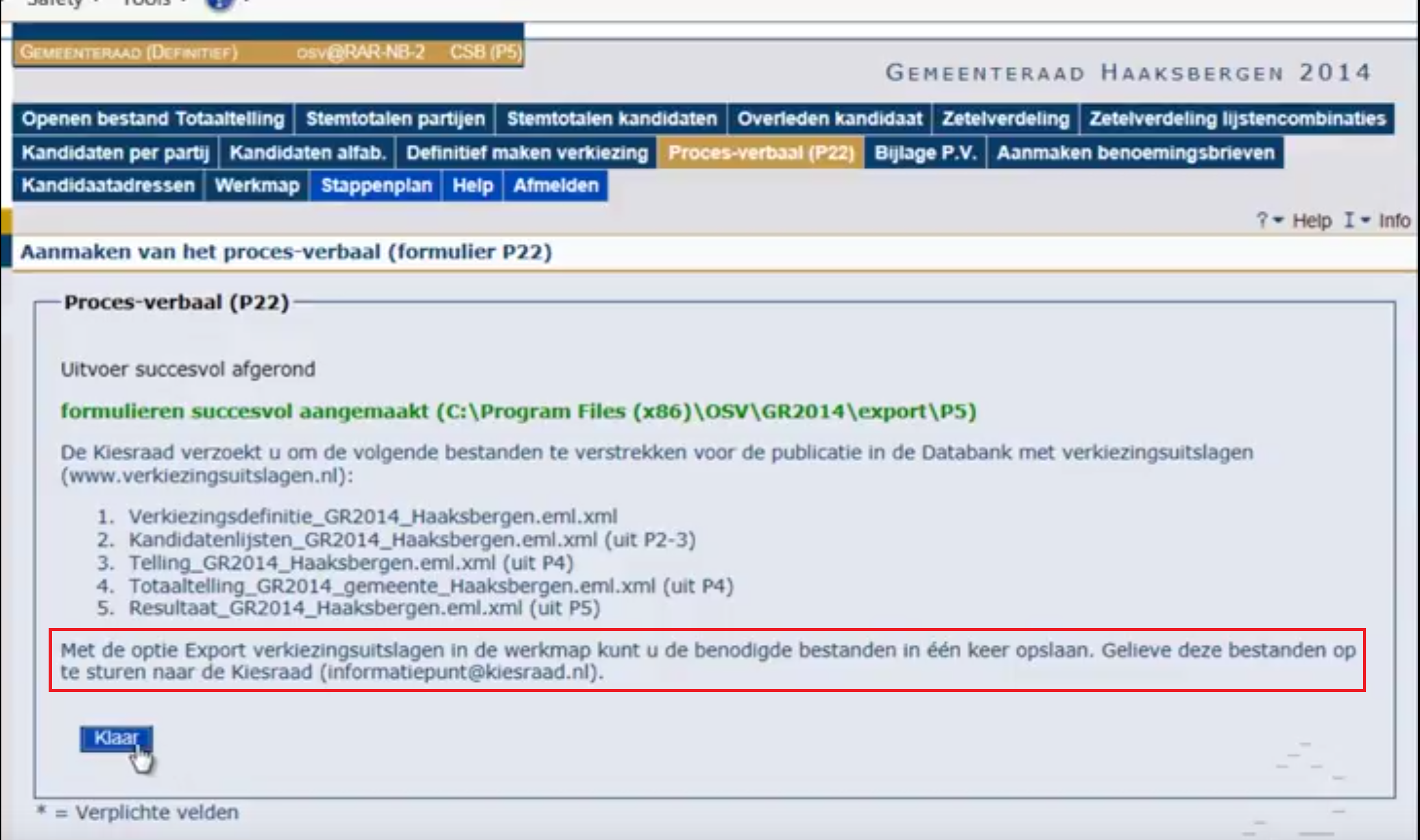
XML files are being mailed during use of voting-software
At 04:45 minutes into the instruction video the voting-software tells the user to mail XML files with voting-results to the central electoral council:
E-mail is not encrypted and therefore a very insecure medium (risk #23 high). What were these software developers even thinking? Doesn’t security matter? How can you send voting results via unsecured e-mail? It is unbelievably easy to intercept and alter e-mail messages.
No printing instructions for PDF file
After finishing this five minute YouTube instruction video, I start the second one:
This two-minute video gives instructions on finalizing vote counting totals. It instructs on how to generate PDF and XML files with vote totals. The instructor mentions that you should save the PDF and XML file on an USB stick and transfer it to the next computer; but printing the PDF file is never mentioned once. Apparently this is how our vote-counting process is performed!
Implemented crypto system is getting worse
After finishing the second instruction video I start the third one. It’s about configuring the election data. Here you first have to understand that the electoral council has implemented additional security measures in the original specification, and then, this specification was realized by a German software development company.
When importing an XML file from another computer, the user is normally shown a 40 character SHA1 code in the web portal. Below to this code you see a ‘next’ button. Only if the user finds it necessary to do so, does he/she compares the SHA1 code in the web portal with the SHA1 code in the PDF file (which in turn is on the USB stick).
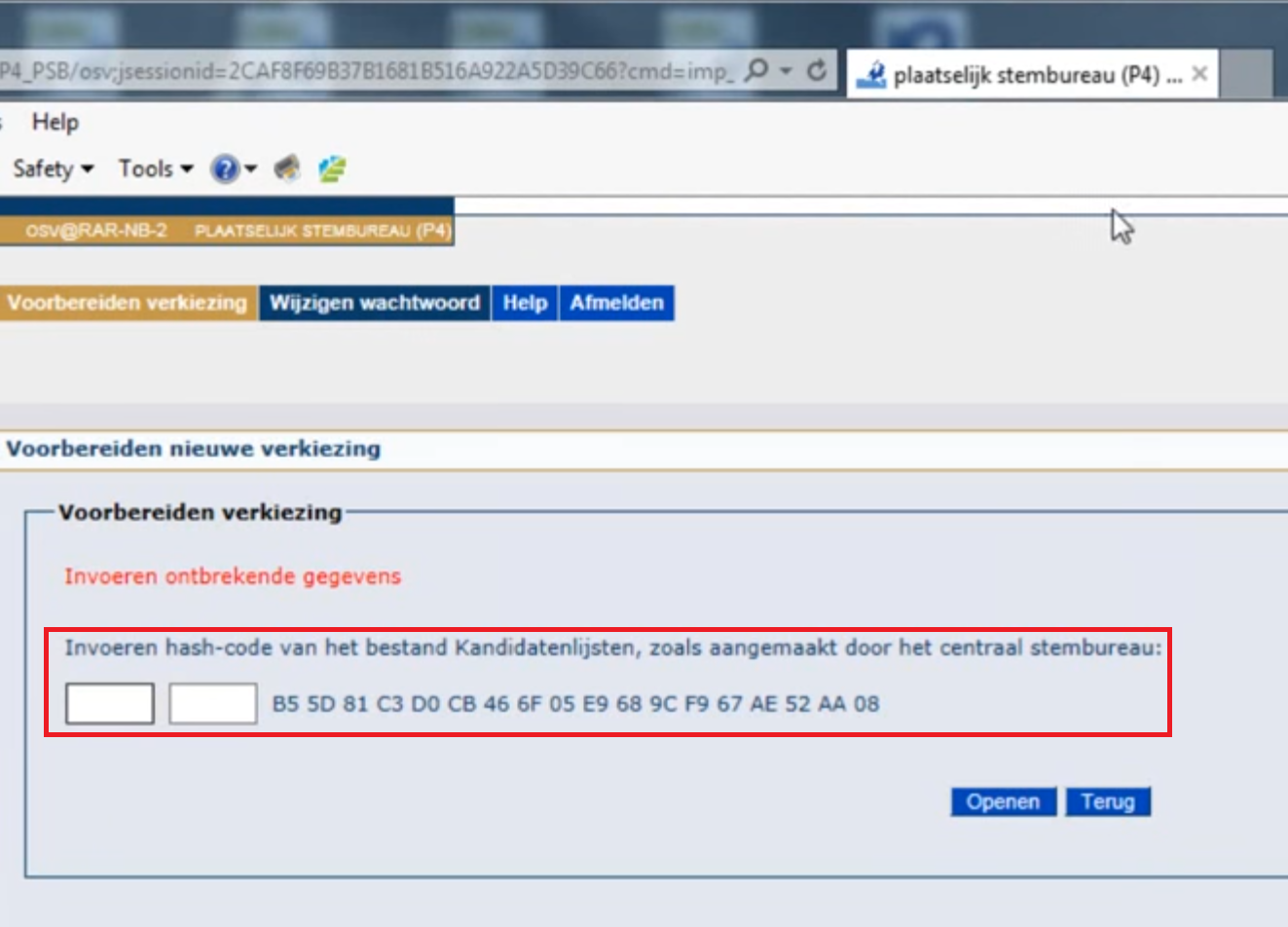
Because configuring election data requires additional security, the German developer came up with a solution that the user has to enter the first four characters of the SHA1 code that’s visible in the PDF-file into the web portal. Meanwhile the 36 remaining characters remain visible on the screen:
The instructor explains how to use this screen
“[…] You will be prompted to enter the hash code from the uploaded candidate list. This hash code can be found on the website of the Kiesraad (electoral college), or possibly in the file [..] that is located in the same folder where you found the candidate file. […]”
Both screen and instructions limit the strength of the SHA1 key to 2^16 combinations. That’s just 65,536 possibilities and delivers almost zero cryptographic strength (risk #24 high). A normal SHA1 key provides 160 bits strength and that’s 2^160 possibilities – a vastly larger number. This means the additional security requirements caused exactly the opposite: almost no security at all! And, unfortunately, this additional requirement is in place in many more XML import routines.
Additional vulnerabilities
I can go on and on listing additional insecurities in this voting system, such as:
- Internet connected computers.
- No IT security expert was consulted when building this software.
- It’s partly open source.
- About a cross-site scripting vulnerability I found.
- Logs are not collected on a central server and thus easy to tamper with.
- No intrusion detection systems are active.
- No experienced ethical hacker has reviewed the software.
- No security test reports are available.
- The integrity of the software is hard to validate, and even optional.
- Etc.
To save time, I hope I made my point already and thus will not write about further vulnerabilities in this horribly insecure voting software.
Nowhere in the hundreds of pages of documentation I read about the software, mention the fact that a hacker might tamper with the election results. It seems the Election Council and the hired software development company simply forgot about the hacker threat. This is almost unbelievable, but then again: my security research proves it’s very easy for just one person to manipulate the election results on so many levels.
Conclusion
Will we ever learn that our important voting process simply cannot be trusted when critical elements are outsourced to software? Our Dutch democracy has been in the hands of very badly protected software since 2009. We’ve run already ten elections with it and in March 2017 we’ll use it again if nothing changes.
I could already find security holes by doing nothing more than watching a few YouTube instruction videos and reading some system documentation. And this only took me one evening to do so (!).
If I can find these security holes this easily, others can as well. This means no proper IT security specialist was consulted for the development of the voting-software. Instead, some incompetent German software development company was hired to build the digital voting system and no proper oversight was conducted by our Electoral Council. Apparently nobody thought about hiring an ethical hacker or security specialist to see if the system could be hacked. This is pure madness and far beyond what I had ever expected to find.
I hope that with this publication we will finally realize that voting should never be fully performed digitally since software can so easily be manipulated. Pencil-and-paper voting should be the only option. Furthermore, strict audits should be enforced, six-eyes procedures deployed as standard, with regular and obligatory consultations of senior IT security specialists and cryptography experts.
In conclusion, it is not hard to make the voting-process secure. But only the right experts should be involved.
An in-depth forensic research should be conducted to check if our elections have been manipulated since 2009. I hope our Electoral Council keeps logs so that investigators can review these. This probably won’t be the case since almost all the log files are stored on the individual desktop computers of all the people using the voting-software. Thus, unfortunately, we may never know if our elections have been hacked in the past.
I truly hope that from this moment on the Dutch government will take election security way more seriously. Because the status quo is totally unacceptable!
Overview of all identified risk
- Critical: Optional final paper audit.
- Very low: Eight internal network shares (from an internal server called Amsterdam) are visible in a YouTube video
- Medium: The voting-software initial installs a web server on the user’s computer. Users have to open a web browser before they can use the voting-software.
- High: The voting software-application can be installed on any computer.
- Medium: The browser for the election software connects to a local host via an unsecured HTTP connection.
- High: Instructor skips important SHA1 check in YouTube video.
- High: Voting software allows skipping SHA1 check.
- High: The insecure, old and deprecated SHA1 hash algorithm is used everywhere in the software.
- High: The voting software stores voting results in an unencrypted XML file.
- Medium: PDF file with SHA1 hash code is stored next to corresponding XML file it has to protect.
- Medium: The voting software / instructor does not mention that PDF files should be printed, nor enforces you to manually delete generated PDF files.
- Medium: The architect designed the system, but it seems that this person doesn’t review the generated (security) documentation about it.
- High: Non encrypted USB sticks are used.
- High: Custom USB sticks can be used and these sticks can be loaded with malicious software.
- Medium: Web browser automatically completes user passwords on a shared computer.
- Medium: Instructor uses three letter password.
- Low: A non personal user account is used.
- Medium: No password strength policy is in place.
- Low: The Java session identifier is visible in the internet address.
- Medium: Instructor uses Windows administrator account instead of low privileged account. The software allows this.
- Medium: Software saves high integrity XML files into a public location on the computer.
- High: No automatic SHA1 hash check is in place for XML files stored on the computer.
- High: Voting results are sent via an unencrypted e-mail over the internet.
- High: Most sensitive operations in voting software have least SHA1 protection.
- Etc. etc.
Update January 30, 2017: RTL News TV broadcast
I’ve worked together with the RTL News research redaction when writing this story. They contacted additional security experts, such as Rop Gonggrijp, Ger Schinkel and Herbert Bos who validated my research. RTL News went live with the story on Dutch TV:
Update January 31, 2017: NOS TV broadcast
NOS about the story and a reaction from the responsible minister:
Update January 31, 2017: Election Council ignores security vulnerabilities for years
It appears that six years ago, university student Maarten Engberts already found out that this voting software was insecure. He confronted the Election Council in 2011, but they ignored all his findings.
Update February 1, 2017: Dutch minister responds
Two days after publication of this article, the responsible Dutch minister Ronald Plasterk ordered the dismission of electronic vote count machines in the upcoming election in March 2017.
Update February 3, 2017: USA Today made an overview
After publication of this article, a lot has happened. The USA Today may a quick overview:
Update February 4, 2017: Overview of Tv coverage
Someone combined Tv coverage of the last few days about this research. Includes reactions from Alexander Pechtold (D66), Sybrand Buma (CDA) and Ronald Plasterk (VVD):
Update March 2, 2017: Fox-IT confirms my research
The Electoral Council hired the well respected Dutch cyber security firm Fox-IT to investigate the security of the current election process. In their detailed analysis (PDF 90 pages, recommended read), Fox-IT confirms almost all my findings.
Update March 3, 2017: AFP video interview
Journalists from AFP took the following video interview, and released it in raw stock material on GettyImages for others to take over:
Update March 9, 2017: Vlog from Michael Hilberer about German election security
The vulnerable vote count software in The Netherlands is made by a German company. That same company used a modified version of the Dutch software for use in German elections. More about it in the vlog from Michael Hilberer:
Update March 9, 2017: South American TV broadcaster (teleSUR) about Dutch election hacking
Today South American TV broadcaster teleSUR brought my research about how I could hack the Dutch elections under attention via their news update:
Update March 10, 2017: Former chairman Electoral Council Henk Kummeling
Former chairman Electoral Council Henk Kummeling thinks the official voting results will be delayed:
Update March 14, 2017: Dutch regional TV: ‘Manual counting is an enormous operation’
Dutch TV broadcast from RTV Rijnmond about the new manual counting process:
Update March 15, 2017: Dutch regional TV: ‘Volunteers help at voting offices’
Dutch TV broadcast from RTV Oost:
Update June 20, 2017: Evaluation of the voting process in Dutch parliament
Today the Dutch parliament evaluated the election that was held in March. The transcript of the discussion is in Dutch.
International news sites that link to this article
- BBC.com: ‘Dutch to hand count votes over hacking fears’
- NYtimes.com: ‘Fearful of Hacking, Dutch Will Count Ballots by Hand’
- WashingtonPost.com: ‘Dutch ballots to be counted by hand amid hacking fears’
- TheGuardian.com: ‘Dutch will count all election ballots by hand to thwart hacking’
- Spiegel.de: ‘Niederlande: Stimmenauszählung bei Wahlen – Zurück zum Taschenrechner’
- ComputerWorld.com: ‘iPads ‘more secure than voting systems’ — claim’
- RT.com: ‘Dutch to hand-count ballots in March vote amid ‘hacking & fake news’ fears’
- InfoSecurity-Magazine.com: ‘Dutch Minister Ditches Election Software Over Hacking Fears’
- TheRegister.co.uk: ‘Netherlands reverts to hand-counted votes to quell security fears’
- MacDailyNews.com: ‘iPads ‘more secure than voting systems’ — claim’
- TechGig.com: ‘iPads ‘more secure than voting systems’ — claim’
- Elmundo.es: ‘Holanda contará a mano los votos de las elecciones de marzo para evitar a los hackers’
- Atlantico.net: ‘Holanda contabilizará votos a mano contra los ciberataques’
- Egazette.eu: ‘Dutch go old school against Russian hacking’
- Antena3.com: TV news item and web article: ‘The Netherlands will avoid computing in elections for fear of a cyber attack and will count the votes manually’
- 521gxw.com: Overview of election hacking news stories of last year
Dutch sites that link to this article
- RTLnieuws.nl : ‘Met potlood stemmen onveilig: verkiezingsuitslag eenvoudig te hacken’
- RTLnieuws.nl: Dutch news article with all the major weaknessess explained for non technical people
- RTLnieuws.nl: ‘Vrees voor hackers: kabinet schrapt software, stemmen tellen volledig met de hand’
- UitzendingGemist.nl: Dutch TV news item about my research (6:30 min.)
- EenVandaag.nl: Dutch radio show with RTL, AIVD and D66
- AD.nl: Dutch news paper interviewed me about my research
- AD.nl (follow up)
- 3FM.nl: Radio interview with me about my findings
- NOS.nl
- NOS.nl (follow up)
- NOS.nl (audio interview)
- Nu.nl
- Nu.nl (follow up)
- NRC.nl
- NRC.nl (follow up)
- DeGelderlander.nl (via Blendle.com)
- FD.nl
- Volkskrant.nl: ‘Beveiliging stemproces uiterst knullig’
- Volkskrant.nl (via Blendle.com): ‘Stemmentelcomputer is slecht beveiligd’
- MetroNieuws.nl
- Tweakers.net
- Tweakers.net (follow up 1)
- Tweakers.net (follow up 2)
- BNR.nl
- BNR.nl (follow up)
- BNR.nl (audio interview)
- Security.nl
- LindaNieuws.nl
- DutchCowboys.nl
- Joop.nl
- Joop.nl (follow up)
- BeveiligingNieuws.nl
- Tubantia.nl
- Gelderlander.nl
- Gelderlander.nl (follow up)
- Twitter.com: Dutch politician reacts on camera on the story
- Reddit.com: ‘Met potlood stemmen onveilig: verkiezingsuitslag eenvoudig te hacken’ (Discussion about this article)
- DeSpeld.nl
- NLtimes.nl
- Hoholok.com
- Politiek.tpo.nl
- Computable.nl


As mentioned in the blog post: Ondersteunende Software Verkiezingen (OSV) is partially (or even mostly?) open source software. Its source code can be downloaded from the website of the Electoral Council (kiesraad.nl). Anyone with an eye for software engineering can see that the source code is too disorganised to be auditable and that the tests are woefully incomplete. I doubt the Electoral Council performed a software audit of any sort.
Luckily it’s open source: https://www.kiesraad.nl/adviezen-en-publicaties/formulieren/2016/osv/osv-bestanden/osv-broncode-programma-4-en-5-versie-2.17.2
Let’s see how the passwords are stored:
./osv45/src/de/ivu/wahl/client/beans/ApplicationBean.java: passHash = calcHash(name + pass);
./osv45/src/de/ivu/wahl/anwender/AnwenderHandlingBean.java: String passwortHash = calcHash(anmeldename + passwort);
./osv45/src/de/ivu/wahl/client/beans/AdministrationBean.java: passwordHash = calcHash(name_anwender + passwort);
And how does this function calcHash work?
public static String calcHash(String plainText) {
try {
MessageDigest md5 = MessageDigest.getInstance(“MD5”); //$NON-NLS-1$
Do I need to type more? 😛
Reading your comment, I wonder which software is used in the German elections…
In Germany the same OSV software is used. Germany only uses the software for quickly couting all the votes, but will also perform a separate final paper based audit. So, critical finding #1 (optional paper audit) can not be applied to Germany, and thus that makes the situation in Germany much less dangerous.
Pingback: Experts: verkiezingsuitslag is te hacken, ook als er met rood potlood gestemd wordt
Since our government has no clue on Information Security hwatsoever (as we can see in numerous other systems and handling of personal information by various governmental institutions) I am actually hardly surprised.
I would even go as far as that the PDF mentioned above is probably put on the same USB stick with the voting data, making it almost childs’ play to rig the Dutch elections.
btw, IMHO the voting machines were actually banned earlier then that. Early 2009 was indeed the first national election back with the red pencil, but not the date the machines were outlawed.
See this: http://wijvertrouwenstemcomputersniet.nl/Wij_vertrouwen_stemcomputers_niet
“Tens of thousands of confidential and private emails from Hillary Clinton and the Democratic National Committee (DNC) were leaked via WikiLeaks. It is thought by many that this helped Trump to win the election.”
I stopped reading there. Trump did not win because the DNC was hacked. But because their candidate was incompetent, he campaigned properly and the DNC is a mess. The emails never received mainstream coverage. Can you please refrain from insinuations without proof?
Manipulating the public opinion is a very strong election influencing force.
Thank you. Can you describe the audits used in the Netherlands? That’s the main protection we have.
As you note, computers can’t be trusted, and the cleanest argument for that that I’ve seen in the election world is the paper on “Software Independence” (Wack and Rivest): http://vote.nist.gov/SI-in-voting.pdf
So we should make sure that the systems and procedures used in elections produce evidence suitable for efficient auditing, as discussed in “Evidence-Based Elections ” by Stark and Wagner:
http://statistics.berkeley.edu/~stark/Preprints/evidenceVote12.pdf
It references the state-of-the-art techniques for the sorts of Risk-Limiting Audits that we have used in Colorado and California.
If the digital election results are believed to be true, than no final paper audit is performed in The Netherlands to check if the software wasn’t been hacked.
Pingback: How to hack the upcoming Dutch elections – and how hackers could have hacked all Dutch elections since 2009 – sec.uno
Interesting article! UPnP stands for “Universal Plug and Play” though, not “United Plug and Play”.
I wonder how you could leverage UPnP to open up the port to a remote host. If you have control over the computer hosting this software it is not necessary and otherwise the default Firewall settings should prevent any incoming connections. Is it possible to request a port to be opened for another host, say if you have access to another PC in the subnet but not the computer running the software itself?
Thanks! Just fixed the UPnP typo 🙂
If a router supports UPnP, then a computer on the local network can ask the router to automatically open up a port in the NAT firewall on the router. When I installed the OSV software in a virtual machine, the Windows Firewall asked me if I wanted to make the port available on the internal network. That’s not a good thing.
Pingback: Five Blogs – 2 February 2017 – 5blogs
Pingback: Netherlands reverts to hand-counted votes to quell security fears – sec.uno
Pingback: ste williams – Netherlands reverts to hand-counted votes to quell security fears
Pingback: Netherlands reverts to hand-counted votes to quell security fears (The Register) – sec.uno
Pingback: Hackowanie holenderskiego systemu do obsługi wyborów na podstawie… oficjalnego filmu instruktażowego
First the article says that you use USB then you mention E-mail.
So what is it?
> This computer program generates multiple files containing the voting total entered by the election official from each district.
So you enter like “party A: 50 votes, party B: 60 votes”?
But what exactly do you mean with paper trail or paper audit?
That it will be written down and sent via snailmail to the next higher gov level? Can also be tampered with.
Pingback: iPads ‘more secure than voting systems’ — claim | Computerworld | Verified Voting
I’m curious why you list “It’s partly open source” as an additional vulnerability. I have the opinion that software like this should be fully open source so that any citizen can audit the software that is used to count their vote. Of course, there are no guarantees that the software running at election time will be built from the same source as the one that’s public but that’s a very different problem. In the end, I fully agree that we should keep any software away from our election, just curious why you consider being open source an additional vulnerability.
If some part of the software can’t be checked, that results in a certain level of uncertainty. That uncertainty creates less trust in the software and thus increases the security risk as certain parts can’t be audited and scanned for vulnerabilities.
Pingback: Netherlands reverts to hand-counted votes to quell security fears • The Register – Packet Storm | Newsist
It is a pity the software is not used anymore. Otherwise I would have dared you to influence the election results…
You may know something about software, however youre assumptions are wrong in many ways, but you clearly do not know the processes and protocols which are used for counting our votes.
The Electoral Council still hasn’t answered many questions about the security of their, and the software your company wrote. They even can’t defend themselves against critics and prove otherwise. So that means my research is still standing strong so far. Just saying that I’m wrong and then give no evidence to support that claim doesn’t work.
Hi
Wat een onzinaanname dat software nooit veilig zou zijn. Vanuit juridisch perspectief is een bekend adagium “No taxation without representation” . Ik mag wel belasting betalen mer mijn Digid dus waarom niet stemmen?
Rop Gonggrijp heeft tien jaar al geleden aangetoond dat de overheid geen veilige stemcomputers gebruikte. Er is sindsdien niets veranderd en de overheid lijkt niet geleerd te hebben van dat debacle. De volgende EenVandaag reportage uit 2013 blijkt terug op 2007 toen de stemcomputers verband werden. Daarnaast heeft fraude met verkiezingsuitslagen een veel grotere impact dan als dit met DigiD gebeurt:
https://www.youtube.com/watch?v=j5INnI-jYSE
Pingback: Misleidende kop: ‘Met potlood stemmen onveilig’ – NieuwsCheckers
Pingback: Veille Cyber N115 – 06 février 2017 |
Pingback: How to hack the upcoming Dutch elections – and how hackers could have hacked all Dutch elections since 2009 | La cybercriminalité
Pingback: Política y hackers | Notas de clase de seguridad informática
Pingback: Cuando la ciberseguridad se convierte en una cuestión de Estado
Pingback: When cyber-security becomes an affair of state
Pingback: When cyber-security becomes an affair of state - InfoSecHotSpot
Pingback: When cyber-security becomes an affair of state | Extol Corporation Sdn Bhd | IT Security News
Pingback: When cyber-security becomes an affair of state | 007 Software
Dear Sijmen, it is good that you had a critical note on the software used for counting our votes. Now it has been investigated and thought to be safe when using in strict conditions. https://www.rijksoverheid.nl/ministeries/ministerie-van-binnenlandse-zaken-en-koninkrijksrelaties/nieuws/2017/03/03/berekenen-van-de-uitslag-van-de-komende-verkiezing
I would like to dare you to influence the outcome of the election results 🙂
Thx, Pieter
I’ve read the Fox-IT report and if *all* Fox-IT recommendations are followed, then it will be hard to tamper with the election results, as paper is effectively in the lead. I hope, but doubt that all recommendations will be followed. To be continued! 😉
Pingback: 担心投票系统被黑,详解荷兰政府为何决定在大选中使用手工计票 – 安全知识资讯快报
Pingback: 担心投票系统被黑,详解荷兰政府为何决定在大选中使用手工计票 – Terry & CoCo
Pingback: older: Dutch election can be stolen https://sijmen.ruwhof.net/weblo… | Dr. Roy Schestowitz (罗伊)
Pingback: Elektronisch stemmen: Gaat het er ooit nog van komen? - c't magazine
Pingback: Stimmenzählung in den Niederlanden: Lieber mit Taschenrechner – Avada Classic
Thank you for this report. You can add the site http://www.spiegel.de to the list of those that are linking to this article.
Although most of the article appears to be accurate, you should fix the statement that encryption protects data from being tampered with. Encryption only protects confidentiality; the integrity (or authenticity) of the data can only be protected using MACs or digital signatures, respectively.
Keep up the good work!
Hi!
Thanks for the link! I’ve added Der Spiegel to the link list.
I agree on your encryption and integrity statement. It’s indeed not mentioned clearly in the article. They should indeed implement digital signatures and proper public key infrastructure.